Microsoft Entra tenant has Exchange Organization without mail-flow rules restricting attachments with executables
Cayosoft Threat Definition CTD-000134
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
This threat detects all tenants that do not have mail-flow rules restricting attachments with executables. Without these rules, a threat actor may deliver and execute code or scripts via email attachments, bypassing basic email-layer controls and increasing the likelihood of malware infections and compromises.
- Severity: Medium
- Platform: Exchange Online
- Category: Mail flow rules
- MITRE ATT&CK Tactics: Initial Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
This threat identifies Microsoft Entra tenants where the Exchange Online Organization is missing mail-flow rules that restrict executable attachments.
If executables (such as .exe, .dll, .js, .vbs, .jar, or similar formats) are allowed into user mailboxes, attackers can send malicious payloads that, when opened, execute code, drop malware, or initiate script-based attacks.
The threat definition:
- Evaluates whether the tenant has mail-flow rules that block or restrict executable file types.
- Uses a set of default file types (mandatory extensions) that should always be considered for blocking.
- Optionally considers an extended list of additional file types when configured.
- Surfaces Existing file extensions and Missing file extensions so administrators can clearly see which risky file types are not currently covered by mail-flow rules.
This is an Indicator of Exposure (IOE): it highlights a configuration gap that could be abused by attackers to gain initial access via email attachments.

Real-World Scenario
A finance user receives an email that appears to be from a trusted supplier with a subject like “Updated payment schedule” and an attachment named invoice_update.exe disguised with a PDF icon. Because the Exchange Online organization lacks mail-flow rules blocking executable attachments, the message is delivered with no warning. The user opens the attachment, which installs a remote access trojan that connects back to the attacker’s command-and-control infrastructure. The attacker then harvests credentials from the device and uses them to access internal systems, pivoting deeper into the environment. CTD-000134 would have detected that the tenant had no mail-flow rules restricting executables, enabling administrators to configure appropriate blocking controls before the phishing email reached the user.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
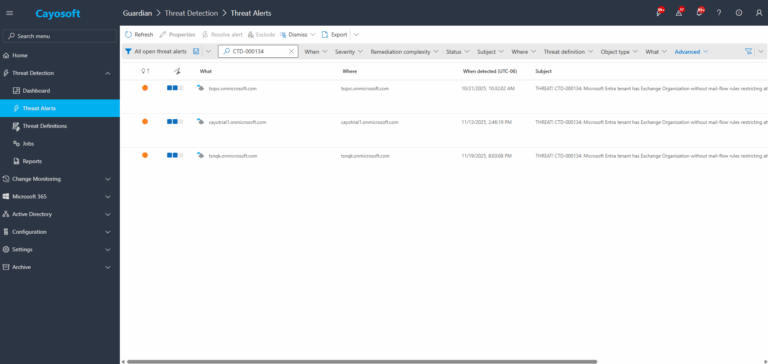
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Search for CTD-000134 or “Microsoft Entra tenant has Exchange Organization without mail-flow rules restricting attachments with executables”.
3.) Open any alert and Click for details (from Raise Threat Alert action).
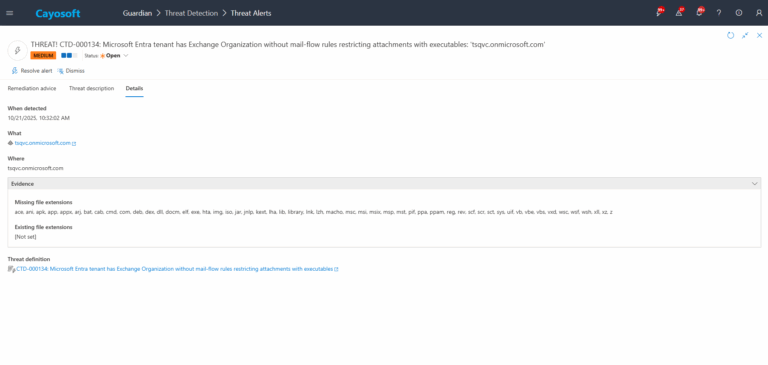
4.)Evidence:
- Missing file extensions (missingFileExtensions) – Executable or risky file types that are not currently covered by mail-flow rules.
- Existing file extensions (existingFileExtensions) – File types already covered by existing mail-flow rules.
- Compare Missing vs Existing lists and verify against your organization’s secure baseline for blocked/filtered attachment types.
