AD domain controller deployed as a VM without drive encryption
Cayosoft Threat Definition CTD-000168
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Deploying Active Directory domain controllers as virtual machines without drive encryption exposes sensitive data at rest. Attackers who obtain VHD/VHDX files can extract credentials and AD secrets offline, enabling rapid privilege escalation with minimal on-host telemetry.
- Severity: High
- Platform: Active Directory
- Category: Infrastructure
- MITRE ATT&CK Tactics: Privilege Escalation, Defense Evasion
- MITRE D3FEND Tactics: D3-PH (Platform Hardening)
Description
Deploying a domain controller VM without disk encryption leaves VHD/VHDX files readable if storage is stolen, copied, or accessed by a malicious insider. An attacker can mount the images, extract NTDS.dit and SYSTEM hives, and recover password hashes, Kerberos keys, and other secrets. BitLocker with TPM (and appropriate protectors) mitigates this risk by protecting data at rest even if virtual disks are exfiltrated.

Real-World Scenario
A virtualization admin copies an unencrypted domain controller VHD from the hypervisor datastore for “backup.” A disgruntled contractor quietly takes the file and mounts it offline, extracting NTDS.dit and the SYSTEM hive to recover the krbtgt key. The attacker forges Golden Tickets and logs in as a domain admin days later, blending in with routine maintenance. Because the entire operation used offline files, traditional endpoint logging shows nothing unusual. Cayosoft Guardian would flag the AD domain controller deployed as a VM without drive encryption misconfiguration so the security team can encrypt the volumes before such an exfiltration occurs.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Open All Alerts and search for CTD-000168 or “AD domain controller deployed as a VM without drive encryption.”
3.) Open any alert and Click for details (from Raise Threat Alert action).
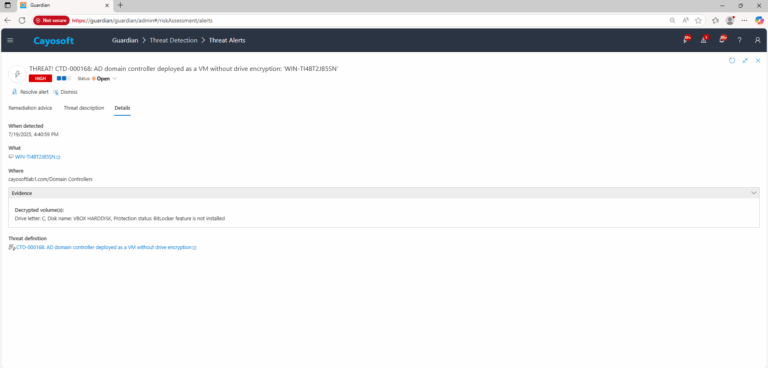
4.) Evidence:
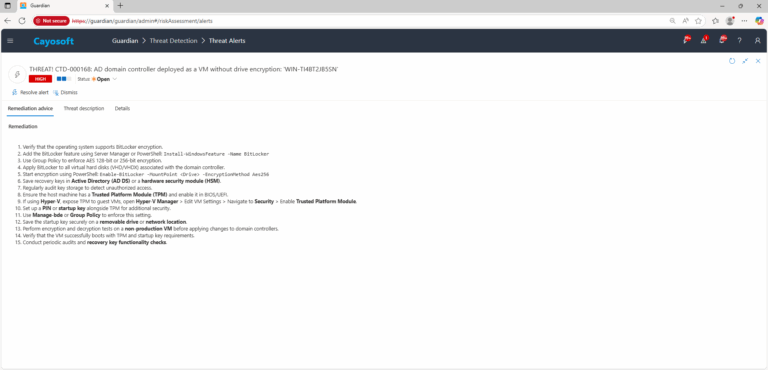
Remediation Steps
- ) Verify that the operating system supports BitLocker encryption.
- ) Add the BitLocker feature using Server Manager or PowerShell:
Install-WindowsFeature -Name BitLocker - ) Use Group Policy to enforce AES 128-bit or 256-bit encryption.
- ) Apply BitLocker to all virtual hard disks (VHD/VHDX) associated with the domain controller.
- ) Start encryption using PowerShell:
Enable-BitLocker -MountPoint <Drive> -EncryptionMethod Aes256 - ) Save recovery keys in Active Directory (AD DS) or a hardware security module (HSM).
- ) Regularly audit key storage to detect unauthorized access.
- ) Ensure the host machine has a Trusted Platform Module (TPM) and enable it in BIOS/UEFI.
- ) If using Hyper-V, expose TPM to guest VMs, open Hyper-V Manager > Edit VM Settings > Navigate to Security > Enable Trusted Platform Module.
- ) Set up a PIN or startup key alongside TPM for additional security.
- ) Use Manage-bde or Group Policy to enforce this setting.
- ) Save the startup key securely on a removable drive or network location.
- ) Perform encryption and decryption tests on a non-production VM before applying changes to domain controllers.
- ) Verify that the VM successfully boots with TPM and startup key requirements.
- ) Conduct periodic audits and recovery key functionality checks.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD domain controller deployed as a VM without drive encryption. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Without drive encryption, virtual hard disk files (VHD/VHDX) are readable if stolen or copied. Attackers can mount them offline, extract NTDS.dit and SYSTEM hives, and recover password hashes and Kerberos keys. This enables Golden Ticket attacks, credential theft, and full domain compromise—all without generating on-host telemetry.
Cayosoft Guardian can raise CTD-000168 alerts when a DC VM lacks encrypted volumes. In the dashboard, review alert details for “Decrypted volume(s)” evidence to confirm which drives are unprotected. Routine audits should also verify that BitLocker with TPM or vTPM is enabled on all domain controller VMs.
Enable BitLocker with TPM (or vTPM) on all DC VM volumes (OS, NTDS.dit, SYSVOL, AD logs, and attached VHDs). Escrow recovery keys securely (AD DS or HSM), enforce encryption policies through Group Policy, and audit recovery key access regularly. Going forward, configure policies to ensure all new domain controller VMs are encrypted before production deployment.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain controller deployed as a VM without drive encryption, you reduce attack surfaces and strengthen your organization’s overall security posture.