Regular AD object with access to gMSA passwords
Cayosoft Threat Definition CTD-000127
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A standalone Managed Service Account (sMSA) is a managed domain account designed to streamline security through automated password management, simplified Service Principal Name (SPN) management, and delegated administration. A Group Managed Service Account (gMSA) extends these capabilities across multiple servers, and any regular AD object allowed to retrieve a gMSA password becomes a high-value credential target. If a threat actor compromises such an object, the attacker can request the gMSA password and leverage that access to move laterally and escalate privileges.
- Severity: High
- Platform: Active Directory
- Category: Infrastructure
- MITRE ATT&CK Tactics: Credential Access
MITRE D3FEND Tactics: Domain Account Monitoring
Description
A standalone Managed Service Account (sMSA) is a managed domain account that simplifies service account management through automated password rotation, SPN management, and delegated administration. A Group Managed Service Account (gMSA) extends these capabilities to multiple servers in a domain, allowing shared use of a single managed identity where the Windows operating system automatically handles password management and SPN updates, removing the need for manual password changes by administrators.
Computers and other security principals that use gMSAs request the current password from Active Directory to start services. gMSAs are configured so specific computer accounts or groups are allowed to retrieve the password. A security issue arises when a threat actor compromises a computer or any regular AD object that has the necessary permissions to request a gMSA password; the attacker can then obtain the managed password and impersonate the gMSA. Once the gMSA is compromised, any services, resources, or permissions associated with that account are also at risk.
NOTE: Cayosoft Guardian defines privileged users in Active Directory as users with adminCount=1. By design, Active Directory uses this attribute to protect members of administrative groups.
According to security best practices, re-using admin accounts is not recommended; these accounts should be properly de-provisioned when no longer needed. If an account has administrative permissions, it may gain access to additional resources and can retain that access even after removal from administrative groups due to how protected ACLs are applied. For more background, see Microsoft guidance on AdminSdHolder and SDProp.

Real-World Scenario
An attacker first compromises a regular server in the domain that runs a line-of-business application. The application uses a gMSA as its service account, and the compromised server’s computer account is listed as a principal allowed to retrieve the gMSA password. After gaining local admin on the server, the attacker uses built-in APIs or tools to request the gMSA’s current password from Active Directory and then reuses those credentials to authenticate to database servers and file servers where the gMSA has rights. Because the gMSA is viewed as a “service account,” security teams may not immediately recognize the abnormal activity. Cayosoft Guardian configured with CTD-000127 would highlight that a regular AD object has access to gMSA passwords and show which principals are allowed, enabling administrators to restrict that access before the attack path is abused.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
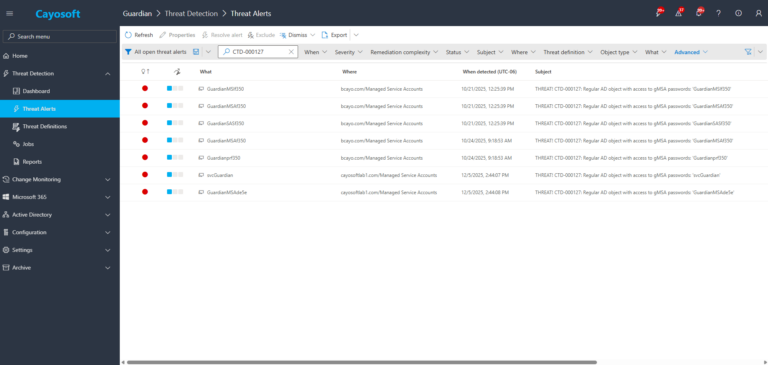
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Open Alerts and search for CTD-000127 or “Regular AD object with access to gMSA passwords.”
