Privileged AD user synced to Microsoft Entra ID
Cayosoft Threat Definition CTD-000034
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
It is best practice from Microsoft to avoid syncing accounts to Microsoft Entra ID that have high privileges in your existing Active Directory instance.
- Severity: High
- Platform: Active Directory, Entra ID
- Category: Account protection, Privileged Access Management
- MITRE ATT&CK Tactics: Privilege Escalation
- MITRE D3FEND Tactics: User Account Permissions, Domain Account Monitoring
Description
It is best practice from Microsoft to avoid syncing accounts to Microsoft Entra ID that have high privileges in your existing Active Directory instance. A threat actor might compromise a regular user account in the tenant to get access to its privileged counterpart in the Active Directory.
Note: Cayosoft Guardian defines privileged users in Active Directory as users with adminCount=1. By design, Active Directory uses this attribute to protect members of administrative groups. According to security best practices, it is not recommended to re-use admin accounts; instead these accounts must be de-provisioned. If an account has administrative permissions, it might also obtain access to other resources using these permissions and keep this access even after it is removed from the administrative groups (see AdminSDHolder/SDProp).

Real-World Scenario
An attacker phishes a standard Entra user who has a matching identity in on-prem AD where the account is a member of Domain Admins. Because identity sync is enabled for that privileged AD user, the attacker signs into Microsoft 365 as the cloud identity and uses password reset and app consent to gain additional access. The attacker then leverages the on-prem privileges to deploy a rogue GPO and creates a stealthy replication backdoor, maintaining control even if the cloud account is disabled. Cayosoft Guardian would surface the Privileged AD user synced to Microsoft Entra ID exposure so admins can exclude the account from synchronization and de-provision the cloud object before abuse.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
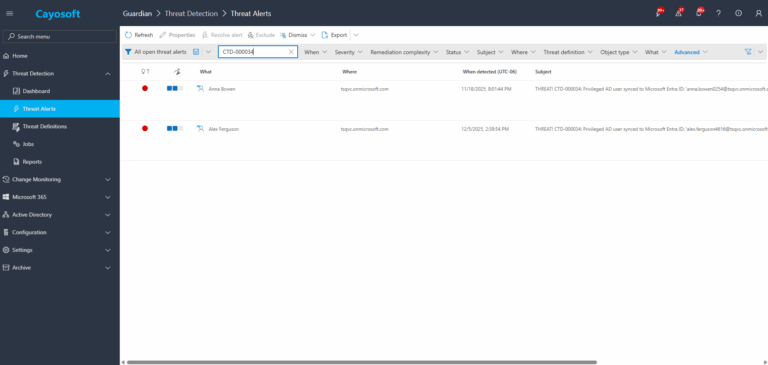
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) View All Alerts and search for CTD-000034 or Privileged AD user synced to Microsoft Entra ID.
3.) Open any alert and Click for details (from Raise Threat Alert action).
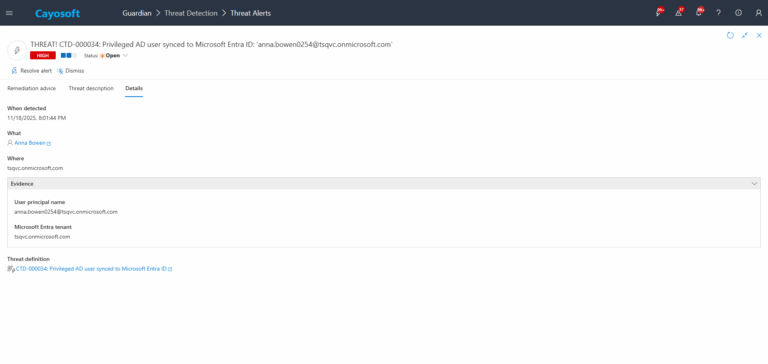
4.)Evidence:
- User principal name
- Microsoft Entra tenant
Remediation Steps
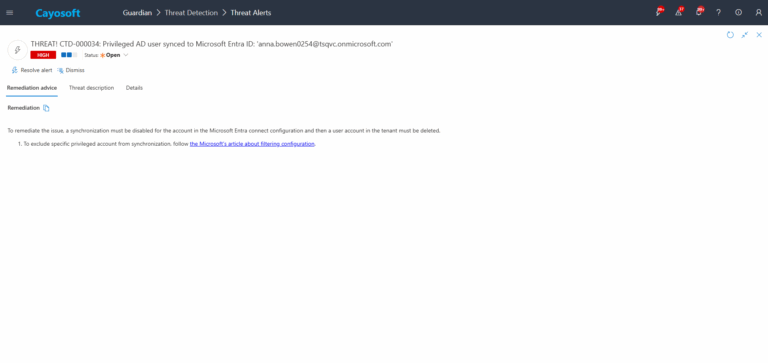
To remediate the issue, a synchronization must be disabled for the account in the Microsoft Entra connect configuration and then a user account in the tenant must be deleted.
- ) To exclude specific privileged account from synchronization, follow the Microsoft’s article about filtering configuration.
How to Prevent It
- Do not sync privileged AD accounts (adminCount=1) to Entra ID.
- Use separate, cloud-only break-glass accounts for Entra administration.
- Apply OU/group filtering in Entra Connect to exclude Tier-0/Tier-1 admin accounts.
- Periodically review for reintroduced privileged identities in the sync scope with Cayosoft Guardian.
FAQ
Because any compromise of the on-prem identity immediately exposes the cloud counterpart. Attackers can exploit cloud authentication vectors—phishing, token theft, OAuth abuse—to escalate into on-prem Tier-0 privileges.
Review the user’s AD group memberships, confirm adminCount status, validate whether the account is supposed to be synced, and inspect Entra app grants, password changes, and recent sign-ins.
Yes. Cayosoft Guardian Protector can detect AD and Entra identity risks — including synced privileged AD users — at no cost.
Yes. Cayosoft Guardian continuously monitors AD, Entra ID, Microsoft 365, and Intune, alerts on misconfigurations like privileged AD users being synced, and provides prescriptive remediation guidance.
References
- Microsoft Entra Connect filtering: https://learn.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sync-configure-filtering
- Active Directory adminCount attribute: https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-ada1/c1c2f7ca-5705-4619-9b62-527b87bf1801
- AdminSDHolder & SDProp (Microsoft Community Hub): https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/five-common-questions-about-adminsdholder-and-sdprop/ba-p/396293
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Privileged AD user synced to Microsoft Entra ID, you reduce attack surfaces and strengthen your organization’s overall security posture.