AD domain with bulk changes of users
Cayosoft Threat Definition CTD-000065
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Bulk user changes in Active Directory can be malicious or accidental. Rapid deletions or undeletions of many user accounts can trigger outages, deny access to critical systems, and mask attacker activity.
- Severity: Medium
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Impact
- MITRE D3FEND Tactics: User Account Permissions
Description
Bulk changes might be a result of threat activities or mistakes. Deletions or modifications of AD objects can lead to service outages. NOTE: The threat rule uses a built-in lookback of 25 hours; only events occurring in this window are evaluated. The rule is configured for Number of changes = 50 within a Threshold = 30 minutes and monitors bulk deletion and bulk undeletion of users (bulk creation is disabled).

Real-World Scenario
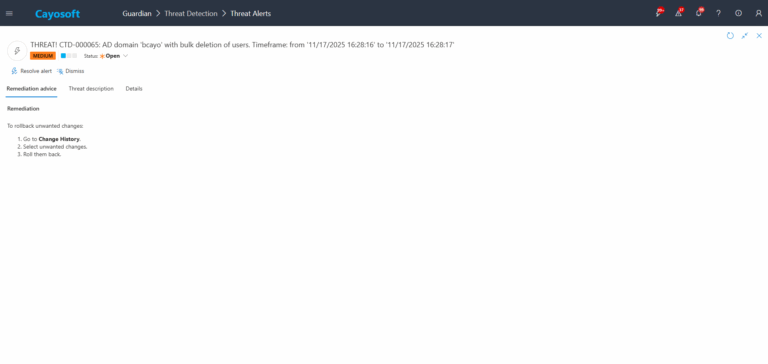
An attacker compromises a helpdesk operator account and uses automated scripts to delete 65 AD user objects in 20 minutes, targeting finance and operations. Users lose access to email, files, and line-of-business apps; service accounts tied to those users disrupt batch jobs. To hide, the attacker begins restoring a subset of users to blend the pattern. Cayosoft Guardian detects the bulk deletion/undeletion pattern within the 30-minute threshold, raises CTD-000065, and lists first/last event times with sample affected users so responders can roll back quickly.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
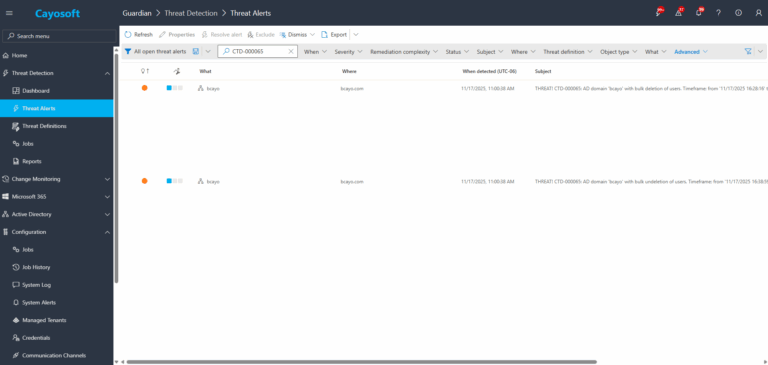
2.) Open All Alerts and search for CTD-000065 or AD domain with bulk changes of users.
3.) Open any alert and Click for details (from Raise Threat Alert action).
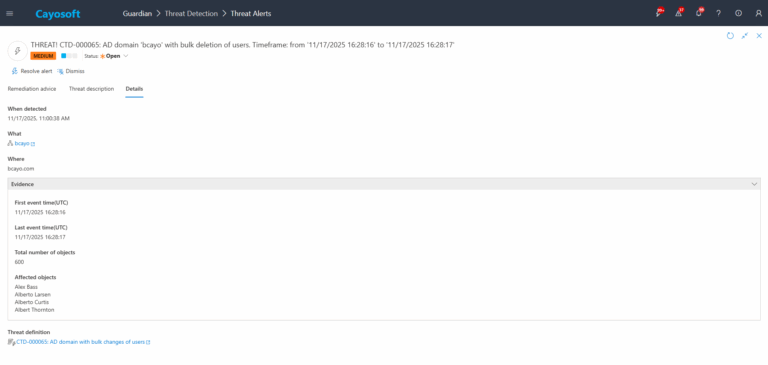
4.)Evidence:
- First event time (UTC)
- Last event time (UTC)
- Total number of objects
- Affected objects (first N per configuration)
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD domain with bulk changes of users. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for 200+ misconfigurations, providing early warning before attackers can exploit them.
FAQ
The rule monitors bulk deletion and bulk undeletion of users. Bulk creation is disabled by default but can be enabled if needed.
Yes. Large planned cleanup operations may trigger alerts. To reduce noise, temporarily adjust Number of changes, expand the Threshold, or enable alert suppression during scheduled maintenance.
Large-scale deletions can cause outages, loss of authentication, disruption of dependent services, and may be used maliciously to hide or support attacker activity.
Yes. Native tools such as Event Viewer, PowerShell, and Advanced Audit Policy can surface Event IDs related to user deletions. Free SIEM options (e.g., Elastic, Wazuh, Splunk Free) can also correlate large volumes of directory changes.
Yes. Cayosoft Guardian provides continuous monitoring, correlation, alerting, and rollback capabilities specifically for large-scale AD user changes. Other commercial platforms (e.g., Quest Change Auditor, Microsoft Defender for Identity, Semperis DSP) also monitor bulk AD modifications.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain with bulk changes of users, you reduce attack surfaces and strengthen your organization’s overall security posture.