Breached credentials remain one of the most common entry points for attackers. The challenge is not just knowing that a breach occurred. The real challenge is identifying which exposed credentials belong to your users, your domains, and your identity systems, and then responding quickly with minimal noise.
With the latest release of Cayosoft Guardian, organizations can now take advantage of direct integration with HaveIBeenPwned (HIBP) combined with new compromised credential detections for both Active Directory and Entra ID. Guardian automatically identifies exposed accounts across hybrid identity environments and enriches each incident with actionable intelligence.
Note: This capability is included in paid editions of Guardian and is not available in Guardian Protector.
To help security teams focus on real risk, Guardian provides:
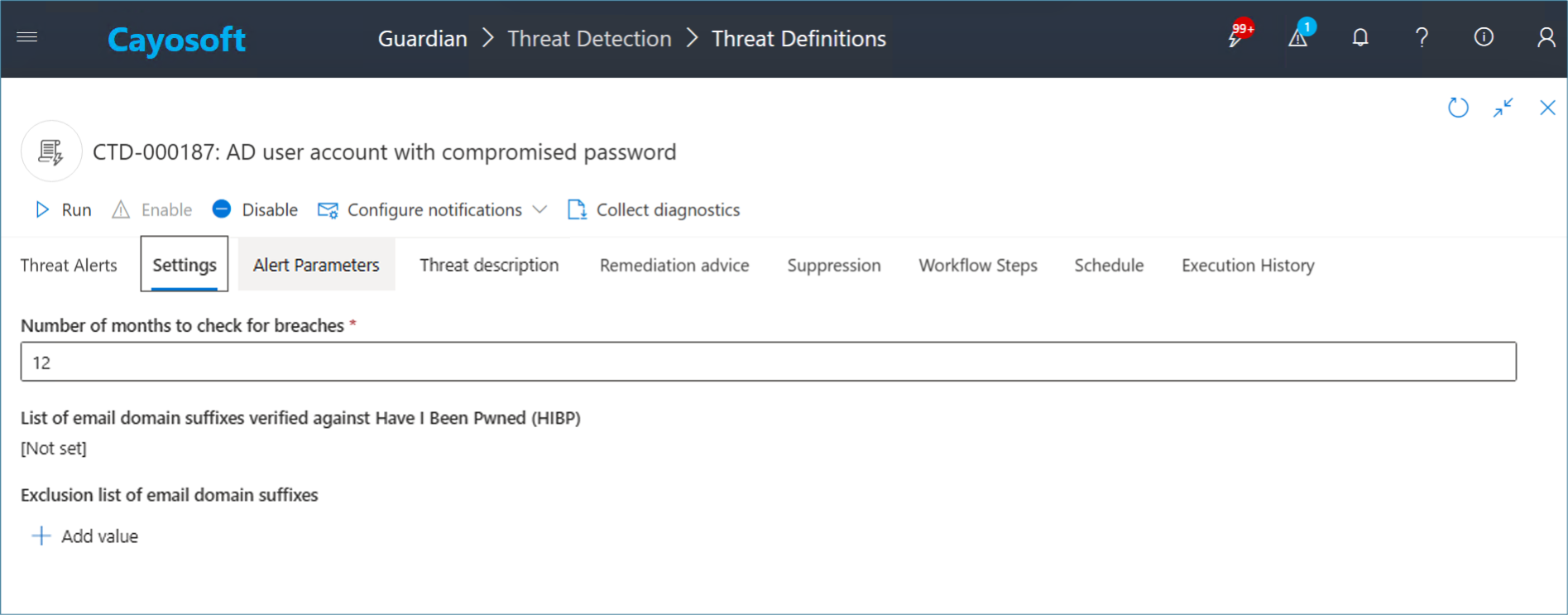
- A twelve-month breach lookback that exposes recent and previously unnoticed credential leaks Note: The lookback window is configurable.
- Password change verification that cuts out noise and highlights only identities that are still vulnerable
This closes the loop between external breach intelligence and internal identity security.
