Active Directory detect dormant accounts for computers and users
Cayosoft Threat Definition CTD-000152
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
This rule detects inactive and never used user and computer accounts in Active Directory (AD) based on the LastLogonTimestamp attribute. By highlighting dormant identities beyond a configurable threshold (typically 90 days for users and computers), the threat definition reduces the risk of stale credentials being abused by attackers. Removing or disabling these accounts lowers the overall attack surface and limits credential theft opportunities.
- Severity: Medium
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Credential Access
MITRE D3FEND Tactics: D3-CRO (Credential Rotation), D3-DAM (Domain Account Monitoring)
Description
This rule detects inactive and never used user and computer accounts in Active Directory (AD) based on the LastLogonTimestamp attribute. The LastLogonTimestamp attribute records the latest time an account successfully logged into the domain. However, it only replicates across domain controllers approximately every 9 to 14 days, making it a more performance-friendly option for identifying dormant accounts across the environment.
By identifying these accounts, administrators can prevent the unauthorized use of stale credentials or deactivate accounts that are no longer needed. The rule uses separate, configurable day thresholds for user accounts and computer accounts (for example, 90 days for each) so you can align detection with your organization’s inactivity standards.

Real-World Scenario
An attacker gains a foothold on the network through a phishing email and begins scanning AD for stale user and computer accounts that have not logged on in months but remain enabled. The attacker identifies several old contractor and workstation accounts whose LastLogonTimestamp shows no activity for more than 90 days and uses password spraying to take over one of them without triggering user complaints. Because the account is no longer monitored by the business owner, the attacker uses it for lateral movement and data exfiltration, confident that the unusual activity will blend into older logs. CTD-000152, configured with 90-day thresholds for users and computers, flags these dormant accounts and raises alerts through Teams and email so administrators can disable or remove them before the attacker can persist long term.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
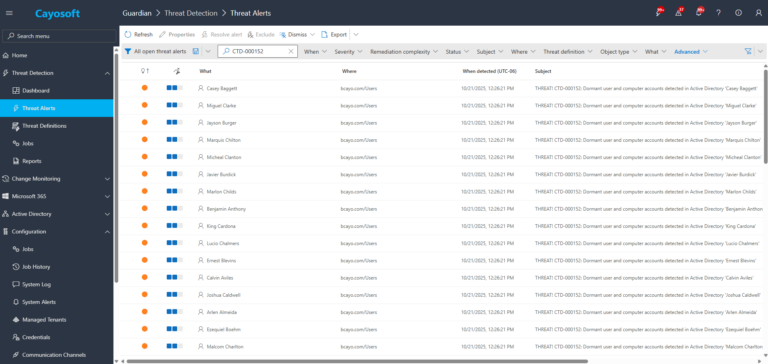
2.) Filter or search for CTD-000152 or “Active Directory detect dormant accounts for computers and users”in the alert list.
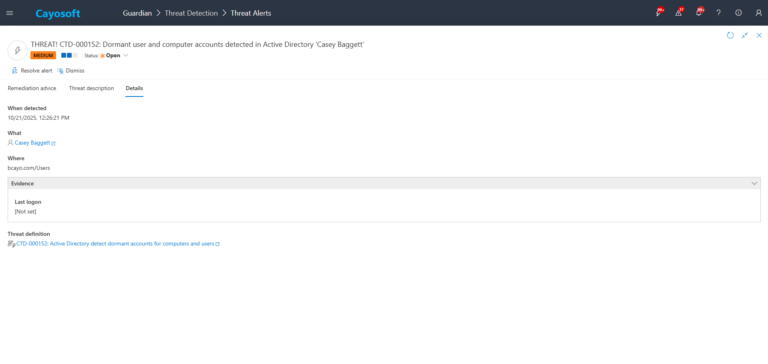
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- Last logon – sourced from lastLogonTimestamp for the target item.
