AD forest with recent changes to default security descriptor in schema
Cayosoft Threat Definition CTD-000086
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Recent changes to the schema attribute of the default security descriptor might be an indication of threat activities. Such changes can silently weaken security across newly created objects forest-wide.
- Severity: Medium
- Platform: Active Directory
- Category: Forest-wide, AD Delegation, Schema
- MITRE ATT&CK Tactics: Defense Evasion
- MITRE D3FEND Tactics: Domain Account Monitoring
Description
Recent changes to the defaultSecurityDescriptor on Active Directory object classes allow a threat actor with Schema modification rights to alter the default ACL applied to newly created objects. This can grant unauthorized access, reduce auditing, or plant long-term persistence. Because schema changes are irreversible, undoing an unwanted change may require forest recovery. These changes are rare and should always have an approved reason and documented change record.

Real-World Scenario
An attacker gains access to an account temporarily added to Schema Admins to support a migration. The attacker updates the defaultSecurityDescriptor of the user and computer classes to include a permissive ACE for a hidden group, ensuring all future accounts and machines grant that group write or replication permissions by default. Operations continue normally, but every new object is born insecure, enabling stealthy escalation and data exfiltration. Guardian detects that default security descriptors were recently modified and pinpoints the affected classes, allowing security teams to respond before the change propagates further.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
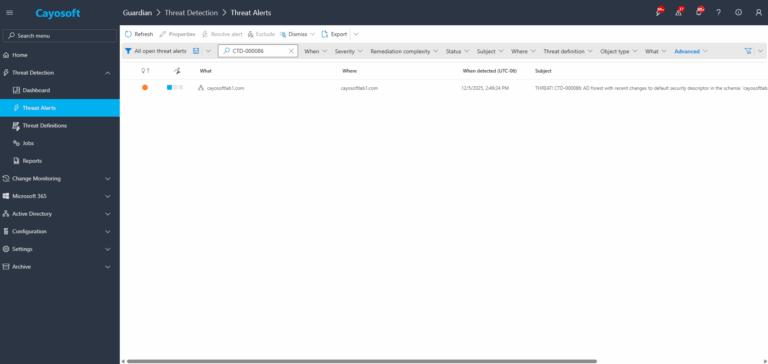
2.) Open All Alerts and search for CTD-000086 or AD forest with recent changes to default security descriptor in schema.
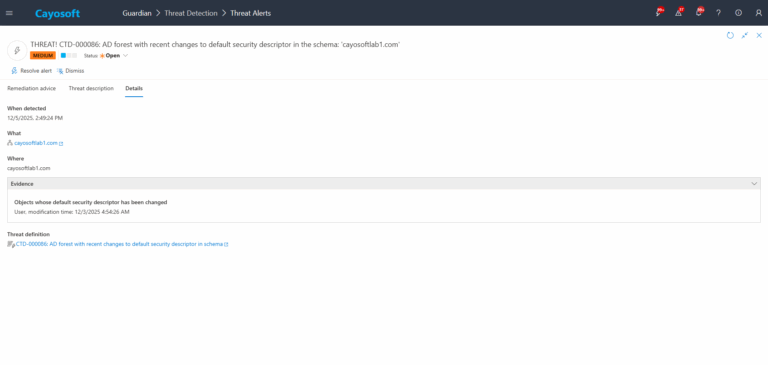
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.)Evidence:
- Objects whose default security descriptor has been changed
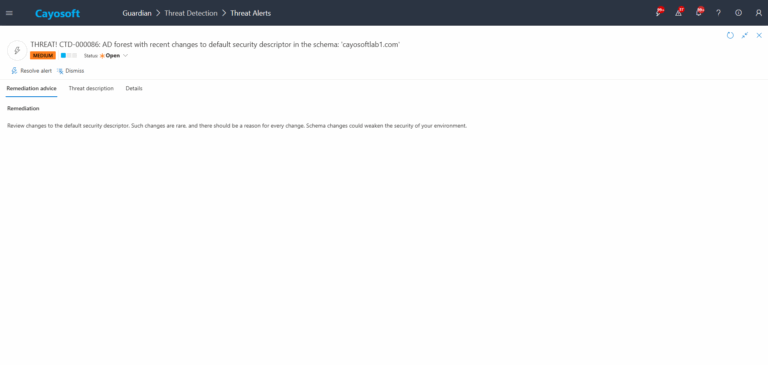
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD forest with recent changes to default security descriptor in schema.
It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
The defaultSecurityDescriptor defines the initial ACL applied to every newly created object of a specific class. A malicious change can silently introduce backdoors, grant unauthorized write/replication rights, or weaken auditing—affecting all future objects forest-wide.
Only highly controlled, temporary members of Schema Admins, ideally using just-in-time elevation, with strict auditing and documented approvals.
Yes. Cayosoft Guardian Protector can detect directory risks — including schema-related misconfigurations — at no cost.
Yes. Cayosoft Guardian continuously monitors AD, Entra ID, M365, and Intune, alerting on misconfigurations like schema descriptor changes and providing prescriptive, step-by-step remediation guidance.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD forest with recent changes to default security descriptor in schema, you reduce attack surfaces and strengthen your organization’s overall security posture.