Folder on SYSVOL with non-default access permissions
Cayosoft Threat Definition CTD-000125
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Improper access permissions for directory data files could allow unauthorized users, including threat actors, to read, modify, or delete directory data. The SYSVOL directory contains public domain files such as policies and logon scripts, which are replicated to all domain controllers; non-default permissions on SYSVOL significantly increase the risk of domain-wide compromise.
- Severity: Medium
- Platform: Active Directory
- Category: Forest-wide, Infrastructure
- MITRE ATT&CK Tactics: Persistence, Privilege Escalation, Defense Evasion
MITRE D3FEND Tactics: Application Configuration Hardening
Description
Improper access permissions for directory data files could allow unauthorized users, including threat actors, to read, modify, or delete directory data. The SYSVOL directory contains public files to the domain, such as policies and logon scripts, and data in shared subdirectories is replicated to all domain controllers in a domain.
If a threat actor can obtain more than read-and-execute access on folders within SYSVOL, the threat actor can tamper with Group Policy Objects (GPOs), scripts, or configuration data and have those malicious changes distributed automatically to every domain controller and affected endpoint. This can be used for persistence, privilege escalation (for example, by adding users to privileged groups or deploying malicious startup scripts), and defense evasion by hiding malicious changes inside legitimate policy mechanisms.
Cayosoft Guardian defines privileged users in Active Directory as users with adminCount=1. By design, Active Directory uses this attribute to protect members of administrative groups, as described in the Microsoft documentation for the adminCount attribute and the AdminSDHolder/SDProp process. According to security best practices, privileged accounts should not be reused; they should be de-provisioned when no longer required to prevent lingering elevated access to resources such as SYSVOL.

Real-World Scenario
An attacker first compromises a standard user account in an organization. Because the SYSVOL folder has non-default access permissions, the compromised account has modify rights on a GPO script directory under SYSVOL. The attacker edits a logon script in SYSVOL to download and execute a remote payload whenever users in a specific OU log on, gaining persistence on multiple endpoints without altering obvious group memberships. Next, the attacker adjusts the script to silently add the attacker’s secondary account to a highly privileged group, achieving privilege escalation via normal Group Policy processing. Since the changes occur within GPO scripts replicated by SYSVOL, traditional monitoring focused only on group changes or direct admin activity might not detect the attack. Cayosoft Guardian, using CTD-000125, would detect that the SYSVOL folder has non-default access permissions and highlight which user and permission changes are exposing the environment, allowing security teams to correct the ACLs before the attack chain completes.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
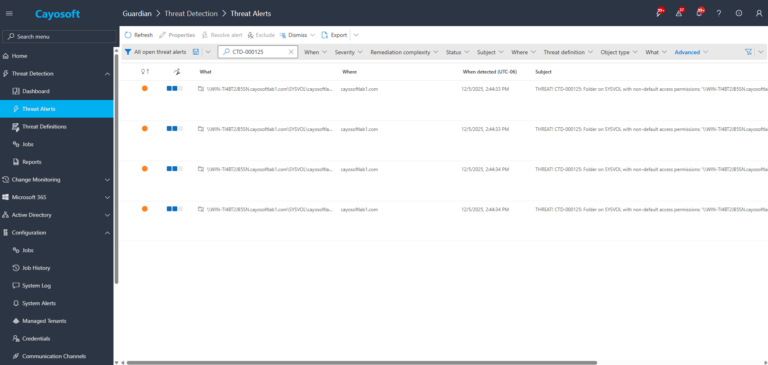
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Filter or search for CTD-000125 or the threat definition name “Folder on SYSVOL with non-default access permissions”.
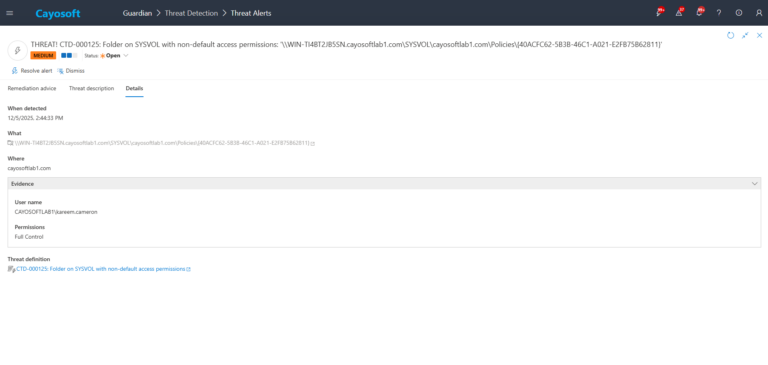
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- User name – username
- Permissions – permissions
Remediation Steps
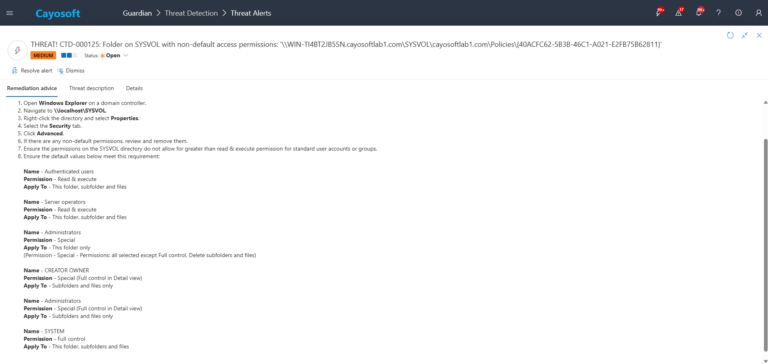
To review and remove non-default permissions on the SYSVOL folder:
1.) Open Windows Explorer on a domain controller.
