AD domain with unsecure ESX authentication bypass
Cayosoft Threat Definition CTD-000141
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
VMware ESXi contains an authentication bypass vulnerability. A threat actor with sufficient Active Directory (AD) permissions can gain full access to an ESXi host that uses AD for user management by re-creating the configured AD group (such as “ESX Admins”) after it was deleted from AD.
- Severity: High
- Platform: Active Directory
- Category: VMware Hypervisor ESXi, Infrastructure, Privileged Access Management
- MITRE ATT&CK Tactics: Persistence, Privilege Escalation
- MITRE D3FEND Tactics: System Configuration Permissions
Description
VMware ESXi contains an authentication bypass vulnerability.
A threat actor with sufficient Active Directory (AD) permissions can gain full access to an ESXi host that was previously configured to use AD for user management by re-creating the configured AD group (“ESX Admins” by default) after it was deleted from AD.

Real-World Scenario
An attacker gains delegated rights in Active Directory that allow creating and managing security groups but not direct access to VMware ESXi. The virtualization team previously removed the ESX Admins group from AD, assuming this would sever AD-based administrative access to ESXi. The attacker quietly re-creates an AD group with the same name and adds a compromised user account to it. Because the ESXi host still trusts that AD group name for administrative access, the attacker now obtains full ESXi host permissions without changing any ESXi configuration. The attacker can create snapshots, exfiltrate virtual machine disks, or tamper with domain controllers hosted on ESXi while blending into normal AD group administration activity. Cayosoft Guardian would detect the suspicious recreation of the ESX Admins group and raise a CTD-000141 alert before the attacker can fully exploit the access.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
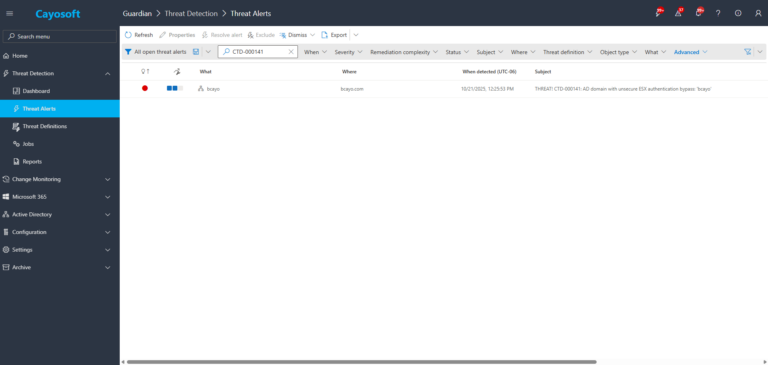
2.) View All Alerts and search for “CTD-000141” or “AD domain with unsecure ESX authentication bypass”.
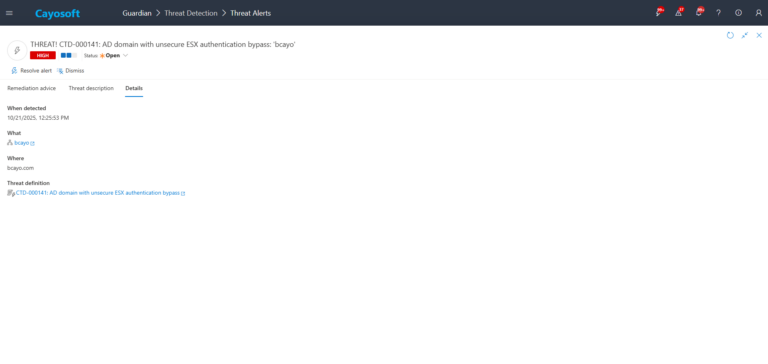
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Standard alert context, including: What (object name), Type, Where, When detected, Who, Severity, and Threat definition as shown in the alert message.
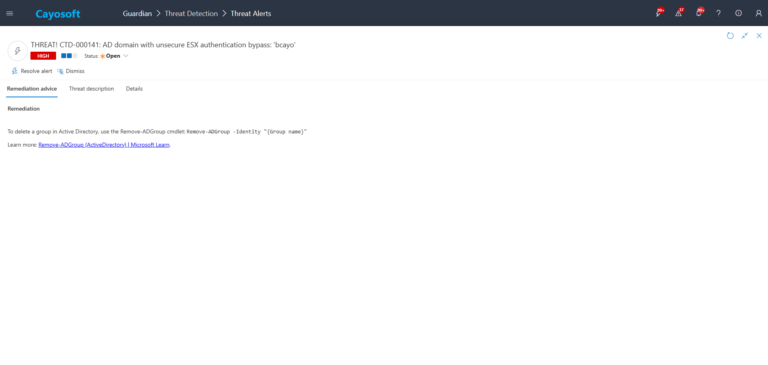
Remediation Steps
To delete a group in Active Directory, use the Remove-ADGroup cmdlet: Remove-ADGroup -Identity "{Group name}"
Learn more: Remove-ADGroup (ActiveDirectory) | Microsoft Learn.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD domain with unsecure ESX authentication bypass. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for misconfigurations and risky changes, providing early warning before attackers can exploit them.
To reduce the risk of AD domain with unsecure ESX authentication bypass:
- Restrict who can create, modify, or delete privileged AD groups related to ESXi administration.
- Regularly review and harden ESXi authentication settings, including the mapping of AD groups to ESXi roles.
- Use Cayosoft Guardian policies to monitor for the creation or recreation of privileged AD groups and unusual group membership changes.
- Coordinate change control between the AD and VMware teams so that ESXi trust relationships are updated whenever AD groups are decommissioned or renamed.
FAQ
It refers to a VMware ESXi vulnerability where an attacker can regain full ESXi administrative access simply by re-creating an AD group (typically “ESX Admins”) that ESXi previously trusted, even if that group had been deleted.
Because ESXi continues to trust the AD group name, an attacker with permissions to create AD groups can silently escalate to ESXi admin without touching ESXi configuration. This gives them the ability to control VMs, extract disks, or compromise domain controllers.
They require delegated rights that allow creating security groups—and potentially adding members. They do not need ESXi access or high-privilege AD rights, making the attack feasible from mid-tier AD compromise.
Yes. Native AD auditing and VMware ESXi logs provide basic visibility, and Cayosoft Guardian Protector offers free assessment capabilities that highlight risky AD group creations relevant to this bypass scenario.
Yes. Cayosoft Guardian provides continuous monitoring for privileged AD group creation, correlates it with ESXi trust mappings, raises CTD-000141 alerts, and offers prescriptive remediation and rollback for AD changes that enable this bypass.
References
- Microsoft Learn – Remove-ADGroup (ActiveDirectory) PowerShell cmdlet: https://learn.microsoft.com/en-us/powershell/module/activedirectory/remove-adgroup?view=windowsserver2022-ps#example-1-remove-a-group-by-name
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain with unsecure ESX authentication bypass, you reduce attack surfaces and strengthen your organization’s overall security posture.