AD Domain where Enterprise Key Admins group has full access to the domain
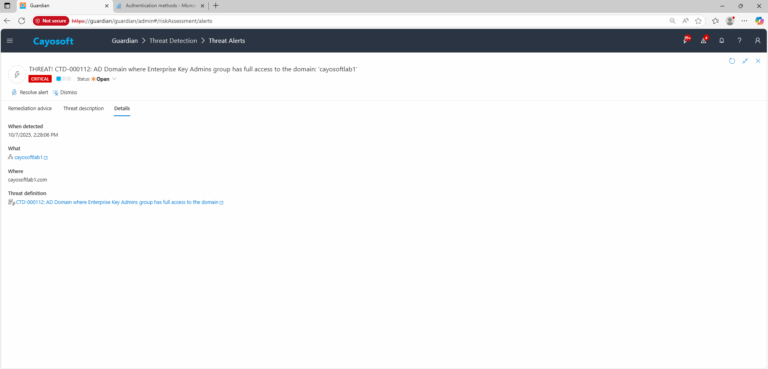
Cayosoft Threat Definition CTD-000112
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
In certain versions of Windows Server 2016, the Enterprise Key Admins group was unintentionally granted Full Control over the domain root, enabling dangerous replication permissions. This creates an exploitable path for attackers to harvest credentials and move laterally across the forest.
- Severity: Critical
- Platform: Active Directory
- Category: Forest-wide
- MITRE ATT&CK Tactics: Credential Access, Lateral Movement
- MITRE D3FEND Tactics: User Account Permissions
Description
Certain builds of Windows Server 2016 Adprep incorrectly grant Enterprise Key Admins the ability to replicate all changes from Active Directory, including password data, making DCSync attacks possible.
Unlike Enterprise Admins, which are protected by AdminSDHolder, the Enterprise Key Admins group is treated like a regular group, meaning:
- Account Operators may have Full Control over it by default.
- Inheritance is enabled, allowing OU admins to change its membership.
Without the protections afforded to Builtin Admins, Domain Admins, or Enterprise Admins, this group becomes a weaker target for attackers aiming to compromise the forest.

Real-World Scenario
An attacker gains access to a helpdesk account that belongs to the Account Operators group.
Due to the misconfiguration, this account has rights to modify membership of Enterprise Key Admins.
The attacker adds their controlled account, then uses DCSync to replicate domain password hashes, including those of Domain Admins.
With these hashes, they log in as privileged accounts and move laterally to other systems, eventually taking control of the forest.
Cayosoft Guardian would detect the excessive permissions and trigger an alert before the privilege escalation could occur.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
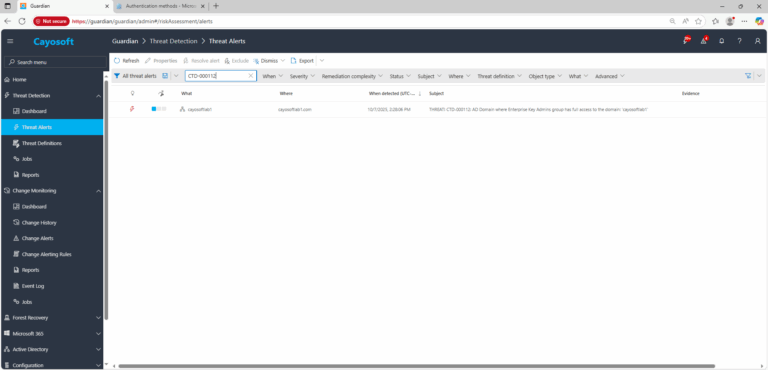
2.) Go to All Alerts and search for CTD-000112 or “Enterprise Key Admins group has full access”.
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review associated evidence fields to confirm excessive Full Control permissions on the domain object.
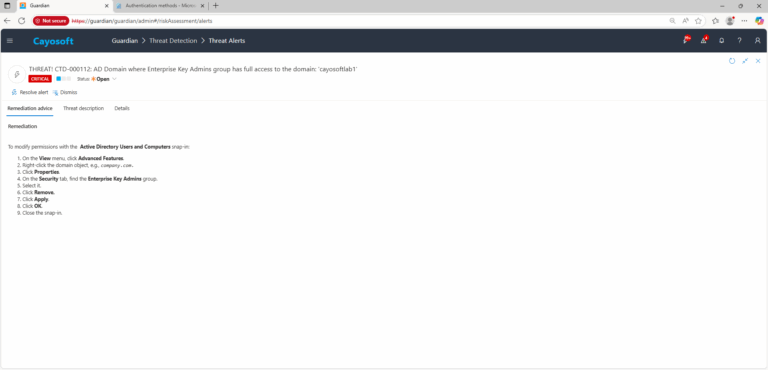
Remediation Steps
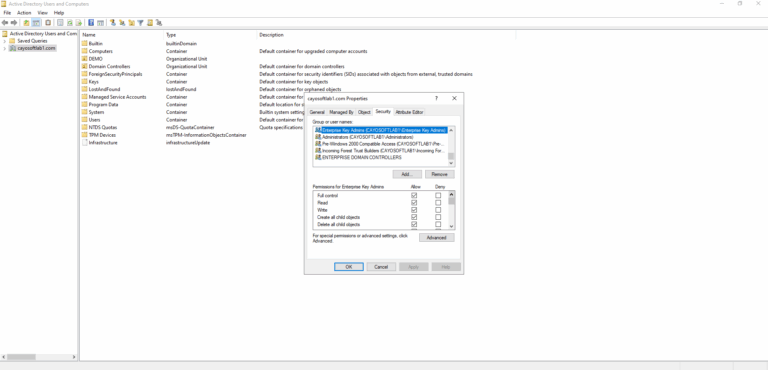
To modify permissions with the Active Directory Users and Computers snap-in:
- ) On the View menu, click Advanced Features.
- ) Right-click the domain object, e.g.,
company.com. - ) Click Properties.
- ) On the Security tab, find the Enterprise Key Admins group.
- ) Select it.
- ) Click Remove.
- ) Click Apply.
- ) Click OK.
- ) Close the snap-in.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on excessive Enterprise Key Admins permissions. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warnings before attackers can exploit them.
FAQ
In certain versions of Windows Server 2016, the Enterprise Key Admins group was mistakenly granted Full Control of the domain root, including replication permissions. This allows attackers to perform DCSync attacks, harvesting password hashes for privileged accounts. Unlike Enterprise Admins, which are protected by AdminSDHolder, Enterprise Key Admins are not, making them an easier and weaker target for privilege escalation.
Tools like Cayosoft Guardian can detect when Enterprise Key Admins have excessive permissions and generate an alert. To remediate, administrators should review domain object permissions in Active Directory Users and Computers (ADUC), remove Full Control rights from the Enterprise Key Admins group, and confirm the changes are applied. This action prevents attackers from exploiting replication rights.
Attackers who compromise accounts with indirect control, such as Account Operators, could add themselves to the Enterprise Key Admins group. With replication rights, they can perform a DCSync attack to obtain hashes of Domain Admin accounts. This allows them to log in as privileged users, move laterally, and eventually take over the forest, making this misconfiguration a critical security risk.
References
- Microsoft Docs – AdminSDHolder Protection
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Enterprise Key Admins excessive permissions, you reduce attack surfaces and strengthen your organization’s security posture.