AD domain with misconfigured UNC paths policies
Cayosoft Threat Definition CTD-000192
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Domain Controllers host the SYSVOL and NETLOGON shared folders via SMB, which are critical for distributing Group Policy and logon scripts. When an AD domain has misconfigured UNC paths policies and Hardened UNC Paths are not enforced, these shares become vulnerable to NTLM relay, man-in-the-middle, and SMB downgrade attacks. The misconfiguration can allow attackers to steal credentials, impersonate domain controllers, or push malicious Group Policy across the forest.
- Severity: High
- Platform: Active Directory
- Category: Forest-wide, Infrastructure
- MITRE ATT&CK Tactics: Initial Access, Privilege Escalation, Defense Evasion, Credential Access, Lateral Movement
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
Domain Controllers (DCs) host the SYSVOL and NETLOGON shared folders via SMB, which are critical for distributing Group Policy and logon scripts. If Hardened UNC Paths are not enforced on DCs, these shares become vulnerable to NTLM relay, man-in-the-middle, and SMB downgrade attacks.
Such attacks can enable adversaries to intercept or manipulate authentication traffic, steal user credentials, impersonate domain controllers, or distribute malicious Group Policy objects across the environment. An AD domain with misconfigured UNC paths policies therefore presents a high-impact entry point for both initial access and privileged lateral movement.

Real-World Scenario
In an AD domain with misconfigured UNC paths policies, a red team discovers that Hardened UNC Paths are not enforced for \\(Domain)\SYSVOL and \\(Domain)\NETLOGON. The attackers position a relay tool on a compromised workstation and capture NTLM authentication attempts to the NETLOGON share, relaying them to a domain controller. Using the relayed credentials, the attackers modify logon scripts and Group Policy in SYSVOL to deploy malicious payloads on all domain-joined machines while appearing as normal policy updates. The attackers then use the new footholds for lateral movement and privilege escalation, carefully blending into routine Group Policy activity to avoid obvious detection. Cayosoft Guardian would have raised CTD-000192 when the AD domain with misconfigured UNC paths policies was detected, giving administrators time to harden SYSVOL and NETLOGON before the weakness was exploited.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
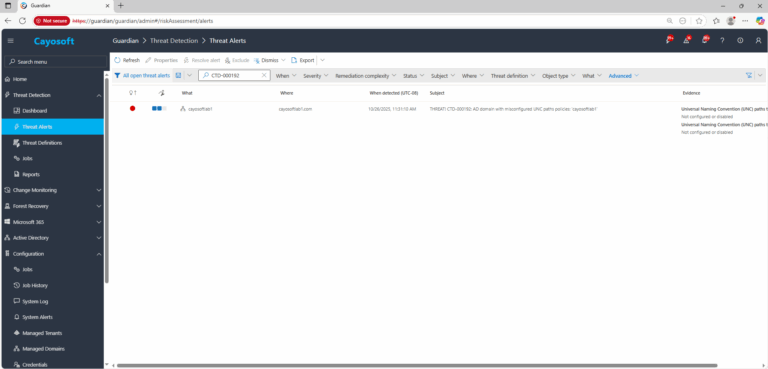
2.) Search for CTD-000192 or “AD domain with misconfigured UNC paths policies.”
3.) Open any alert and Click for details (from Raise Threat Alert action).
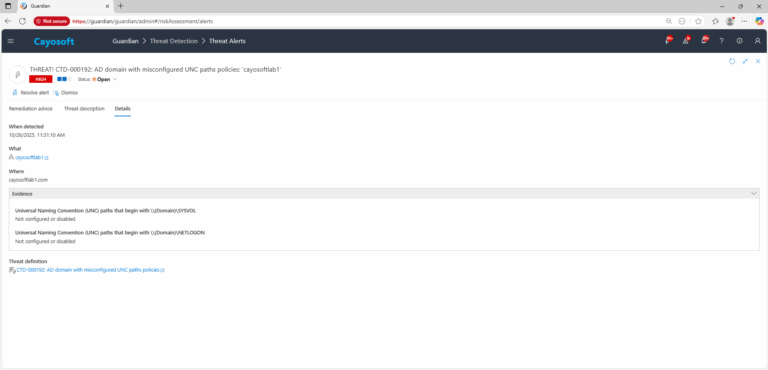
4.) Review the What, Where, Who, and When fields to identify the affected domain and domain controllers.