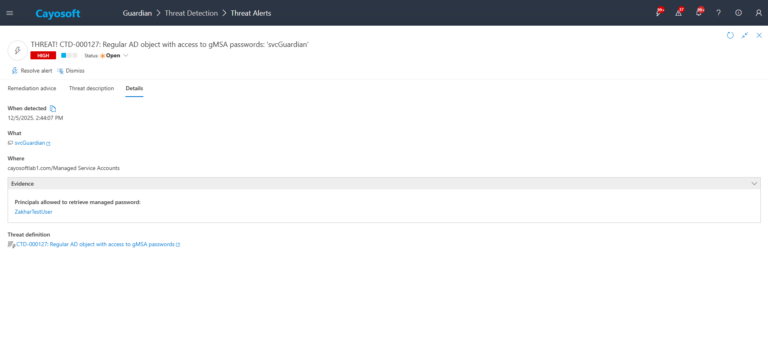
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- Principals allowed to retrieve managed password
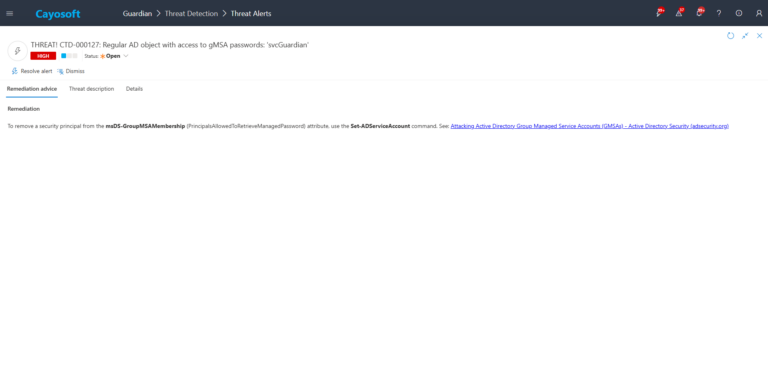
Remediation Steps
To remove a security principal from the msDS-GroupMSAMembership (PrincipalsAllowedToRetrieveManagedPassword) attribute, use the Set-ADServiceAccount command. See: Attacking Active Directory Group Managed Service Accounts (GMSAs) – Active Directory Security (adsecurity.org)
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Regular AD object with access to gMSA passwords. Cayosoft Guardian continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for risky configurations such as overly broad access to gMSA passwords, providing early warning before attackers can abuse these accounts for credential theft and lateral movement.
To reduce risk further:
- Limit msDS-GroupMSAMembership / PrincipalsAllowedToRetrieveManagedPassword to only the computers or groups that must run services using the gMSA.
- Avoid granting gMSA password retrieval rights to regular user accounts or general-purpose groups.
- Harden servers that are allowed to use gMSAs (for example, restrict interactive logons and local admin access).
- Periodically review all gMSAs and remove unused or stale principals that no longer require access.
- Combine CTD-000127 with monitoring of privileged accounts (adminCount=1) to detect high-impact combinations of access.
FAQ
Any regular AD object that can retrieve a gMSA password can impersonate that gMSA. If the gMSA has elevated rights on servers, databases, or applications, compromising the regular object provides an indirect path to these high-value resources.
This attribute defines which security principals—users, groups, or computer accounts—are allowed to request the gMSA’s current password from Active Directory. Only dedicated, hardened service hosts or groups should be granted this access.
Yes. PowerShell and native AD tools can list PrincipalsAllowedToRetrieveManagedPassword for gMSAs, but Cayosoft Guardian provides automated detection and alerts for any regular AD objects with gMSA access.
Yes. Cayosoft Guardian continuously monitors Active Directory for over-permissioned gMSA access, raises CTD-000127 alerts, and provides prescriptive guidance to safely restrict and remediate access.
References
- Attacking Active Directory Group Managed Service Accounts (GMSAs) – Active Directory Security (adsecurity.org)
- Microsoft documentation on adminCount and protected administrative accounts
- Microsoft guidance on AdminSdHolder and SDProp behavior for admin objects
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Regular AD object with access to gMSA passwords, you reduce attack surfaces and strengthen your organization’s overall security posture.