Microsoft Entra tenant with unsecure configuration of sign-in risk policy
Cayosoft Threat Definition CTD-000102
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
An unsecure or missing sign-in risk policy allows risky authentications to proceed. Microsoft recommends requiring Microsoft Entra multifactor authentication when sign-in risk is Medium or High to remediate risk at authentication time.
- Severity: Medium
- Platform: Entra ID
- Category: Tenant-wide, Conditional Access
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
Sign-in risk policy in Conditional Access mitigates risky authentications so threat actors cannot access user accounts. Organizations should balance user experience with security posture, but Microsoft guidance is to require MFA when sign-in risk is Medium or High, allowing users to prove identity with a registered method and remediating the sign-in risk.

Real-World Scenario
An attacker replays a stolen session cookie and attempts to sign in from a new country. Identity Protection flags the attempt as Medium sign-in risk, but the tenant lacks a Conditional Access sign-in risk policy requiring MFA. The attacker bypasses scrutiny during off-hours and accesses SharePoint to exfiltrate files. Helpdesk sees scattered alerts without automatic enforcement. Cayosoft Guardian detects CTD-000102 and alerts administrators so a sign-in risk policy can force MFA and stop the attack path.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
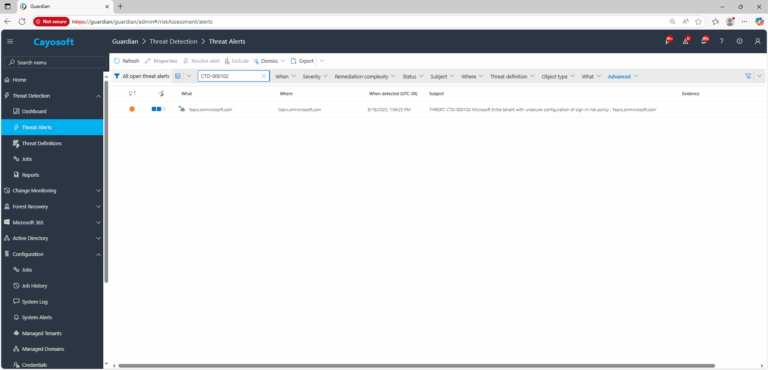
2.) Open All Alerts and search for CTD-000102 or “Microsoft Entra tenant with unsecure configuration of sign-in risk policy.”
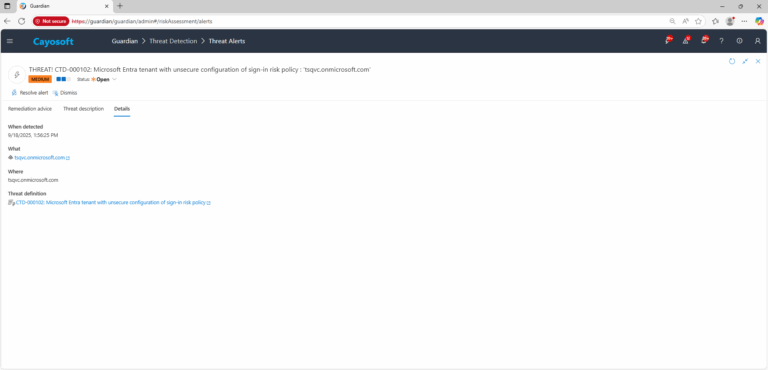
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review rule details to confirm that the sign-in risk Conditional Access policy is missing or not aligned with guidance (Medium/High → require MFA).
Remediation Steps
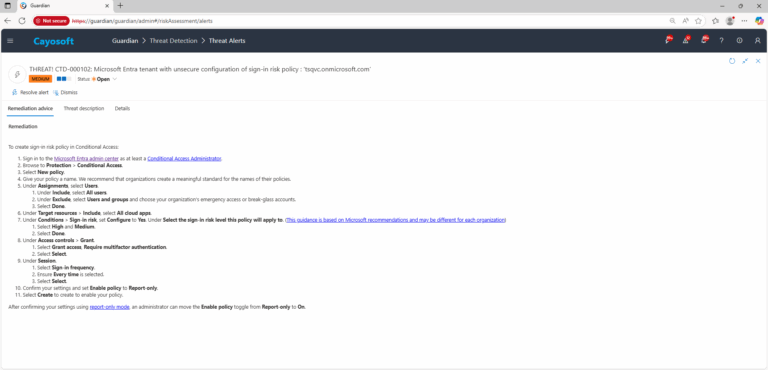
To create sign-in risk policy in Conditional Access:
- ) Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
- ) Browse to Protection > Conditional Access.