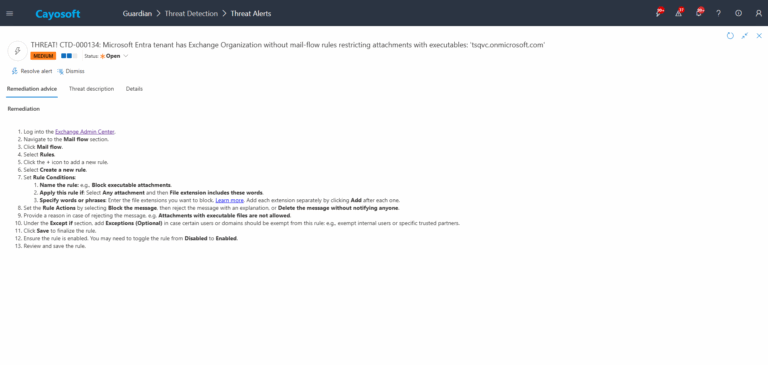
Remediation Steps
- ) Log into the Exchange Admin Center.
- ) Navigate to the Mail flow section.
- ) Click Mail flow.
- ) Select Rules.
- ) Click the + icon to add a new rule.
- ) Select Create a new rule.
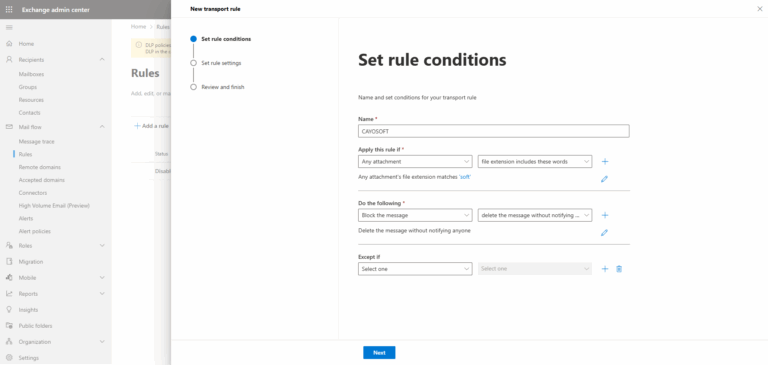
- ) Set Rule Conditions:
- ) Name the rule: e.g., Block executable attachments.
- ) Apply this rule if: Select Any attachment and then File extension includes these words.
- ) Specify words or phrases: Enter the file extensions you want to block. Learn more. Add each extension separately by clicking Add after each one.
- ) Set the Rule Actions by selecting Block the message, then reject the message with an explanation, or Delete the message without notifying anyone.
- ) Provide a reason in case of rejecting the message, e.g. Attachments with executable files are not allowed.
- ) Under the Except if section, add Exceptions (Optional) in case certain users or domains should be exempt from this rule: e.g., exempt internal users or specific trusted partners.
- ) Click Save to finalize the rule.
- ) Ensure the rule is enabled. You may need to toggle the rule from Disabled to Enabled.
- ) Review and save the rule.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Microsoft Entra tenant has Exchange Organization without mail-flow rules restricting attachments with executables. Cayosoft Guardian continuously evaluates Exchange Online configuration for missing or incomplete attachment controls and highlights which file extensions are not covered. By implementing mail-flow rules that block or restrict executable file types, optionally including the broader set of additional file types, you reduce the opportunity for attackers to gain initial access through malicious attachments.
FAQ
Executable files can run arbitrary code or scripts when opened, enabling attackers to deploy malware, establish remote access, steal credentials, or perform privilege escalation. These attachments frequently bypass user awareness and can evade endpoint defenses, making them a high-risk initial access vector.
Yes, in nearly all organizations, executable attachments should be broadly blocked. If necessary, exceptions can be defined for highly trusted and controlled accounts or processes (e.g., software distribution teams), but these exceptions should be rare and tightly governed.
Mail-flow rules add organization-specific, customizable blocking of risky file types and complement Defender’s anti-malware scanning. Microsoft’s “common attachments filter” identifies file formats frequently used in malware campaigns; these can be enforced directly in mail-flow rules for stronger protection.
Yes. Free tools such as the Exchange Admin Center, Microsoft 365 Admin Center, and Exchange Online PowerShell can help review mail-flow rules and detect unblocked risky file types.
However, these free tools do not provide continuous monitoring or automated correlation. For full coverage, organizations typically rely on paid solutions like Cayosoft Guardian, which offers real-time change tracking and visibility that free tools cannot match.
Yes. Cayosoft Guardian is a commercial platform that continuously monitors Exchange Online for configuration drift, alerts when risky attachment types aren’t blocked, and provides guided remediation steps.
Other enterprise email security products can offer partial coverage, but Guardian provides purpose-built monitoring for Microsoft ecosystems including Exchange, Entra ID, and Active Directory.
References
- Exchange Admin Center: https://admin.exchange.microsoft.com/
- Common attachments filter in anti-malware policies (Microsoft Defender for Office 365): https://learn.microsoft.com/en-us/defender-office-365/anti-malware-protection-about#common-attachments-filter-in-anti-malware-policies
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Microsoft Entra tenant has Exchange Organization without mail-flow rules restricting attachments with executables, you reduce attack surfaces and strengthen your organization’s overall security posture.