AD domain with Operator Groups that are not empty
Cayosoft Threat Definition CTD-000115
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Account Operators, Server Operators, Backup Operators, and Print Operators might have broad permissions to access resources across the environment. If these Operator Groups are not empty, a threat actor who compromises any member account can access critical data and, in many cases, elevate privileges to Domain Admins. Keeping these groups populated significantly increases the risk of domain-wide compromise.
- Severity: Medium
- Platform: Active Directory
- Category: Domain-wide
- MITRE ATT&CK Tactics: Credential Access, Privilege Escalation
MITRE D3FEND Tactics: User Account Permissions
Description
Account Operators, Server Operators, Backup Operators, and Print Operators might have permissions to access resources in the environment. A threat actor could compromise accounts that are members of these groups to gain access to critical data. Also, in many cases, a member of such a group can elevate their permissions to Domain Admins.
CTD-000115 detects when any of the built-in Operator Groups in an Active Directory domain are not empty, exposing potential paths for credential theft, lateral movement, and privilege escalation.

Real-World Scenario
An attacker first compromises a helpdesk operator account that is a member of the Account Operators group. Using those delegated privileges, the attacker resets passwords on service accounts and privileged users, then signs in as those users to gain access to sensitive systems. From there, the attacker leverages membership in additional Operator Groups to manage servers, access backups, and modify print servers, slowly escalating privileges until Domain Admin access is obtained—all by using legitimate built-in groups that often escape scrutiny. Cayosoft Guardian continuously monitors the environment for non-empty Operator Groups and raises CTD-000115 when these groups contain members, allowing administrators to detect and remove risky memberships before attackers can abuse them.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
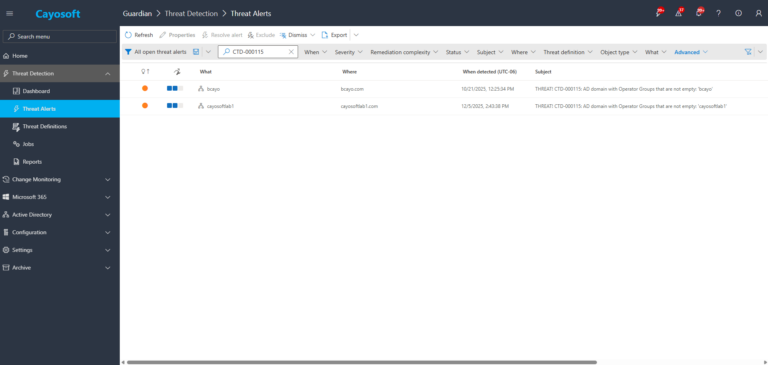
2.) Open Threats / Alerts and search for CTD-000115 or “AD domain with Operator Groups that are not empty”.
3.) Open any alert and Click for details (from Raise Threat Alert action).
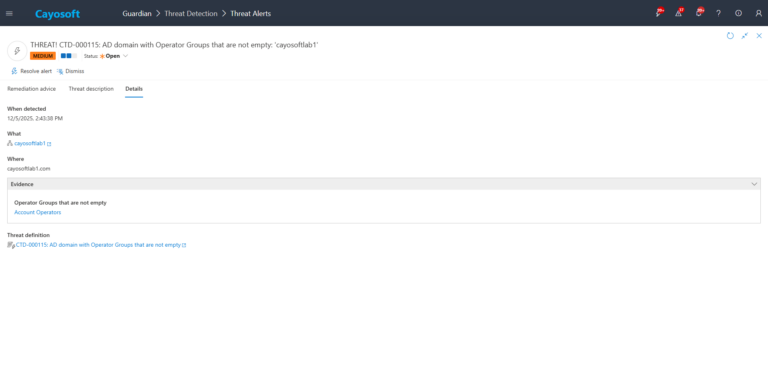
4.) Evidence:
- Operator Groups that are not empty
Remediation Steps
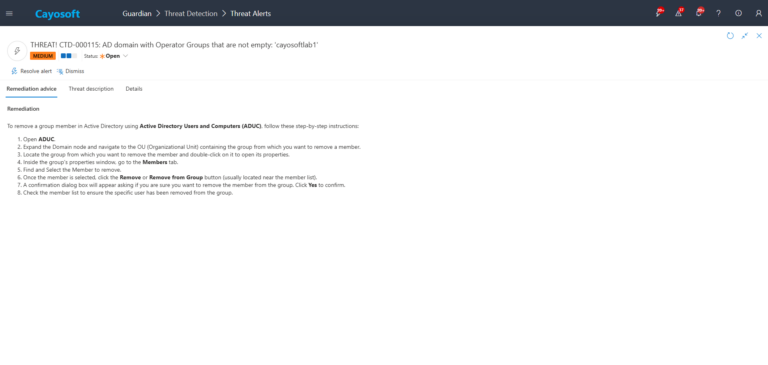
To remove a group member in Active Directory using Active Directory Users and Computers (ADUC), follow these step-by-step instructions:
- ) Open ADUC.