Why Breached Credentials Detection is Now a Top Priority
Hybrid Identity Makes Credential Theft More Dangerous
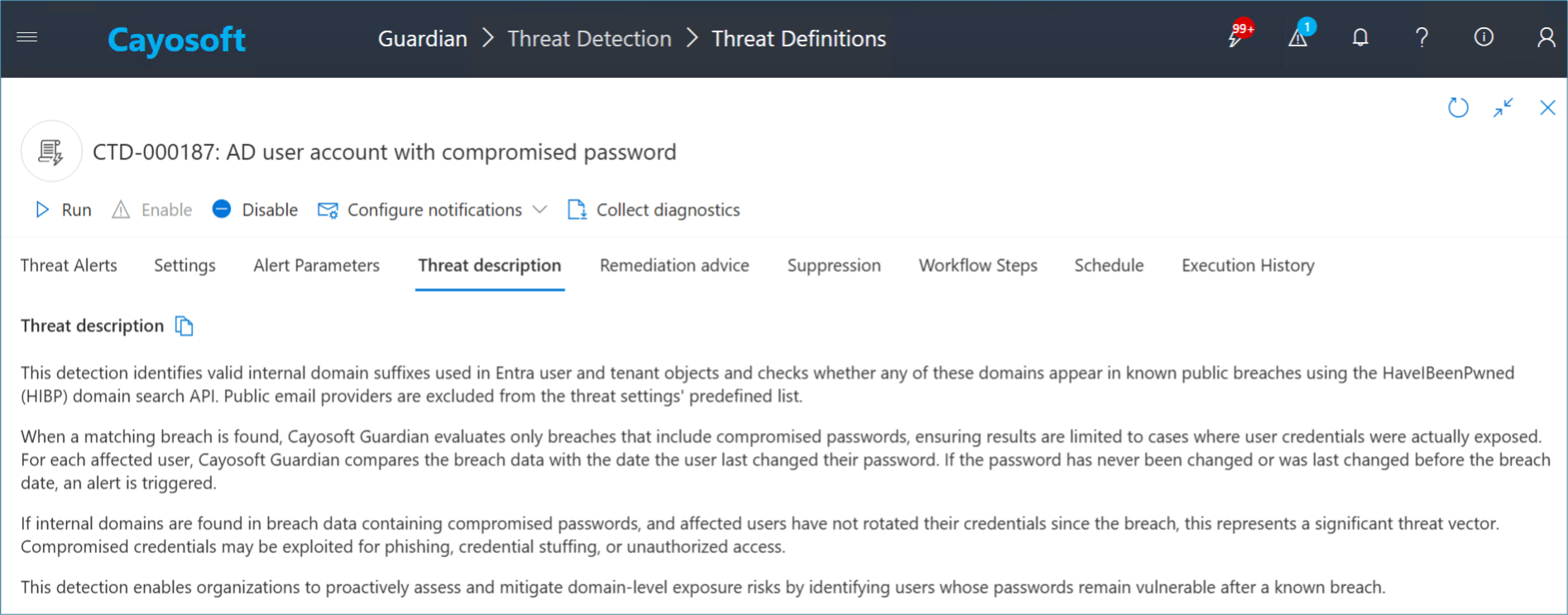
Active Directory and Entra ID are tightly connected. If attackers obtain a working credential in one system, they often gain access to the other. One exposed password can escalate into a full compromise.
Example:
A user reuses the same password for both AD and Entra ID. Months later, that password appears in a public breach tied to a consumer service. An attacker signs into a cloud app using the exposed Entra ID credential and bypasses basic controls using a device token purchased from the dark web. Once inside, they test the same password on the VPN and authenticate successfully.
What began as a simple password reuse issue became a material incident with legal notification requirements and audit impact. Early detection would have prevented the escalation entirely.
Breach Data Arrives Long After the Attack
Credential dumps often surface weeks or months after the original intrusion. Attackers may already be exploiting these credentials long before organizations even see the breach data.
Example:
HIBP published a new dataset from a breach that occurred two months earlier. One of your privileged hybrid identities appears in the dump. The user never changed their password, and your team had no visibility that your domain was affected.
The attacker has already accessed unmanaged cloud resources and collected sensitive information. When the SOC finally discovers the exposure manually, the organization faces both cleanup and compliance reporting. Continuous correlation would have flagged the risk the moment the breach surfaced.
