AD domain allowing multicast name resolution (LLMNR)
Cayosoft Threat Definition CTD-000165
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Multicast Name Resolution (LLMNR) is a legacy protocol for name resolution in networks without DNS servers.
- Severity: Medium
- Platform: Active Directory
- Category: Infrastructure
- MITRE ATT&CK Tactics: Credential Access, Discovery, Lateral Movement
- MITRE D3FEND Tactics: D3-ACH (Application Configuration Hardening)
Description
Multicast Name Resolution (LLMNR) is a legacy protocol for name resolution in networks without DNS servers. In an Active Directory domain, LLMNR can expose the environment to spoofing and credential-harvesting attacks, such as responder attacks. Attackers can intercept and manipulate LLMNR requests to gain user credentials or redirect traffic.
Disabling LLMNR mitigates these risks by preventing unauthorized interception of name resolution requests. However, this change may impact legacy applications or older systems that rely on LLMNR or NetBIOS for network communication.

Real-World Scenario
A user mistypes a fileserver name on a Wi-Fi network. Because LLMNR is allowed, the workstation multicasts a query that an attacker’s Responder host answers, tricking the client to authenticate and leak NTLM challenge/response material. The attacker cracks a weak hash offline, reuses the credentials to access a jump server, and pivots laterally using SMB. To avoid obvious detection, the attacker throttles traffic and operates during maintenance windows. Cayosoft Guardian flags CTD-000165: AD domain allowing multicast name resolution (LLMNR) so administrators can enforce the GPO and disable LLMNR before credentials are harvested.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
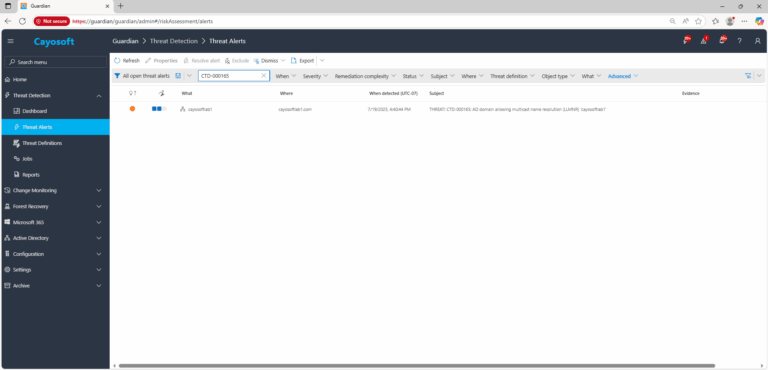
2.) Open All Alerts and search for CTD-000165 or AD domain allowing multicast name resolution (LLMNR).
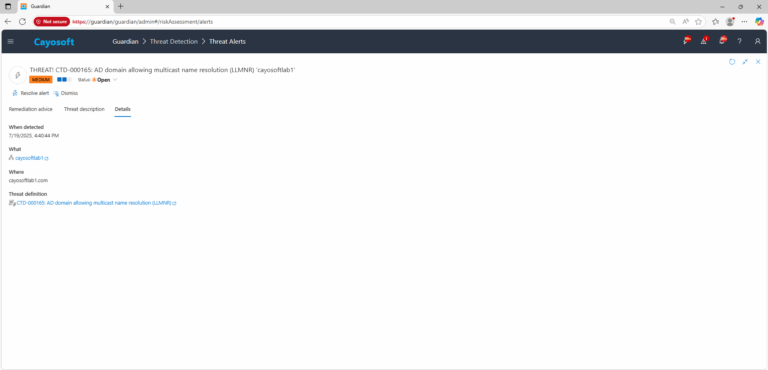
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review alert context (What/Type/Where/When/Who/Severity/Threat definition) to confirm LLMNR is permitted in the domain.
Evidence: No explicit evidence fields defined for this template.