- ) Expand the Domain node and navigate to the OU (Organizational Unit) containing the group from which you want to remove a member.
- ) Locate the group from which you want to remove the member and double-click on it to open its properties.
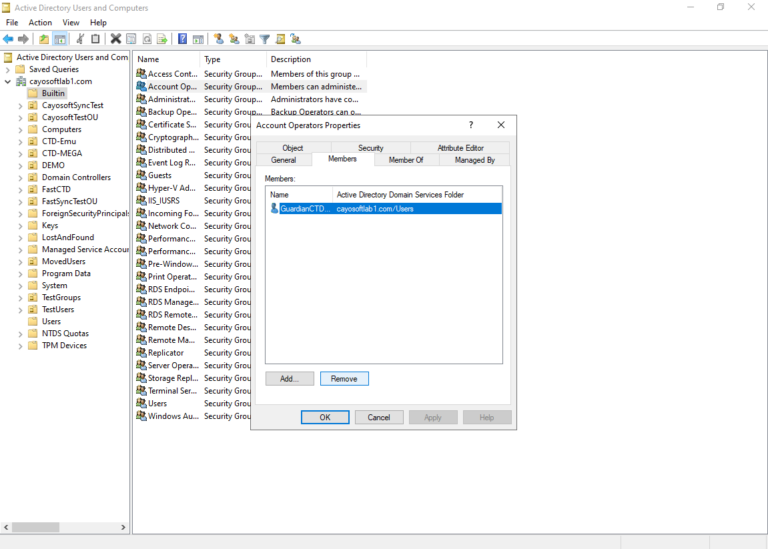
- ) Inside the group’s properties window, go to the Members tab.
- ) Find and Select the Member to remove.
- ) Once the member is selected, click the Remove or Remove from Group button (usually located near the member list).
- ) A confirmation dialog box will appear asking if you are sure you want to remove the member from the group. Click Yes to confirm.
- ) Check the member list to ensure the specific user has been removed from the group.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD domain with Operator Groups that are not empty. Cayosoft Guardian continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations and risky conditions, providing early warning before attackers can exploit over-privileged built-in groups for credential access and privilege escalation.
To further prevent recurrence:
- Keep Operator Groups (Account Operators, Server Operators, Backup Operators, Print Operators) empty by default unless a strong business justification exists.
- Use granular delegation rather than assigning broad memberships in powerful built-in groups.
- Implement strict access request, approval, and periodic review processes for any membership in Operator Groups.
- Regularly review Cayosoft Guardian alerts for CTD-000115 and verify that any detected memberships are immediately investigated.
- Educate administrators about the risks associated with Operator Groups and enforce least-privilege principles across the domain.
FAQ
Operator Groups—Account Operators, Server Operators, Backup Operators, and Print Operators—have broad permissions across the domain. Compromise of any member can allow credential theft, access to critical systems, and a path to Domain Admin privileges.
Cayosoft Guardian evaluates the membership of all built-in Operator Groups and raises CTD-000115 if any accounts are present. The alert lists affected groups and associated members for review.
Ideally, yes. Modern environments should keep these groups empty and rely on granular delegation models. Any membership should be justified, documented, and temporary.
Cayosoft Guardian provides continuous monitoring, historical change tracking, and alerting for Operator Groups. This creates a clear audit trail showing when members were added or removed, which supports compliance reporting and internal audits.
Yes. Alerts link to Change History and prescriptive remediation guidance, allowing administrators to quickly remove unauthorized members. While automatic remediation is optional, the tool provides clear, step-by-step instructions to enforce least-privilege principles safely.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain with Operator Groups that are not empty, you reduce attack surfaces and strengthen your organization’s overall security posture.