Microsoft Entra user with multiple MFA failures
Cayosoft Threat Definition CTD-000171
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Multiple MFA failures in a short period may indicate a brute-force attempt or an MFA fatigue attack, where attackers spam the user with repeated MFA requests until one is accepted. The threat Microsoft Entra user with multiple MFA failures increases the risk of account takeover even when MFA is enabled.
- Severity: High
- Platform: Entra ID
- Category: Account protection
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Multi-factor Authentication
Description
Multiple MFA failures in a short period may indicate a brute-force attempt or an MFA fatigue attack, where attackers spam the user with repeated MFA requests until one is accepted.

Real-World Scenario
An attacker obtains a Microsoft Entra user’s password from a phishing campaign and begins sending repeated MFA prompts to the user’s mobile device every few seconds. The user is busy in a meeting and eventually accepts one of the prompts just to clear the notifications, unknowingly approving the attacker’s sign-in. The attacker then accesses sensitive applications, downloads data, and attempts to register a new MFA method to maintain persistence. The threat Microsoft Entra user with multiple MFA failures (CTD-000171) detects the unusual burst of MFA failures, including the IP address, device, and location details. Security operations can quickly correlate the MFA failure burst with a suspicious sign-in and revoke sessions before the attacker fully establishes persistence. Cayosoft Guardian would have raised a threat alert early in the attack, allowing the security team to intervene before significant damage occurred.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
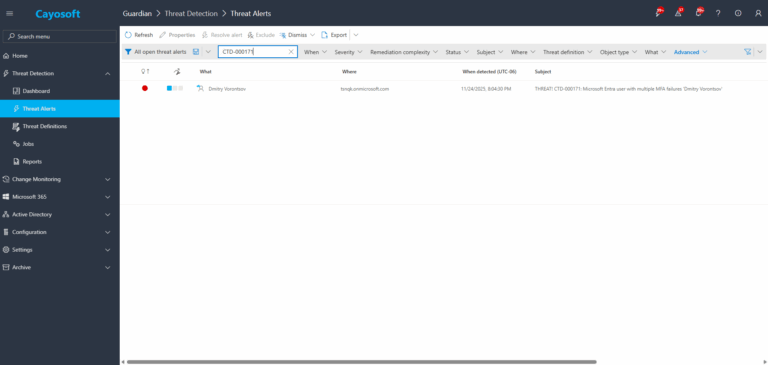
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Search for CTD-000171 or “Microsoft Entra user with multiple MFA failures”.
3.) Open any alert and Click for details (from Raise Threat Alert action).
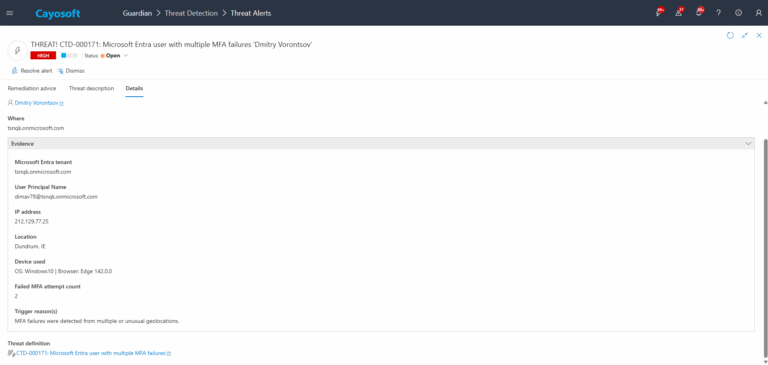
4.)Evidence:
- Microsoft Entra tenant
- User Principal Name
- IP address
- Location
- Device used
- Failed MFA attempt count
- Trigger reason(s)
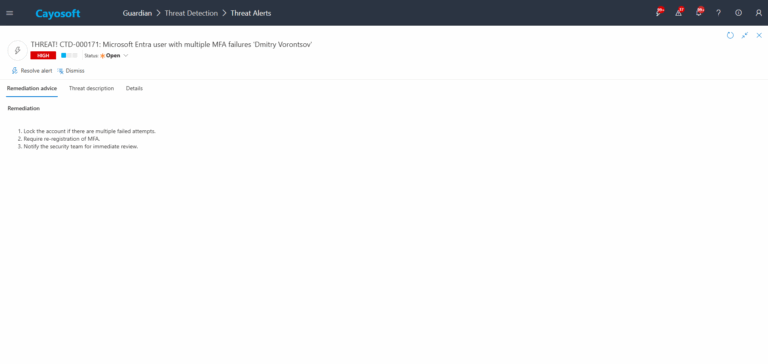
How to Prevent It
- Configure Cayosoft Guardian CTD-000171 to monitor for multiple MFA failures within a short time window and ensure the rule remains enabled.
- Set an appropriate MFA burst failure threshold and time window that balances sensitivity with noise for the organization’s user base.
- Enforce strong MFA methods (such as phishing-resistant MFA) and educate users to report unexpected MFA prompts instead of approving them.
- Implement conditional access policies that require compliant devices and restrict sign-in from risky locations or anonymous networks.
- Regularly review Guardian alerts and Entra ID sign-in logs to tune detection thresholds and refine incident response playbooks.
FAQ
Multiple MFA failures often indicate credential-based attacks such as brute force or MFA fatigue, where attackers repeatedly trigger MFA requests hoping the user will accidentally approve one. Even with MFA enabled, this pattern significantly increases the risk of unauthorized account access.
Attackers repeatedly send MFA prompts—sometimes dozens or hundreds—until the user approves one simply to stop the notifications. This accidental approval grants the attacker a valid session and often allows them to register new MFA methods, establishing persistence.
Misconfigured authenticator apps, outdated cached credentials, unstable networks, or users rapidly retrying authentication can also cause bursts of MFA failures. Administrators should validate context such as IP, device, and location before determining whether the activity is malicious.
Entra ID provides basic sign-in logs and security reports that allow manual review. Cayosoft Guardian Protector also offers free visibility features that can help highlight risky authentication behavior, but lacks the full automated detection and remediation workflows.
Yes. Cayosoft Guardian delivers continuous monitoring for MFA-failure patterns, automatically raises CTD-000171 alerts, correlates evidence across Entra ID and Microsoft 365, and provides prescriptive remediation guidance for rapid response.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Microsoft Entra user with multiple MFA failures, you reduce attack surfaces and strengthen your organization’s overall security posture.