Failed logon attempts targeting honey account
Cayosoft Threat Definition CTD-000185
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Honey accounts are non-operational, decoy accounts intentionally created to attract and monitor unauthorized access attempts by threat actors. A series of failed logon attempts targeting these accounts may indicate brute-force attacks, reconnaissance activity, or the presence of an unauthorized user probing the environment. Because honey accounts are not used for any legitimate business activity, any authentication attempt against a honey account is inherently suspicious.
- Severity: Medium
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Credential Access, Discovery
- MITRE D3FEND Tactics: Domain Account Monitoring, D3-CCSA (Credential Compromise Scope Analysis)
Description
Honey accounts are non-operational, decoy accounts intentionally created to attract and monitor unauthorized access attempts by threat actors. A series of failed logon attempts targeting these accounts may indicate brute-force attacks, reconnaissance activity, or the presence of an unauthorized user probing the environment. Such activity often precedes lateral movement or privilege escalation attempts. Because honey accounts are not used in legitimate operations, any authentication attempt against a honey account is considered inherently suspicious.
For more information about the underlying audit signal, see Microsoft’s documentation on Event ID 4625 – An account failed to log on (Microsoft Docs).
NOTE: The CTD-000185 threat definition includes a built-in lookback parameter set to 25 hours. Only events that occurred within this timeframe are processed by the threat definition.

Real-World Scenario
An attacker gains a foothold on a workstation and begins running automated tools to discover valid credentials in the domain. The attacker’s tooling repeatedly attempts to log on to a decoy honey account such as IGASVC (example from configuration), generating multiple Event ID 4625 failures in a short period. Because the honey account is never used by legitimate users or services, the repeated failures are a strong signal of malicious reconnaissance or brute-force activity. The attacker may intend to pivot to lateral movement or privilege escalation once valid credentials are found, while trying to blend into normal logon-failure noise. Cayosoft Guardian’s CTD-000185 threat definition detects the failed logon attempts against the honey account within the defined lookback window and raises an alert before the attacker can progress further.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
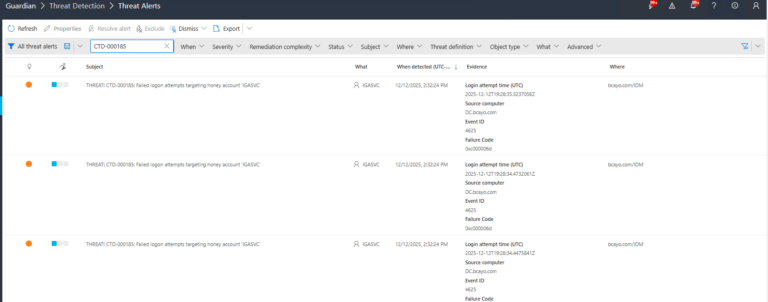
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Open All Alerts and search for CTD-000185 or “Failed logon attempts targeting honey account”.
3.) Open any alert and Click for details (from Raise Threat Alert action).
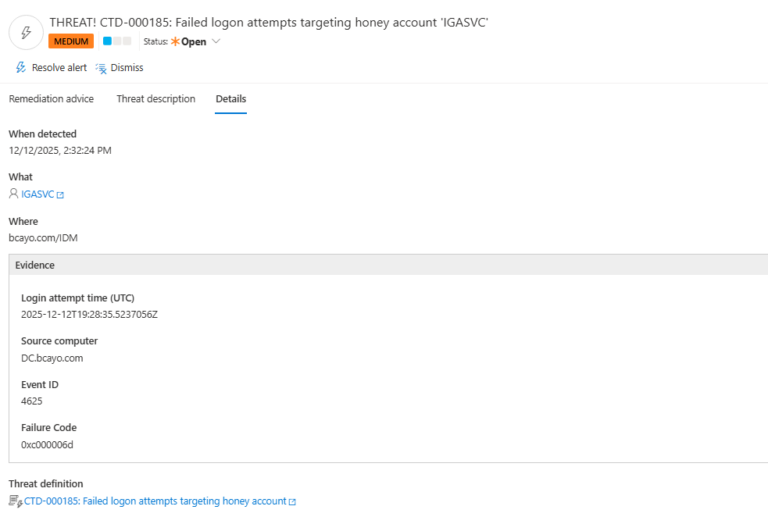
4.) Evidence:
- Login attempt time (UTC) – {TargetItem/LastState/loginAttemptTime}
- Source computer – {TargetItem/LastState/sourceComputer}
- Event ID – {TargetItem/LastState/eventID} (typically 4625 for failed logon)
- Failure Code – {TargetItem/LastState/failureCode}
Remediation Steps
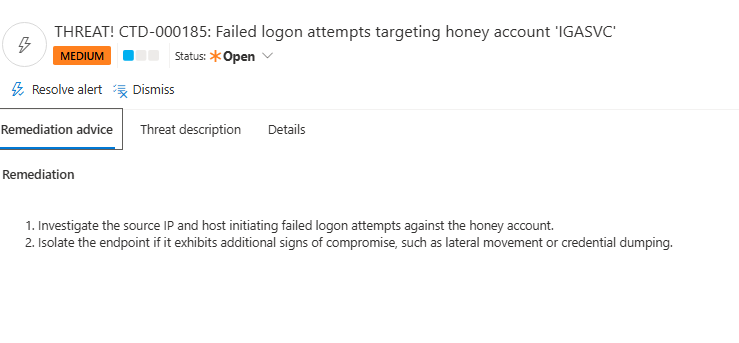
- ) Investigate the source IP and host initiating failed logon attempts against the honey account.
- ) Isolate the endpoint if it exhibits additional signs of compromise, such as lateral movement or credential dumping.
How to Prevent It
- Use clearly labeled, non-operational honey accounts with no legitimate business use to maximize the signal value of any authentication attempt.
- Limit knowledge of honey accounts to a small, trusted security operations group to reduce the risk of accidental use.
- Ensure auditing for Event ID 4625 is enabled and logs are retained long enough for investigation and correlation.
- Maintain and review Cayosoft Guardian alerts for CTD-000185 regularly, tuning honey account names and the lookback window to align with your environment and threat model.
- Integrate CTD-000185 alerts with your SIEM or SOAR platform to automate triage steps such as host isolation or creating incident tickets.
FAQ
It indicates that one or more authentication attempts were made against a designated honey (decoy) account, which has no legitimate business use and is intended solely to detect unauthorized access attempts.
Honey accounts are never used for normal operations, so any logon attempt—successful or failed—is a strong indicator of reconnaissance, brute-force activity, or credential testing by an attacker.
This behavior is often associated with password spraying, brute-force attacks, automated credential discovery tools, or attackers probing the environment after gaining an initial foothold.
Cayosoft Guardian monitors Active Directory authentication events and correlates failed logon attempts targeting designated honey accounts, raising alerts when suspicious activity is detected within the defined monitoring window.
By detecting early credential probing against honey accounts, Cayosoft Guardian provides high-confidence signals that can be correlated with other alerts to assess the scope and progression of a potential credential compromise.
References
- Microsoft documentation: Event ID 4625 – An account failed to log on (Security Auditing).
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Failed logon attempts targeting honey account, you reduce attack surfaces and strengthen your organization’s overall security posture.