AD Domain Controller Not Changing Its Password
Cayosoft Threat Definition CTD-000136
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A domain controller that has not updated its computer account password in over 45 days may have outdated security credentials, increasing the risk of compromise. Domain controllers are expected to change their passwords every 30 days by default. Failure to do so could indicate misconfiguration or tampering.
- Severity: Critical
- Platform: Active Directory
- Category: Infrastructure
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND: Reissue Credential
Description
Some domain controllers have not updated their passwords in over 45 days, suggesting that their security credentials may be outdated. Domain controllers are typically configured to change their passwords automatically every 30 days. Therefore, it is crucial to ensure that domain controller passwords are updated regularly to maintain security. Investigating why the automatic password change is not occurring is important, as it could indicate a potential security issue. Regular password updates help protect against breaches and ensure the ongoing security of your network.

Real-World Scenario
An attacker gains a foothold in an environment and compromises a domain controller’s cached credentials. Because the DC has not updated its computer account password for several months, the attacker can continue to authenticate and maintain persistence without detection. This stale credential allows them to extract Kerberos tickets, create golden tickets, and access sensitive data without triggering password change policies. Cayosoft Guardian could have detected the stale DC password early, allowing security teams to reset it before the attacker leveraged it for long-term domain compromise.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
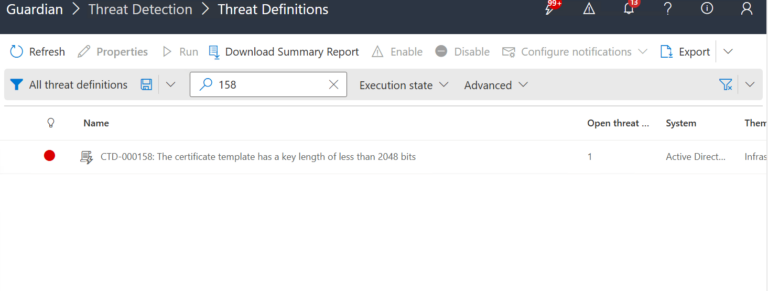
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) View All Alerts and search for CTD-000136 or AD domain controller not changing its password.
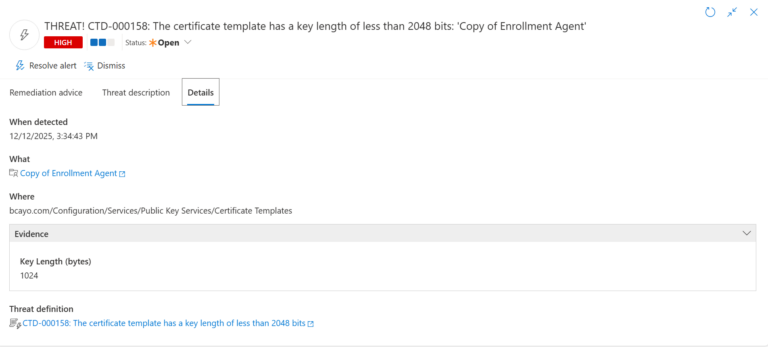
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- Password last set
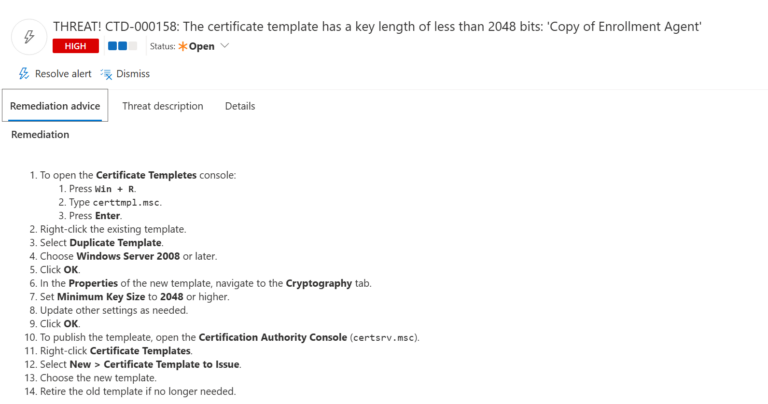
Remediation Steps
To reset the computer account password of the domain controller:
- ) At a command prompt, type the netdom help resetpwd command, and then press Enter.
- ) After you press Enter, you will be prompted to enter the password associated with the domain user. Even though you may not see any typed characters, you need to type the password and press Enter.
- ) Use the syntax that this command provides for using the Netdom command-line tool to reset the computer account password, for example: netdom resetpwd /server:<domain controller name> /userD:administrator /passwordd:*, where the domain controller name is the local DC that you’re recovering.
Note: You should run this command twice.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD domain controllers that are not changing their passwords as expected. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
A domain controller relies on its computer account password to securely authenticate within Active Directory. If this password is not changed regularly, attackers who obtain the credential can reuse it for an extended period, increasing the risk of persistence and domain-wide compromise.
By default, a domain controller should automatically change its computer account password every 30 days. A significantly longer interval usually indicates misconfiguration, operational issues, or possible tampering.
Common causes include replication problems, broken secure channels, incorrect system time, disabled password change settings, or manual intervention that disrupted the normal password rotation process.
Cayosoft Guardian continuously monitors Active Directory infrastructure and evaluates the last password change timestamp of domain controllers to identify systems that fall outside expected rotation behavior.
Cayosoft Guardian provides visibility into affected domain controllers and historical context, enabling administrators to quickly investigate, correct credential issues, and ensure domain controllers remain securely maintained.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory environment. By addressing issues like a domain controller not changing its password, you reduce attack surfaces and strengthen your organization’s overall security posture.