AD Domain with executable files in SYSVOL
Cayosoft Threat Definition CTD-000121
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Executable files in SYSVOL might pose a risk as these files might be infected. Because SYSVOL content is replicated and included in forest recovery backups, malicious executables stored there can persist across restores and silently reinfect a recovered environment.
- Severity: Low
- Platform: Active Directory
- Category: Infrastructure
- MITRE ATT&CK Tactics: Persistence
MITRE D3FEND Tactics: File Eviction
Description
Executable files in SYSVOL might pose a risk as these files might be infected. These infected files will be included in your backups for forest recovery and can transfer infection into a recovered forest.
CTD-000121 monitors the Active Directory domain for executable and script files (for example, .msi, .exe, .bat, .sh, .cmd, .psm1, .ps1) located in SYSVOL, where only Group Policy data and configuration files should normally reside.

Real-World Scenario
An attacker compromises a management workstation and drops a trojanized exe into a Group Policy script folder under SYSVOL. The executable is configured to run as part of a logon or startup script, giving the attacker long-term persistence on any computer that processes the GPO. Domain controllers replicate SYSVOL, so the malicious file spreads to all DCs and is captured in regular system state and forest recovery backups. Months later, when the organization performs a forest recovery, the same infected SYSVOL content is restored, reintroducing the malware into the rebuilt domain. Cayosoft Guardian detects executable files in SYSVOL early and raises CTD-000121 so administrators can evict the files before they are baked into backups or abused for persistence.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
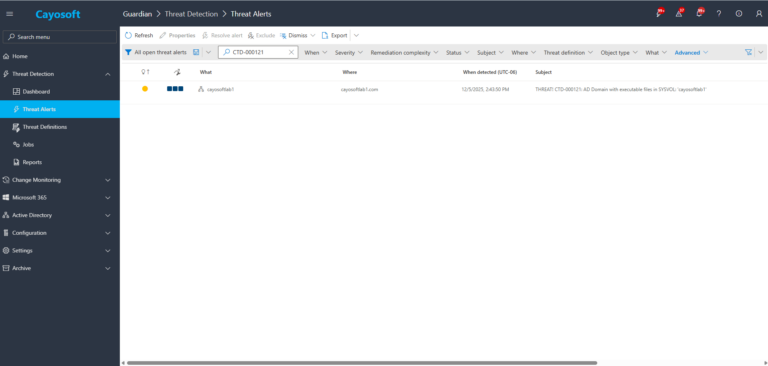
2.) Open Threats / Alerts and search for CTD-000121 or “AD Domain with executable files in SYSVOL”.
3.) Open any alert and Click for details (from Raise Threat Alert action).
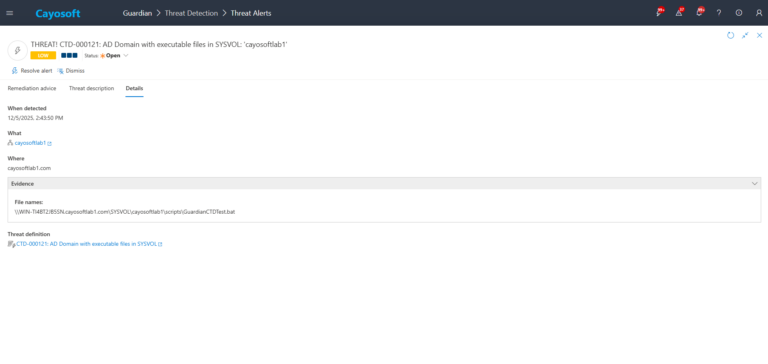
4.) Evidence:
- File names
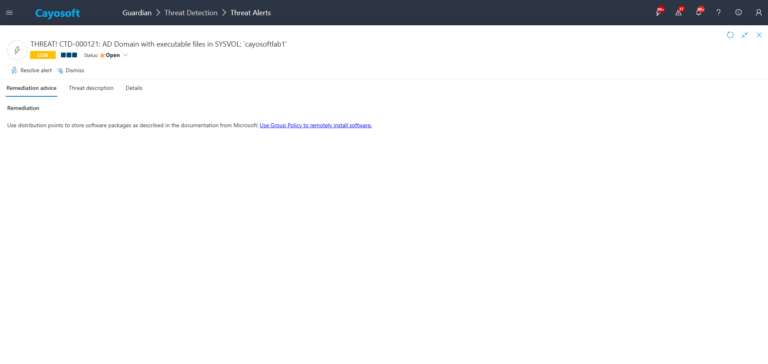
Remediation Steps
Use distribution points to store software packages as described in the documentation from Microsoft: Use Group Policy to remotely install software.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD Domain with executable files in SYSVOL. Cayosoft Guardian continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations and risky conditions, providing early warning before attackers can exploit persistence mechanisms tied to SYSVOL.
To further prevent recurrence:
- Do not use SYSVOL as a general software file share or package repository.
- Use dedicated distribution points and software shares for installers, as described in Microsoft’s Group Policy software deployment guidance.
- Restrict permissions on SYSVOL and GPO script folders to only required administrative accounts.
- Periodically scan SYSVOL for executable and script files and review any changes.
- Maintain regular reviews of Cayosoft Guardian alerts for CTD-000121 and follow up on any new detections.
FAQ
Executables in SYSVOL are replicated across all domain controllers, included in forest recovery backups, and can be executed through Group Policy, making them an ideal persistence mechanism for attackers.
While historically some organizations placed installers there, Microsoft does not recommend this practice. Installers should be stored on dedicated distribution points, not SYSVOL.
By placing malicious executables in SYSVOL, attackers can achieve long-term persistence because the files spread via replication, execute through GPO processing, and survive forest recovery.
Yes. Cayosoft Guardian Protector provides free detection and alerting for risky SYSVOL conditions, including unauthorized executable files that could be used for persistence.
Yes. Cayosoft Guardian offers continuous monitoring, alerting, full change auditing, and prescriptive remediation for CTD-000121 and more than 200 other AD, Entra ID, and Microsoft 365 misconfigurations.
References
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD Domain with executable files in SYSVOL, you reduce attack surfaces and strengthen your organization’s overall security posture.