- ) Select New policy.
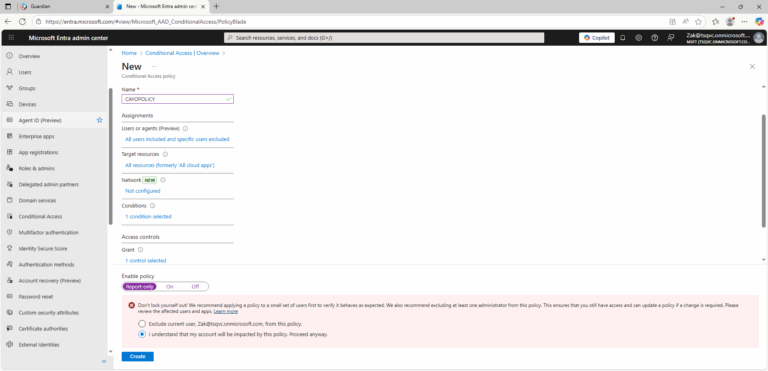
- ) Give your policy a name. We recommend that organizations create a meaningful standard for the names of their policies.
- ) Under Assignments, select Users.
- ) Under Include, select All users.
- ) Under Exclude, select Users and groups and choose your organization’s emergency access or break-glass accounts.
- ) Select Done.
- ) Under Target resources > Include, select All cloud apps.
- ) Under Conditions > Sign-in risk, set Configure to Yes. Under Select the sign-in risk level this policy will apply to. (This guidance is based on Microsoft recommendations and may be different for each organization)
- ) Select High and Medium.
- ) Select Done.
- ) Under Access controls > Grant.
- ) Select Grant access, Require multifactor authentication.
- ) Select Select.
- ) Under Session.
- ) Select Sign-in frequency.
- ) Ensure Every time is selected.
- ) Select Select.
- ) Confirm your settings and set Enable policy to Report-only.
- ) Select Create to create to enable your policy.
After confirming your settings using report-only mode, an administrator can move the Enable policy toggle from Report-only to On.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Microsoft Entra tenant with unsecure configuration of sign-in risk policy. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Without enforcement, risky authentications—such as atypical location, unfamiliar sign-in patterns, or token replay—can proceed without challenge, allowing attackers to access resources unnoticed.
It can prompt additional verification, but Microsoft recommends this requirement because it offers strong mitigation against credential replay and session hijacking with minimal operational overhead.
Yes. All users should be included except emergency/break-glass accounts. Even regular users can be targeted for risky sign-ins, and selective enforcement can create exploitable gaps.
Yes. Cayosoft Guardian Protector can detect misconfigured sign-in risk policies and other directory risks at no cost.
Yes. Cayosoft Guardian provides continuous monitoring, alerting, configuration auditing, and prescriptive remediation for sign-in risk policy issues and over 200 other AD/M365/Entra ID misconfigurations.
References
- Microsoft Entra admin center — entra.microsoft.com
- Conditional Access Administrator role permissions — learn.microsoft.com/en-us/entra/identity/role-based-access-control/permissions-reference#conditional-access-administrator
- Choosing acceptable risk levels for risk policies — learn.microsoft.com/en-us/entra/id-protection/howto-identity-protection-configure-risk-policies#choosing-acceptable-risk-levels
- Conditional Access insights and reporting (report-only mode) — learn.microsoft.com/en-us/entra/identity/conditional-access/howto-conditional-access-insights-reporting
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Microsoft Entra tenant with unsecure configuration of sign-in risk policy, you reduce attack surfaces and strengthen your organization’s overall security posture.