Remediation Steps
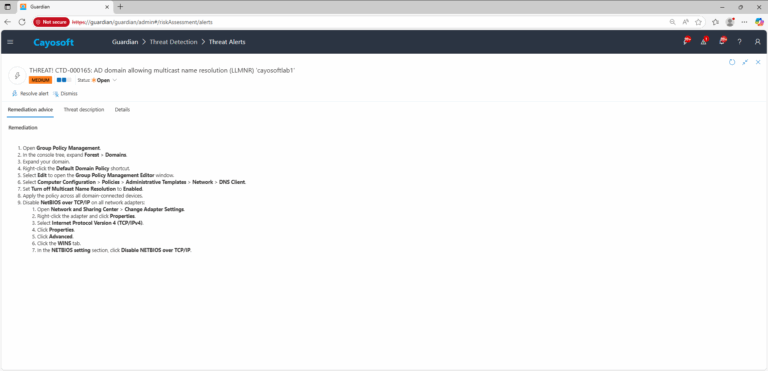
- ) Open Group Policy Management.
- ) In the console tree, expand Forest > Domains.
- ) Expand your domain.
- ) Right-click the Default Domain Policy shortcut.
- ) Select Edit to open the Group Policy Management Editor window.
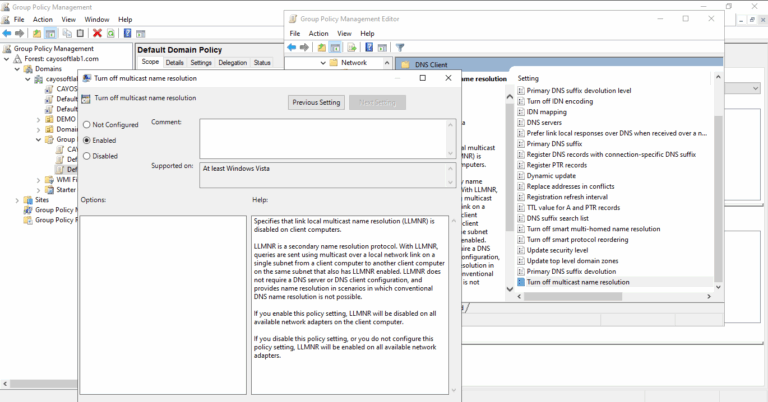
- ) Select Computer Configuration > Policies > Administrative Templates > Network > DNS Client.
- ) Set Turn off Multicast Name Resolution to Enabled.
- ) Apply the policy across all domain-connected devices.
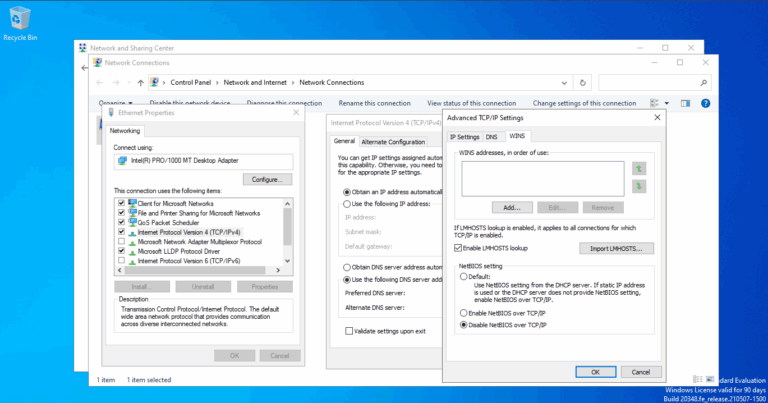
- ) Disable NetBIOS over TCP/IP on all network adapters:
- ) Open Network and Sharing Center > Change Adapter Settings.
- ) Right-click the adapter and click Properties.
- ) Select Internet Protocol Version 4 (TCP/IPv4).
- ) Click Properties.
- ) Click Advanced.
- ) Click the WINS tab.
- ) In the NETBIOS setting section, click Disable NETBIOS over TCP/IP.
FAQ
LLMNR allows systems to multicast name queries, which attackers can spoof. By responding to these queries with malicious answers, attackers can capture NTLM credentials, perform offline cracking, and reuse compromised accounts for lateral movement.
The most common is a Responder attack, where an attacker tricks clients into sending authentication attempts to their rogue machine. This can expose NTLM challenge/response pairs and lead to credential theft and unauthorized access.
In modern Active Directory environments with DNS, disabling LLMNR typically causes no issues. However, some legacy applications or older systems that relied on LLMNR or NetBIOS may break until they are updated to use DNS.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain controller deployed as a VM without drive encryption, you reduce attack surfaces and strengthen your organization’s overall security posture.