AD domain account with password stored using reversible encryption
Cayosoft Threat Definition CTD-000055
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Storing encrypted passwords in a reversible way means the encryption can be undone; if a threat actor obtains the stored value, the attacker can recover the clear-text password and sign in with the compromised account.
- Severity: Medium
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Domain Account Monitoring
Description
Storing passwords with reversible encryption allows decryption of those values. If the reversible form is accessed or the encryption is broken, an attacker can obtain the clear-text password and authenticate as the user or service account. This option should remain disabled unless an application’s requirement clearly outweighs the security risk.

Real-World Scenario
A developer enables Store password using reversible encryption for a service account to satisfy an old IIS digest-auth integration. Months later, an attacker with read access to AD data dumps user attributes from a backup and extracts the reversible password for that account. Using the recovered clear-text, the attacker signs in to multiple application servers, plants web shells, and pivots laterally using scheduled tasks to avoid obvious sign-in anomalies. Operations are disrupted and sensitive data is exfiltrated under the service account’s identity. Cayosoft Guardian would highlight CTD-000055 across domains so the team could remove the setting and rotate credentials before abuse.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
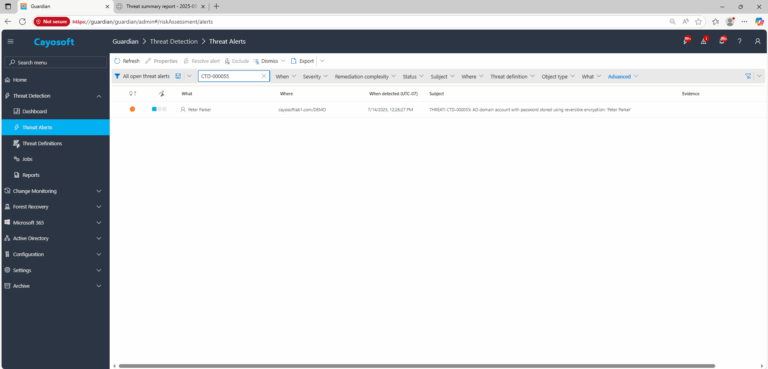
2.) Open All Alerts and search for CTD-000055 or AD domain account with password stored using reversible encryption.
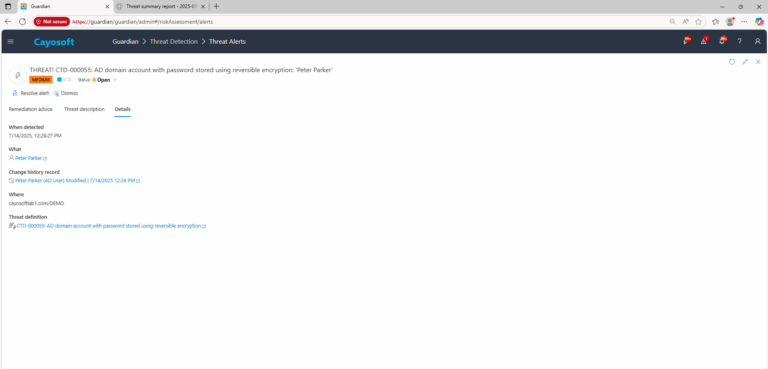
3.) Open any alert and Click for details (from Raise Threat Alert action).
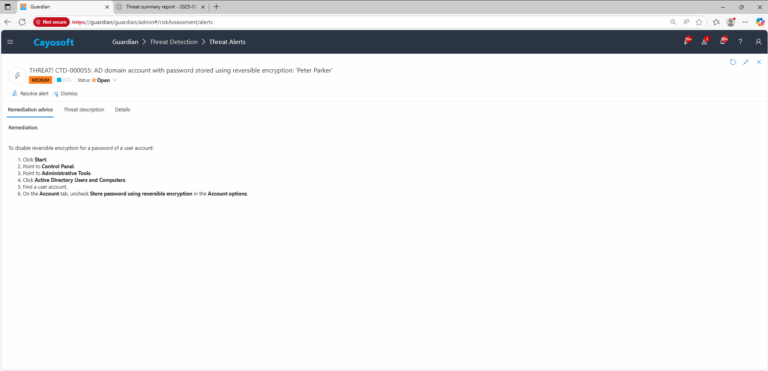
Remediation Steps
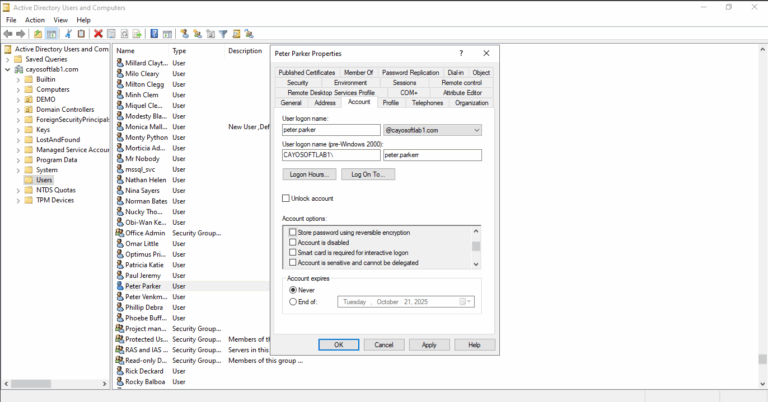
To disable reversible encryption for a password of a user account:
- ) Click Start.
- ) Point to Control Panel.
- ) Point to Administrative Tools.
- ) Click Active Directory Users and Computers.
- ) Find a user account.
- ) On the Account tab, uncheck Store password using reversible encryption in the Account options.
How to Prevent It
- Use Cayosoft Guardian to continuously detect accounts with reversible password encryption across domains.
- Keep Store password using reversible encryption disabled in domain password policy and in account templates.
- Upgrade or reconfigure legacy apps (e.g., IIS Digest/CHAP-based auth) to use modern methods that do not require reversible passwords.
- Regularly audit userAccountControl for the 0x80 flag and remove it where found.
- Enforce strong password policies and rotate service account credentials on change.
FAQ
This method is essentially equivalent to storing passwords in clear text because the value can be decrypted. If an attacker gains access to an AD dump or backups, they can recover the password and use it directly for authentication.
This usually stems from legacy applications or protocols such as IIS Digest Authentication, CHAP, or older RADIUS solutions. Administrators sometimes enable the option for compatibility, overlooking the severe security downgrade it introduces.
Applications should be modernized or replaced whenever possible. If temporary support is unavoidable, the affected service accounts must be isolated, enforced with multi-factor authentication, restricted to specific systems only, and tightly monitored through event logs.
Final Thought
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain account with password stored using reversible encryption, you reduce attack surfaces and strengthen your organization’s overall security posture.