Service principal promoted to privileged role via OAuth consent attack
Cayosoft Threat Definition CTD-000173
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
An attacker could exploit an OAuth consent attack to grant a malicious service principal highly privileged access in Entra ID, enabling long-term persistence. This bypasses normal user sign-in controls and shifts the attack surface into app permissions that are often less monitored.
- Severity: Critical
- Platform: Entra ID
- Category: Privileged Access Management
- MITRE ATT&CK Tactics: Persistence, Privilege Escalation
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
An attacker could exploit an OAuth consent attack to provide a malicious service principal with privileged access, enabling long-term persistence.
NOTE: This threat rule includes a built-in lookback parameter set to 25 hours. Only events that occurred within this timeframe are processed by the rule.

Real-World Scenario
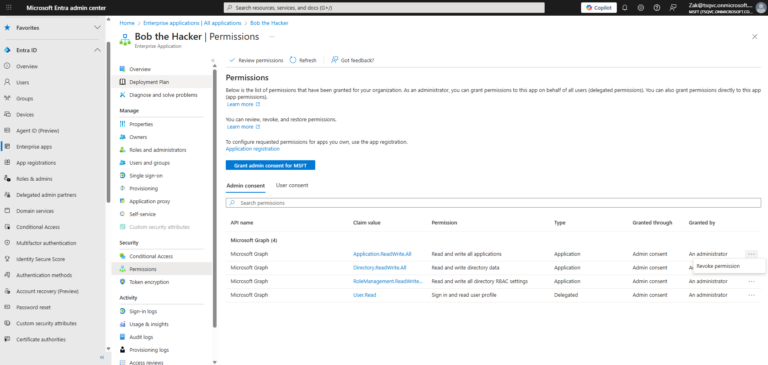
An attacker compromises a standard user account in Microsoft 365 that can grant consent to applications. The attacker tricks the user into approving a malicious multi-tenant app that requests powerful Graph scopes such as Directory.ReadWrite.All or Application.ReadWrite.All. Entra ID creates a service principal in the tenant and stores the granted privileged scopes, effectively promoting the service principal to a highly privileged role without adding the attacker to any obvious admin group. The attacker then uses the app’s credentials or refresh tokens to manage users, groups, and applications in the background, maintaining persistence even if the original user changes their password. Because the app has no owners and no verified publisher, the risk is easy to miss in the portal. Cayosoft Guardian, using CTD-000173, detects that a service principal was promoted to privileged access via OAuth consent and raises an alert within the 25-hour lookback window so the security team can revoke access quickly.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
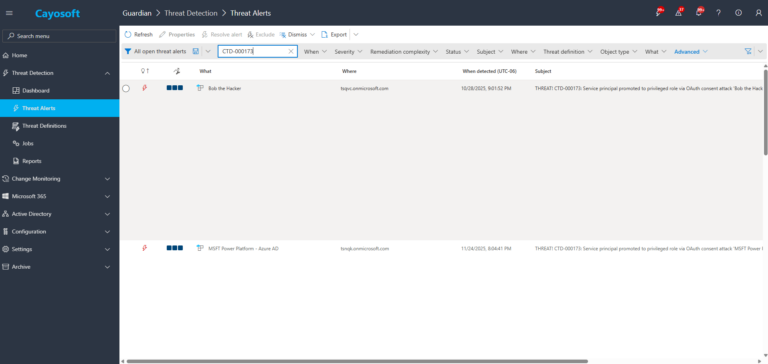
2.) View All Alerts and search for “CTD-000173” or “Service principal promoted to privileged role via OAuth consent attack”.
3.) Open any alert and Click for details (from Raise Threat Alert action).
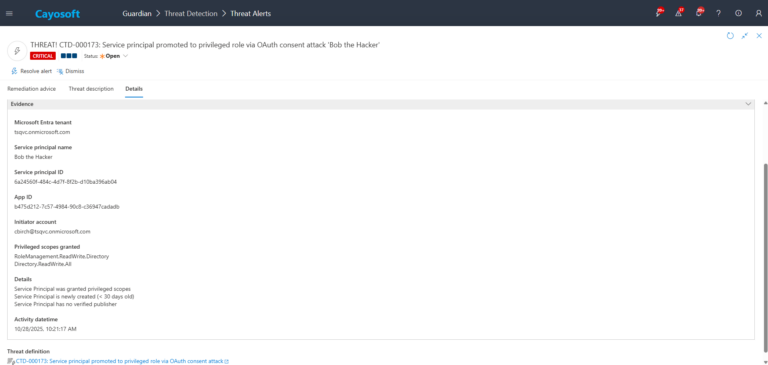
4.)Evidence:
- Microsoft Entra tenant
- Service principal name
- Service principal ID
- App ID
- Initiator account
- Privileged scopes granted
- Details
- Activity datetime
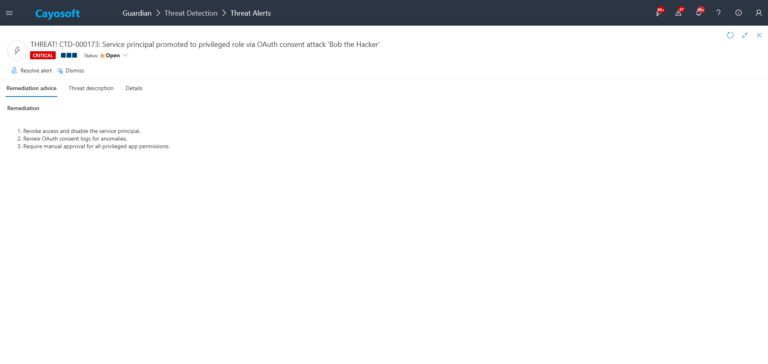
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Service principal promoted to privileged role via OAuth consent attack. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for configuration risks and misconfigurations, providing early warning before attackers can exploit them.
To reduce the risk of Service principal promoted to privileged role via OAuth consent attack:
- Enable and enforce admin consent workflows for all high-privilege app permissions and sensitive delegated scopes.
- Limit who can grant tenant-wide consent and who can register or manage enterprise applications.
- Require that privileged applications have verified publishers and at least one trusted owner.
- Use CTD-000173 with checkUnapprovedElevation enabled to focus on newly created, ownerless, or unverified privileged service principals.
- Regularly review Entra ID enterprise apps and service principals for unused or over-privileged permissions.
FAQ
It means an application was granted privileged API permissions (such as Directory.ReadWrite.All or Application.ReadWrite.All). This effectively elevates the service principal to a high-impact, persistent backdoor without modifying user admin roles.
Privileged application permissions allow silent, non-interactive access to directories, applications, and sensitive objects. Attackers can maintain persistence even after passwords are reset, making this attack extremely difficult to detect and remove.
Enforce admin consent workflows, restrict who can grant tenant-wide permissions, require verified publishers, enforce ownership on all enterprise apps, use CTD-000173 with unapproved elevation checks, and continuously review privileged application permissions.
Yes. Entra ID audit logs, app registration logs, and OAuth consent logs provide free visibility into application permissions. Cayosoft Guardian Protector also offers free change visibility, though advanced alerting and risk correlation require the full product.
Yes. Cayosoft Guardian continuously monitors Entra ID for privileged service principal elevations, raises CTD-000173 alerts, correlates owners/publisher/scopes, and provides guided remediation and rollback for misconfigurations and suspicious OAuth consent events.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Service principal promoted to privileged role via OAuth consent attack, you reduce attack surfaces and strengthen your organization’s overall security posture.