AD domain with non-default permissions on krbtgt account
Cayosoft Threat Definition CTD-000087
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Non-default permissions on the KRBTGT account may allow attackers to forge Kerberos authentication tickets, enabling them to impersonate any user, access any resource, and remain undetected for extended periods.
- Severity: Critical
- Platform: Active Directory
- Category: Account protection, Kerberos, Domain-wide
- MITRE ATT&CK Tactics: Persistence, Privilege Escalation, Defense Evasion, Credential Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
A threat actor with permission to modify the KRBTGT account can compromise it. Using the KRBTGT account, they can create a Kerberos ticket-granting ticket (TGT) that provides authorization to any resource and set the ticket expiration to any arbitrary time. This forged TGT, known as a Golden Ticket, grants attackers unrestricted access and persistence in the network.

Real-World Scenario
An attacker gains administrative access to a single domain controller through a misconfigured privileged account. They discover that the KRBTGT account has non-default permissions, allowing them to modify it. Using this access, they generate a Golden Ticket granting domain-wide administrative rights that bypass password changes and standard Kerberos expiration times. For months, they can log in as any user, access sensitive data, and evade detection. Cayosoft Guardian could have detected the altered KRBTGT permissions and alerted security teams before the attack escalated.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
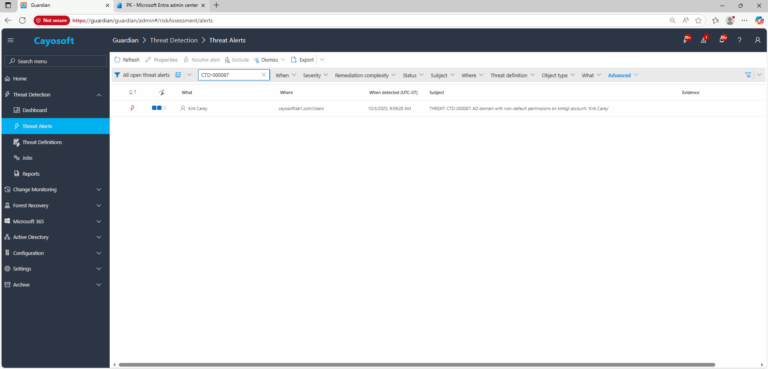
2.) View All Alerts and search for CTD-000087 or AD domain with non-default permissions on krbtgt account.
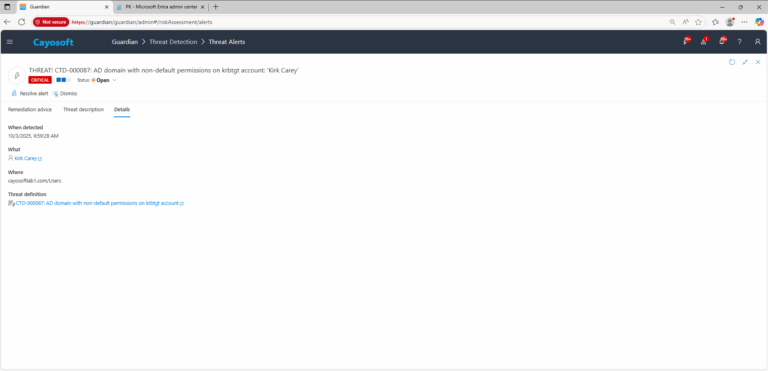
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review the alert for evidence of non-default security permissions applied to the KRBTGT account.
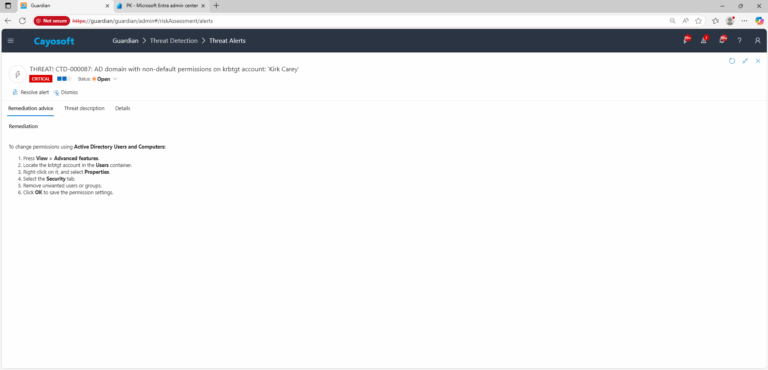
Remediation Steps
To change permissions using Active Directory Users and Computers:
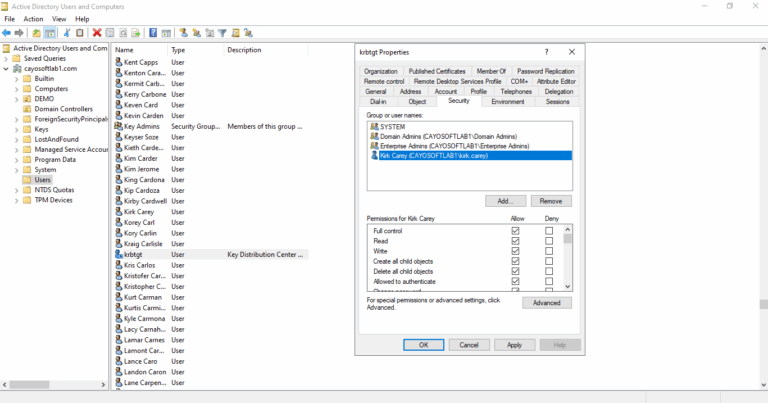
- ) Press View > Advanced features.
- ) Locate the krbtgt account in the Users container.
- ) Right-click on it, and select Properties.
- ) Select the Security tab.
- ) Remove unwanted users or groups.
- ) Click OK to save the permission settings.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on non-default permissions on the KRBTGT account. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
It is a built-in service account used by the Kerberos Key Distribution Center (KDC). The KRBTGT account encrypts and signs all Kerberos ticket-granting tickets (TGTs) within a domain.
If compromised, attackers can generate forged TGTs (Golden Tickets), impersonating any user or service in the domain, including domain administrators, with no expiration limits.
Any additional permissions may allow unauthorized users or groups to modify the KRBTGT account. That enables attackers to control Kerberos ticketing and escalate privileges stealthily.
References
- Kerberos KRBTGT account overview – Microsoft
- Golden Ticket attack details – Microsoft Security Blog
Final Thought
The KRBTGT account is one of the most sensitive objects in Active Directory. Protecting it with default, restrictive permissions is critical to preventing catastrophic and long-lasting domain compromise.