AD domain accounts with password not required
Cayosoft Threat Definition CTD-000053
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Accounts with Password not required (msDS-UserPasswordNotRequired=TRUE) can authenticate without a password or with an empty/blank password, creating a direct path for unauthorized access.
- Severity: Medium
- Platform: Active Directory
- Category: Account Protection
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Domain Account Monitoring, Application Configuration Hardening, Strong Password Policy
Description
The msDS-UserPasswordNotRequired attribute indicates whether a user must have a password to sign in. When set to TRUE, a threat actor may leverage the account to access your environment without meeting password requirements, increasing the likelihood of compromise and lateral movement.

Real-World Scenario
During an audit, a legacy import process accidentally sets Password not required on a batch of test users that were later granted file-share access. An attacker enumerates AD, finds the misconfigured accounts, and logs in with blank passwords to stage data theft and password-spray attempts from trusted endpoints. Cayosoft Guardian would detect CTD-000053 and list affected users so the team can immediately enforce password requirements and review any activity tied to these identities.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
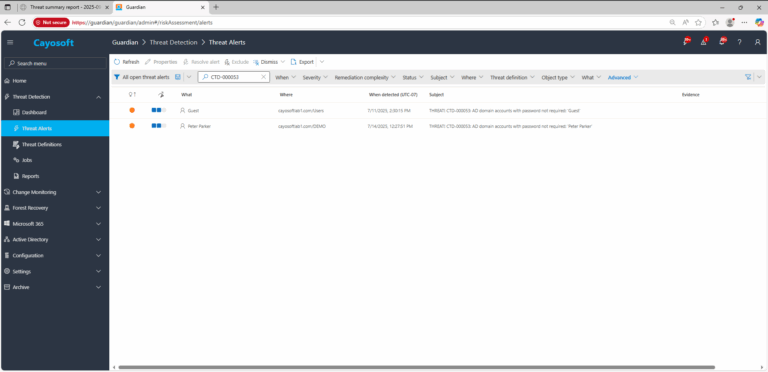
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) View All Alerts and search for CTD-000053 or AD domain accounts with password not required.
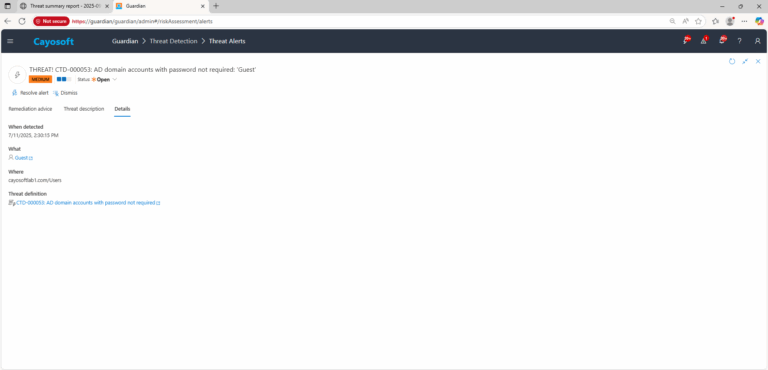
3.) Open any alert and Click for details (from Raise Threat Alert action).
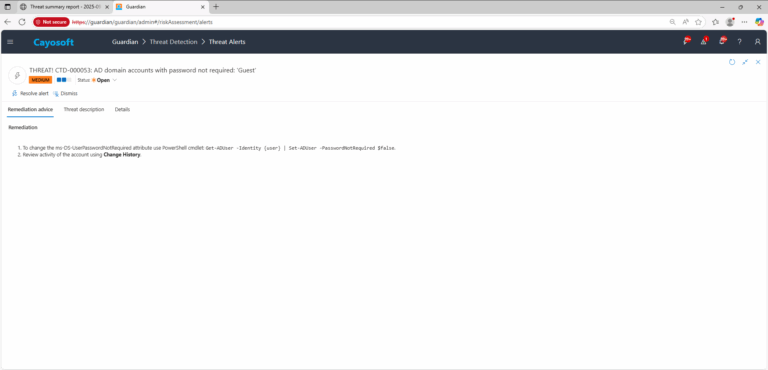
Remediation Steps
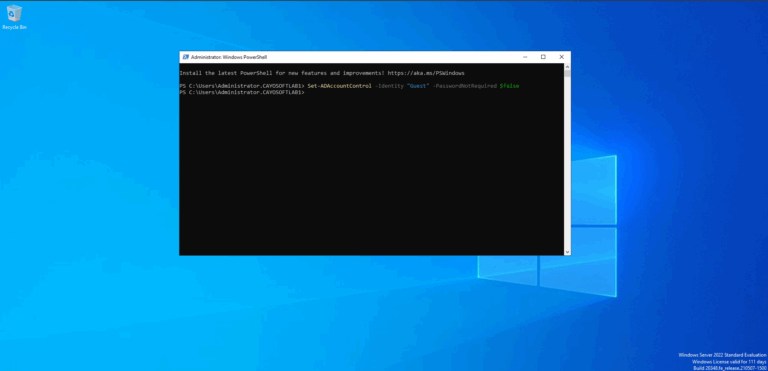
- To change the ms-DS-UserPasswordNotRequired attribute use PowerShell cmdlet: Set-ADAccountControl -Identity “Guest” -PasswordNotRequired $false
- Review activity of the account using Change History.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD domain accounts with password not required. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
When the msDS-UserPasswordNotRequired attribute is set to TRUE, the account can potentially authenticate with a blank or empty password. This makes AD Domain Accounts with Password Not Required a direct security threat, as attackers may gain unauthorized access and move laterally across the environment.
The most effective method is to use monitoring tools such as Cayosoft Guardian, which will detect and alert on these misconfigured accounts. Once identified, administrators should enforce password requirements, rotate affected credentials, and review activity logs for signs of suspicious behavior.
Yes. Even disabled accounts remain a risk because the misconfiguration persists if they are later enabled. Service accounts should never bypass password requirements; instead, organizations should use managed solutions like Group Managed Service Accounts (gMSA) or managed identities to ensure strong authentication.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain accounts with password not required, you reduce attack surfaces and strengthen your organization’s overall security posture.