Active Directory Dangerous ACLs Expose DFSR Settings Objects of the SYSVOL Share
Cayosoft Threat Definition CTD-000147
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Dangerous Access Control Lists (ACLs) on Distributed File System Replication (DFSR) settings objects can allow attackers to alter SYSVOL replication settings, enabling unauthorized Group Policy changes to propagate across all domain controllers.
- Severity: Critical
- Platform: Active Directory
- Category: Forest-wide, Infrastructure
- MITRE ATT&CK Tactics: Persistence, Privilege Escalation, Lateral Movement
- MITRE D3FEND Tactics: Domain Account Monitoring
Description
DFSR settings under the DFSR-GlobalSettings container control SYSVOL replication, which carries Group Policy Objects (GPOs) and other domain-critical files. Misconfigured permissions here allow attackers to modify replication topology, partners, or schedules, potentially inserting malicious GPOs or altering existing ones. This creates a powerful mechanism for persistence, privilege escalation, and lateral movement in an Active Directory forest.

Real-World Scenario
An attacker compromises an account with excessive rights on DFSR-GlobalSettings. They modify replication settings to introduce a rogue domain controller or tamper with GPOs that control security settings and login scripts. These malicious GPOs then replicate to all domain controllers, granting the attacker persistent privileged access and the ability to execute code across the enterprise without direct interaction with each system. Cayosoft Guardian detects these dangerous ACL changes before malicious replication can take place.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
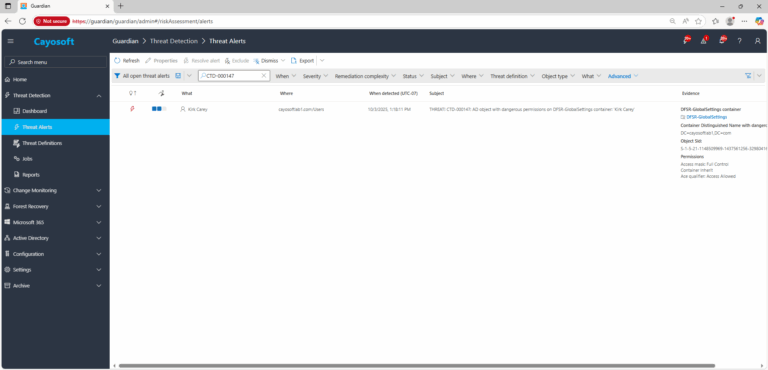
2.) View All Alerts and search for CTD-000147 or Active Directory Dangerous ACLs expose DFSR settings objects of the SYSVOL share.
3.) Open any alert and Click for details (from Raise Threat Alert action).
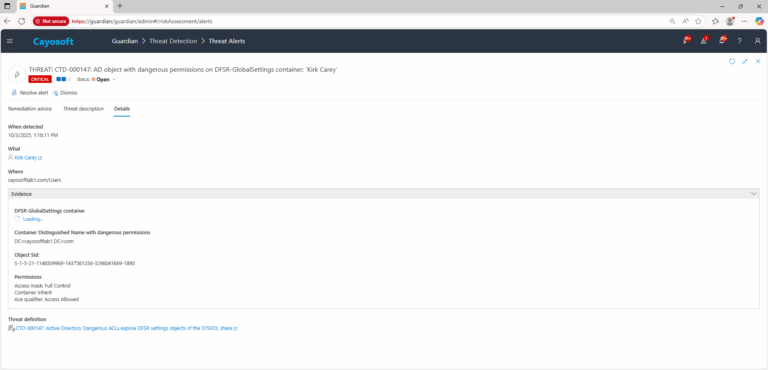
4.) Review Evidence:
- DFSR-GlobalSettings container
- Container Distinguished Name with dangerous permissions
- Object SID
- Permissions
Remediation Steps
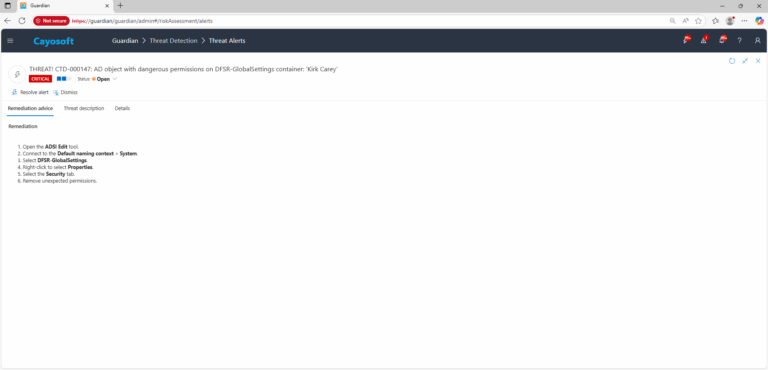
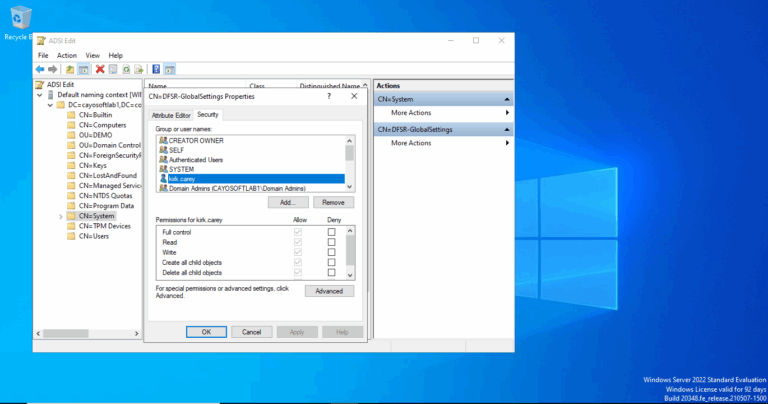
- ) Open the ADSI Edit tool.
- ) Connect to the Default naming context > System.
- ) Select DFSR-GlobalSettings.
- ) Right-click to select Properties.
- ) Select the Security tab.
- ) Remove unexpected permissions.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on dangerous ACLs on DFSR settings objects. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
It warns that dangerous ACLs on DFSR-GlobalSettings objects can let attackers modify SYSVOL replication settings, leading to unauthorized Group Policy propagation and potential domain-wide compromise.
Active Directory administrators and security teams should regularly review and secure permissions on DFSR-GlobalSettings to prevent attackers from manipulating replication or Group Policy Objects.
They can use continuous monitoring tools like Cayosoft Guardian to detect dangerous ACL changes early and apply strict permission controls to safeguard SYSVOL replication integrity.
References
- Microsoft – DFSR Overview
Final Thought
Securing SYSVOL replication settings is critical to maintaining the integrity of Group Policy. By locking down DFSR-GlobalSettings permissions, you prevent attackers from injecting malicious policies that can silently take control of your environment.