Remediation Steps
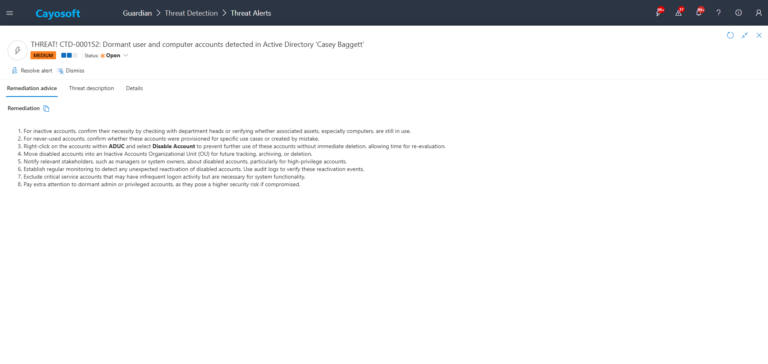
- ) For inactive accounts, confirm their necessity by checking with department heads or verifying whether associated assets, especially computers, are still in use.
- ) For never-used accounts, confirm whether these accounts were provisioned for specific use cases or created by mistake.
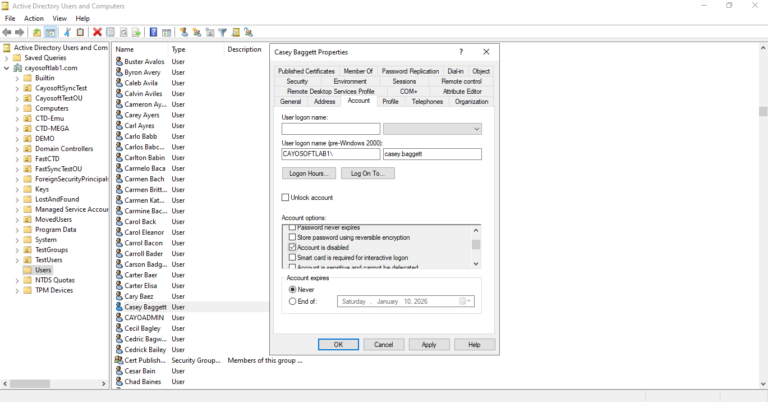
- ) Right-click on the accounts within ADUC and select Disable Account to prevent further use of these accounts without immediate deletion, allowing time for re-evaluation.
- ) Move disabled accounts into an Inactive Accounts Organizational Unit (OU) for future tracking, archiving, or deletion.
- ) Notify relevant stakeholders, such as managers or system owners, about disabled accounts, particularly for high-privilege accounts.
- ) Establish regular monitoring to detect any unexpected reactivation of disabled accounts. Use audit logs to verify these reactivation events.
- ) Exclude critical service accounts that may have infrequent logon activity but are necessary for system functionality.
- ) Pay extra attention to dormant admin or privileged accounts, as they pose a higher security risk if compromised.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Active Directory detect dormant accounts for computers and users. Cayosoft Guardian continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations and risky conditions, including dormant identities and stale credentials, providing early warning before attackers can exploit them. Aligning the user and computer inactivity thresholds with your organization’s account lifecycle policy, and regularly reviewing CTD-000152 alerts, helps ensure dormant accounts are quickly identified and addressed.
FAQ
An account is considered dormant when its LastLogonTimestamp shows no activity beyond the configured inactivity threshold (commonly 90 days for both user and computer accounts).
These accounts often remain enabled and overlooked, making them easy targets for attackers who can use them for password spraying, persistence, credential theft, or lateral movement without alerting users or asset owners.
Yes. The rule uses two separate thresholds—one for user inactivity and one for computer inactivity—allowing organizations to align detection policies with operational requirements and lifecycle processes.
Yes. Native AD tools provide limited visibility, and Cayosoft Guardian Protector offers free assessment capabilities that highlight dormant users and computers, helping organizations quickly pinpoint stale identities.
Yes. Cayosoft Guardian delivers continuous monitoring, real-time alerting, detailed auditing, and prescriptive remediation for CTD-000152 and 200+ other AD, Entra ID, M365, and Intune risks, ensuring dormant accounts are identified and addressed before attackers can exploit them.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Active Directory detect dormant accounts for computers and users, you reduce attack surfaces related to stale identities and strengthen your organization’s overall security posture.