AD user added to privileged group
Cayosoft Threat Definition CTD-000146
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Modification of privileged group membership might be an indication of a privilege escalation attempt by a threat actor. Such changes can signal unauthorized access or attempts to gain elevated permissions within Active Directory.
- Severity: High
- Platform: Active Directory
- Category: Privileged Access Management
- MITRE ATT&CK Tactics: Privilege Escalation, Credential Access
MITRE D3FEND Tactics: Restore Configuration
Description
Modification of privileged group membership might be an indication of a privilege escalation attempt by a threat actor. This activity can signal unauthorized access or an attempt to gain elevated permissions within the system.
Administrators can configure alerts based on AdminCount or sAMAccountName to monitor and detect suspicious changes to privileged group memberships. However, the built-in privileged groups will always trigger an alert, regardless of user configuration, ensuring that critical security events are not overlooked.
Cayosoft Guardian considers both direct and indirect (nested) group permissions when evaluating risks. Privileged users are defined in Active Directory as groups with adminCount=1 and a well-known SID.
NOTE: This threat rule includes a built-in lookback parameter set to 48 hours. Only events that occurred within this timeframe are processed by CTD-000146.

Real-World Scenario
A helpdesk operator’s account is compromised through phishing and reused passwords. The attacker uses the stolen credentials to connect to a management workstation and quietly adds the compromised user to the Domain Admins group, hoping the change will be lost among routine admin activity. With the new privileged group membership, the attacker gains full control over domain controllers, GPOs, and user accounts, and then creates additional backdoor accounts to maintain persistence. Because the change is a direct modification of privileged group membership and the affected group has adminCount=1, it represents both credential access and privilege escalation. Cayosoft Guardian, using CTD-000146, detects the addition of the user to the privileged group within the 48-hour lookback window and raises an alert before the attacker can fully exploit domain-wide access.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
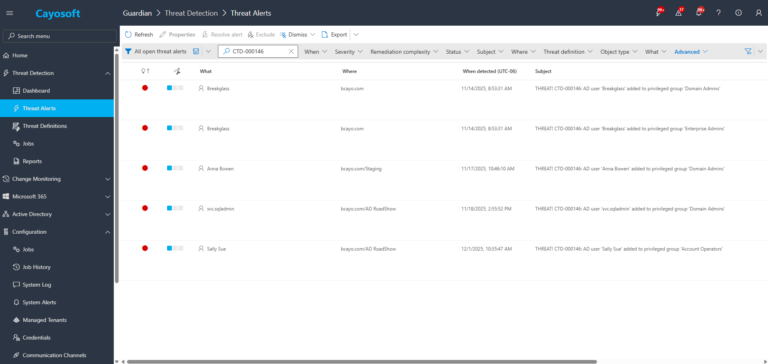
2.) Open All Alerts and search for CTD-000146 or “AD user added to privileged group”.
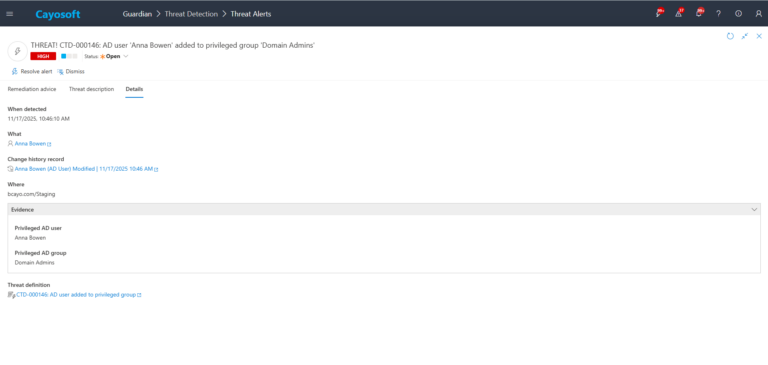
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- Privileged AD user
- Privileged AD group
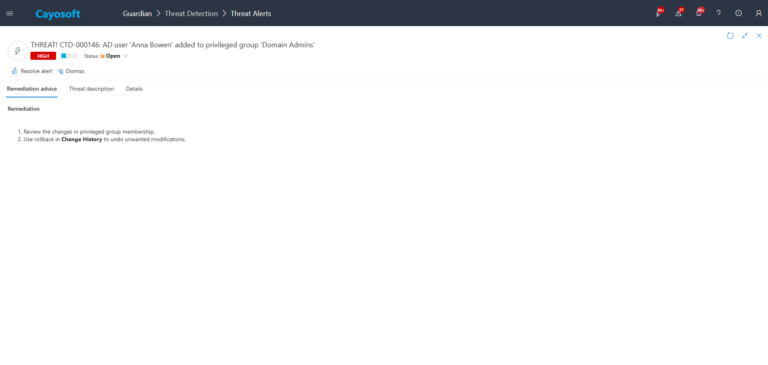
How to Prevent It
- Restrict who can modify membership of built-in privileged groups and other groups with adminCount=1.
- Use a change management process requiring approval and documented justification for any addition to privileged groups.
- Regularly review membership of groups such as Domain Admins, Enterprise Admins, Administrators, Enterprise DCs, and similar high-privilege roles.
- Enable and keep CTD-000146 active in Cayosoft Guardian to continuously monitor and alert on additions to privileged groups (direct and nested).
- Protect admin accounts with MFA, just-in-time access, and least-privilege assignments to reduce the chance of compromise.
Cayosoft Guardian can proactively detect and alert on AD user added to privileged group. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Privileged groups such as Domain Admins grant full control over domain resources. Unauthorized additions are a common privilege escalation technique that immediately exposes the environment to credential theft, configuration takeover, and persistence mechanisms.
CTD-000146 recognizes privileged groups by checking for adminCount=1 and well-known SIDs, along with any designated privileged groups configured by administrators. These characteristics ensure that all high-risk groups are monitored consistently.
Yes. CTD-000146 evaluates both direct and indirect (nested) group membership changes. Any path that results in a user gaining privileged group rights triggers an alert.
Yes. Native tools like PowerShell and event logs can be used manually, and Cayosoft Guardian Protector offers free detection that highlights risky privileged group changes without requiring a full license.
Yes. Cayosoft Guardian provides continuous monitoring, real-time alerting, full audit history, and guided remediation for CTD-000146 and more than 200 additional AD/Entra/M365 configuration risks.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD user added to privileged group, you reduce attack surfaces and strengthen your organization’s overall security posture.