Evidence:
- Universal Naming Convention (UNC) paths that begin with \\(Domain)\SYSVOL – {TargetItem/uncSYSVOL}
Remediation Steps
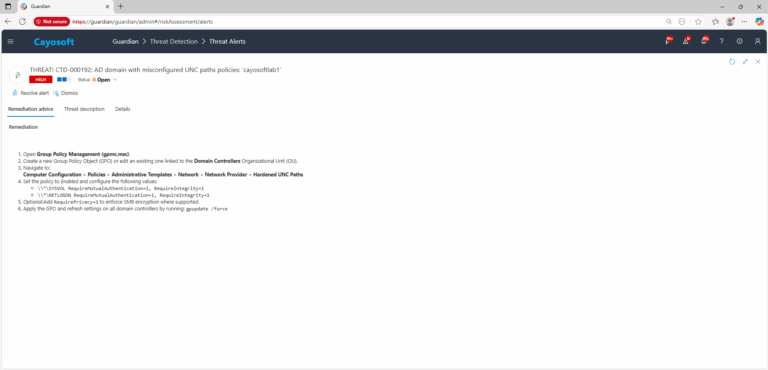
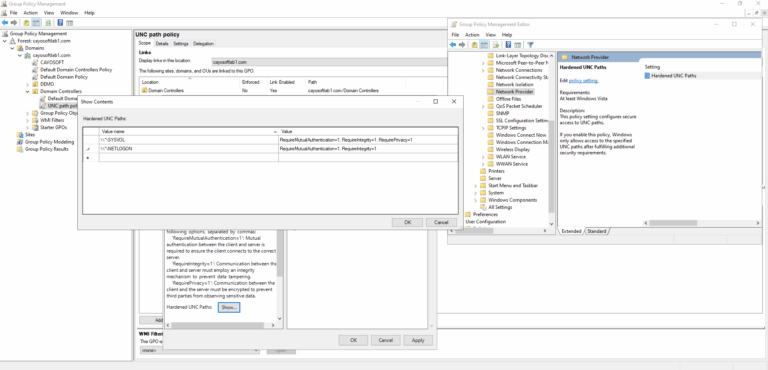
- ) Open Group Policy Management (gpmc.msc).
- ) Create a new Group Policy Object (GPO) or edit an existing one linked to the Domain Controllers Organizational Unit (OU).
- ) Navigate to:
Computer Configuration > Policies > Administrative Templates > Network > Network Provider > Hardened UNC Paths - ) Set the policy to Enabled and configure the following values:
\\*\SYSVOL RequireMutualAuthentication=1, RequireIntegrity=1\\*\NETLOGON RequireMutualAuthentication=1, RequireIntegrity=1
- ) Optional:Add
RequirePrivacy=1to enforce SMB encryption where supported. - ) Apply the GPO and refresh settings on all domain controllers by running:
gpupdate /force
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD domain with misconfigured UNC paths policies. Cayosoft Guardian continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for misconfigurations, providing early warning before attackers can exploit weaknesses such as unprotected SYSVOL and NETLOGON shares. Regularly reviewing and remediating CTD-000192 alerts ensures Hardened UNC Paths remain enforced and reduces opportunities for NTLM relay, man-in-the-middle, and SMB downgrade attacks.
FAQ
Misconfigured UNC paths leave SYSVOL and NETLOGON vulnerable to NTLM relay, man-in-the-middle, and SMB downgrade attacks, allowing attackers to intercept credentials or distribute malicious Group Policy across the environment.
Attackers can modify logon scripts or GPOs stored in SYSVOL and NETLOGON, causing malicious payloads to execute on many domain-joined systems, which accelerates lateral movement and escalates privileges quickly across the domain.
Yes. Legacy clients that lack support for mutual authentication or integrity checks may experience access failures, so administrators should test the settings in a pilot OU before broad deployment.
Yes, Cayosoft Guardian Protector.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain with misconfigured UNC paths policies, you reduce attack surfaces on critical domain controller shares and strengthen your organization’s overall security posture.