Privileged Microsoft Entra account synced from on-premise
Cayosoft Threat Definition CTD-000035
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A synced user account that is an active or eligible member of Microsoft Entra administrative roles can grant an attacker cloud admin access if the on-premises identity is compromised. Hybrid role assignment extends on-premises breach impact to Entra ID and Microsoft 365 workloads. Removing privileged roles from synced identities reduces lateral movement paths.
- Severity: High
- Platform: Active Directory, Entra ID
- Category: Account protection
- MITRE ATT&CK Tactics: Privilege Escalation
- MITRE D3FEND Tactics: Domain Account Monitoring
Description
A synchronized on-premises user with membership (active or eligible) in Microsoft Entra administrative roles increases organizational risk. Compromise of the corresponding on-premises account allows an adversary to leverage directory role privileges in Microsoft Entra and associated cloud services.

Real-World Scenario
An attacker phishes a helpdesk user whose account is synced via Entra Connect and is eligible for Privileged Role Administrator through PIM. After resetting the user’s on-prem password and waiting for sync, the attacker activates the role, grants a backdoor role assignment to a cloud-only account, and adds app credentials for persistence. Cayosoft Guardian detects that a privileged Microsoft Entra account is synced from on-premise (CTD-000035) and raises an alert before the attacker can broaden access.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
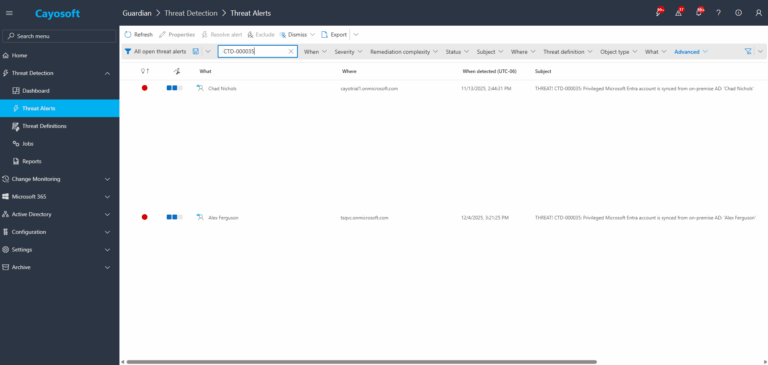
2.) Open All Alerts and search for CTD-000035 or “Privileged Microsoft Entra account synced from on-premise.”
3.) Open any alert and Click for details (from Raise Threat Alert action).
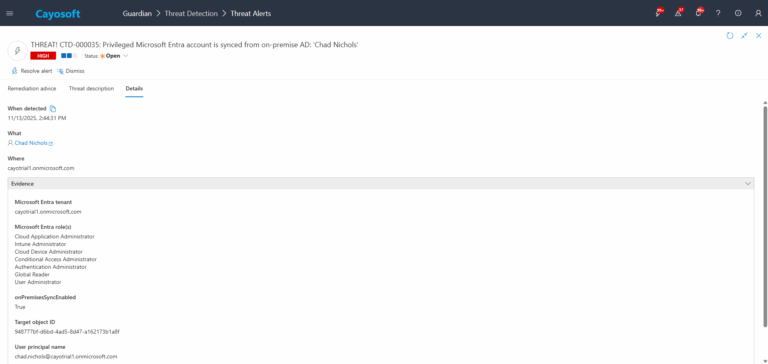
4.)Evidence:
- Microsoft Entra tenant
- Microsoft Entra role(s)
- onPremisesSyncEnabled
- Target object ID
- User principal name
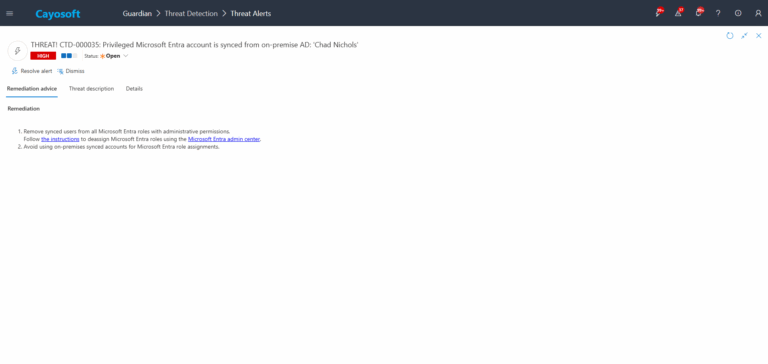
Remediation Steps
- ) Remove synced users from all Microsoft Entra roles with administrative permissions.
Follow the instructions to deassign Microsoft Entra roles using the Microsoft Entra admin center. - ) Avoid using on-premises synced accounts for Microsoft Entra role assignments.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Privileged Microsoft Entra account synced from on-premise. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Because compromising the on-premises identity instantly grants attackers access to cloud administrative roles, expanding the breach into Microsoft Entra and Microsoft 365.
Check change tickets, PIM activation logs, identity lifecycle documentation, and whether the assignment aligns with approved admin processes.
Yes. Cayosoft Guardian Protector can detect AD and Entra identity risks — including synced privileged accounts — at no cost.
Yes. Cayosoft Guardian continuously monitors AD, Entra ID, Microsoft 365, and Intune, alerts on misconfigurations like synced privileged roles, and provides prescriptive remediation guidance.
References
- Microsoft: Manage Microsoft Entra roles in the portal — https://docs.microsoft.com/en-us/azure/active-directory/roles/manage-roles-portal#assign-a-role
- Microsoft Entra admin center (Roles & administrators) — https://entra.microsoft.com/#view/Microsoft_AAD_IAM/AllRolesBlade
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Privileged Microsoft Entra account synced from on-premise, you reduce attack surfaces and strengthen your organization’s overall security