2.) Navigate to \\localhost\SYSVOL.
3.) Right-click the directory and select Properties.
4.) Select the Security tab.
5.) Click Advanced.
6.) If there are any non-default permissions, review and remove them.
7.) Ensure the permissions on the SYSVOL directory do not allow for greater than read & execute permission for standard user accounts or groups.
8.) Ensure the default values below meet this requirement:
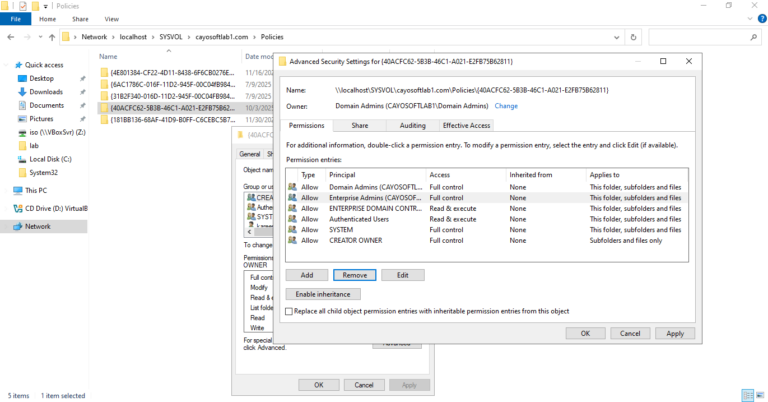
Name
- – Authenticated users
Permission
- – Read & execute
Apply To
- – This folder, subfolder and files
Name
- – Server operators
Permission
- – Read & execute
Apply To
- – This folder, subfolder and files
Name
- – Administrators
Permission
- – Special
Apply To
- – This folder only
- (Permission – Special – Permissions: all selected except Full control, Delete subfolders and files)
Name
- – CREATOR OWNER
Permission
- – Special (Full control in Detail view)
Apply To
- – Subfolders and files only
Name
- – Administrators
Permission
- – Special (Full control in Detail view)
Apply To
- – Subfolders and files only
Name
- – SYSTEM
Permission
- – Full control
Apply To
- – This folder, subfolders and files
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Folder on SYSVOL with non-default access permissions. Cayosoft Guardian continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit misconfigured SYSVOL permissions.
To reduce the likelihood of SYSVOL being abused:
- Enforce standard ACL baselines on the SYSVOL folder and GPO subfolders and periodically review them.
- Restrict write and modify permissions on SYSVOL to tightly controlled administrative groups only.
- Avoid using privileged accounts for routine tasks; de-provision privileged accounts when no longer needed so adminCount=1 users remain strictly controlled.
- Include CTD-000125 alerts in regular security reviews and incident response playbooks.
- Combine Cayosoft Guardian monitoring with regular Group Policy audits to detect unauthorized script or GPO changes.
FAQ
Because SYSVOL replicates policies and logon scripts to every domain controller, any unauthorized user with modify or write permissions can plant malicious content that spreads domain-wide. This enables persistence, privilege escalation, and automated execution of attacker-controlled scripts.
CTD-000125 analyzes the ACLs applied to SYSVOL folders and identifies any accounts or groups with access levels that deviate from secure defaults. The alert includes the specific user and permission set that triggered detection, allowing administrators to validate or correct them immediately.
Attackers may modify logon scripts, inject malicious payloads into GPO folders, or use policy-based mechanisms to add backdoor accounts. Because the changes are replicated automatically, attackers can persist or escalate privileges without directly altering group membership.
Yes. Native tools (e.g., icacls, Event Viewer, GPMC) provide limited visibility, and Cayosoft Guardian Protector offers free assessment capabilities that help identify misconfigured SYSVOL folders and ACL deviations faster and with less manual effort.
Yes. Cayosoft Guardian provides continuous monitoring, real-time threat alerts, change auditing, and prescriptive remediation guidance for CTD-000125 and more than 200 other AD, Entra ID, Microsoft 365, and Intune risk conditions. It ensures that SYSVOL permissions stay aligned with secure defaults to prevent domain-wide compromise.
References
- Microsoft: adminCount attribute documentation
- Microsoft Community Hub: Five common questions about AdminSDHolder and SDProp
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Folder on SYSVOL with non-default access permissions, you reduce attack surfaces and strengthen your organization’s overall security posture.