Security Teams are Drowning in Noise
Static breach lists provide no context and produce overwhelming alert volume. Most exposed credentials no longer pose risk because the user has already changed their password.
Example:
A security team imports a breach dataset and identifies 250 exposed accounts. After manual review, they discover that 210 users have already changed their passwords and no longer represent risk. Only 40 accounts remain vulnerable.
The team wastes valuable time filtering out false positives, while one of the high-risk accounts is actively being probed. That account belongs to a service operator with access to sensitive systems. This creates downstream audit findings that could have been avoided. Guardian automatically suppresses the 210 safe accounts and escalates the 40 real threats.
What’s New in Cayosoft Guardian for Compromised Credential Detection
Direct HIBP Integration for Breach Intelligence
Guardian securely ingests credential breach data from HaveIBeenPwned and automatically correlates entries with:
- Organizational domains
- Active Directory UPN suffixes
- Entra ID identities and aliases
This provides a unified and continuously updated view of credential exposure across your hybrid identity environment.
New Threat Detections for Active Directory and Entra ID
- Active Directory Compromised Credential Detection
- Entra ID Compromised Credential Detection
- Breach date
- Breach source
- Password change status
Twelve Month Breach Lookback for Full Visibility
Guardian automatically evaluates breach data from the most recent 12 months. This is critical for:
- Organizations that missed earlier breach disclosures
- Accounts that transitioned between AD and Entra ID
- Long lived credentials that were never rotated
Most organizations never see these long tail exposures. Guardian makes it impossible to miss.
Intelligent Noise Suppression for More Accurate Alerts
Guardian validates whether each user changed their password after the breach occurred.
- If the password is changed, Guardian suppresses the alert
- If the password was not changed, Guardian raises a high priority incident
This dramatically reduces alert fatigue and focuses security teams on accounts that attackers can still exploit.
How Cayosoft Guardian Processes Breached Credentials
Ingestion and Normalization
Guardian retrieves HIBP breach entries based on your verified domains and UPN suffixes. Each record is normalized with:
- Breach timestamp
- Breach source
- Breach data lists password
This ensures consistent and reliable correlation across identity systems.
Hybrid Identity Correlation Across AD and Entra ID
Guardian automatically maps breach data to:
- Active Directory users through UPN or email attributes
- Entra ID users through Entra ID managed domains
This coverage ensures that no exposed account goes unrecognized.
Password Change Verification
Guardian evaluates each exposed identity by comparing:
- AD password last set timestamp
- Entra ID credential change signals
- Breach timestamp
Organizations can configure Guardian:
- Timeframe to look back for breaches
- Exclude domains
Continuous Re-Evaluation of Credential Risk
When users update their passwords, Guardian automatically rescans and reclassifies the incident. This ensures risk scoring remains accurate over time.
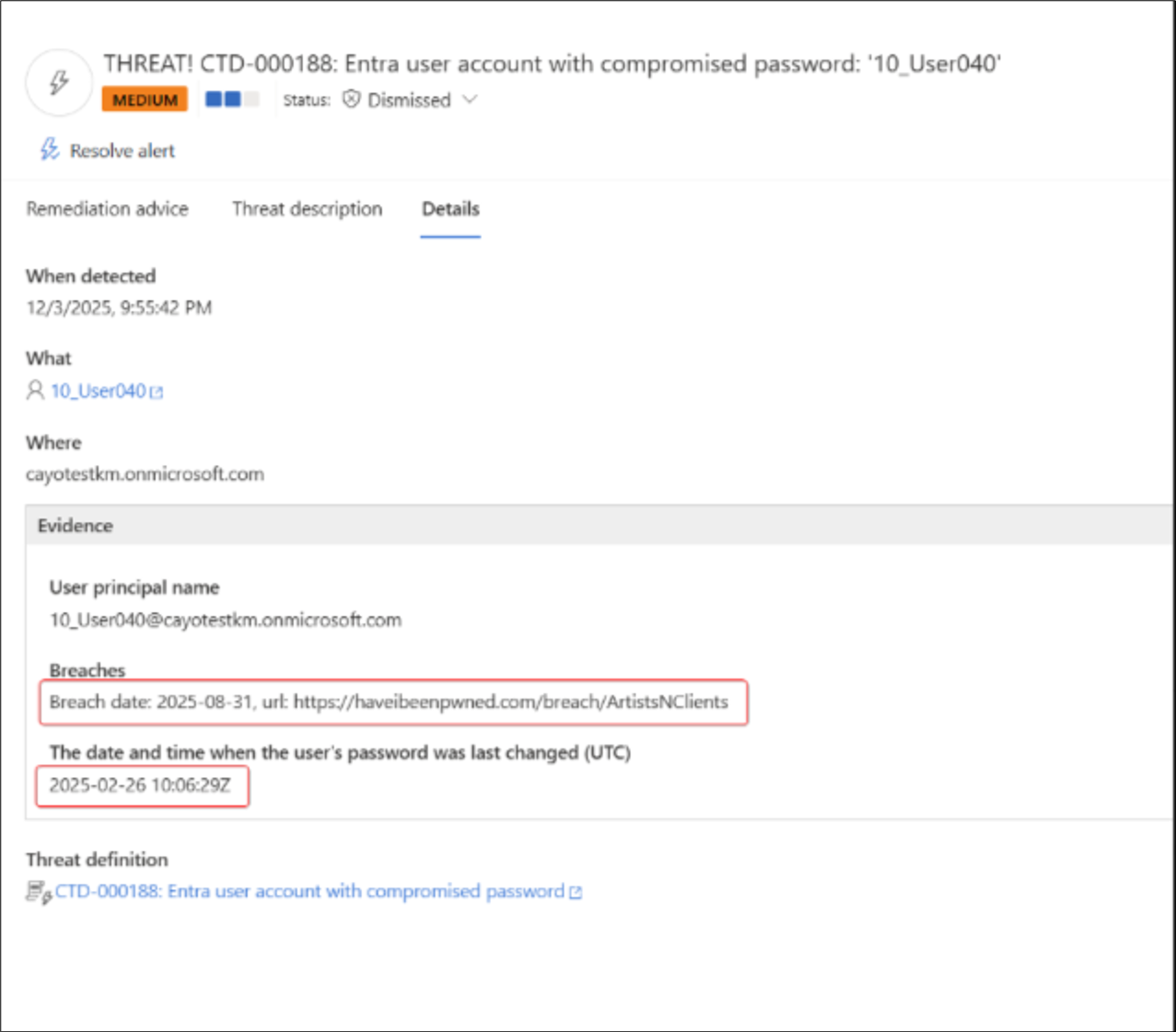
What Security Teams See in the Guardian Console
Guardian presents a clear and intuitive incident alert for each compromised credential, including:
- Affected user identity
- Breach name and date
- Password change status
- Recommended remediation steps
Teams can immediately see which accounts still pose real and immediate risk.
Measurable Benefits of Guardian and HIBP Integration
- Faster identification of AD and Entra ID breached credentials
- Reduced alert noise through password verification
- Stronger compliance posture through trackable remediation
- Continuous credential validation aligned with Zero Trust identity security
Real World Use Cases
Incident Response
Guardian flags a finance user whose credentials appear in a breach list. The user has not changed their password. The SOC forces a reset, enforces MFA, and applies Conditional Access adjustments. The incident is documented for audit and compliance reporting.
Mergers and Acquisitions
After an acquisition, new domains and UPN suffixes are added to Guardian. The twelve-month lookback identifies exposed accounts across the combined environment, helping teams eliminate inherited credential risk during integration.
Password Hygiene and Identity Governance Reviews
During quarterly access reviews, identity teams use Guardian to confirm which accounts appeared in breach datasets and whether users completed required password updates. Governance teams gain verified evidence that reduces manual review effort.
Service Account Credential Monitoring
Email enabled service accounts or identities tied to breach affected domains are surfaced by Guardian. Security teams can verify credential rotation and prevent unmanaged service accounts from becoming hidden attack paths.
Audit and Compliance Evidence
Guardian provides auditors with complete and time-stamped proof of detection, review, and remediation for all exposed credentials. This lowers audit friction and strengthens compliance with identity security requirements.