Stale administrative account in AD domain
Cayosoft Threat Definition CTD-000036
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Enabled administrative account that has not logged in during the specified period poses a threat to your Active Directory environment. Such an account can be abused by a former employee or a threat actor and increases the attack surface.
- Severity: Medium
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Privilege Escalation, Credential Access
- MITRE D3FEND Tactics: Domain Account Monitoring
Description
A stale admin account (still enabled but unused) can retain wide privileges and become a low-noise path for credential abuse and privilege escalation. According to the template note, privileged users are defined as adminCount=1, which by design protects members of administrative groups. Residual permissions and ACL changes can persist even after group removal due to AdminSDHolder/SDProp behavior.

Real-World Scenario
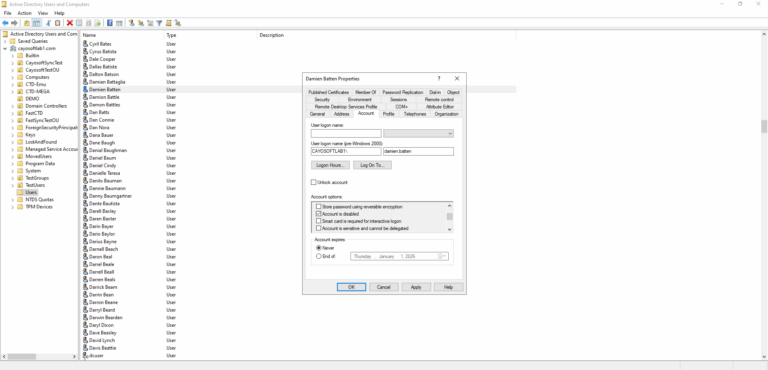
A contractor with domain admin rights leaves the organization, but the account remains enabled and unused for months. An attacker obtains the old password from a leaked vault export and authenticates during off-hours, using the account’s privileged token to dump credentials and create a hidden local admin on key servers. To avoid obvious detection, the attacker limits activity to DC replication hours and leverages built-in tools. Cayosoft Guardian flags the account as stale administrative based on last logon and privilege indicators, enabling the SOC to disable and deprovision it before further lateral movement.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
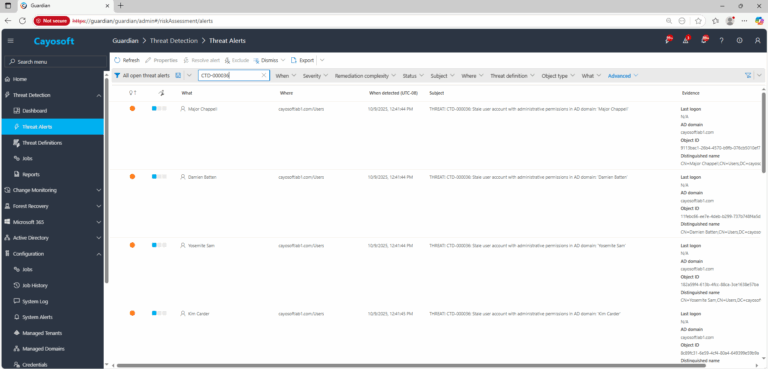
2.) View All Alerts and search for CTD-000036 or Stale administrative account in AD domain.
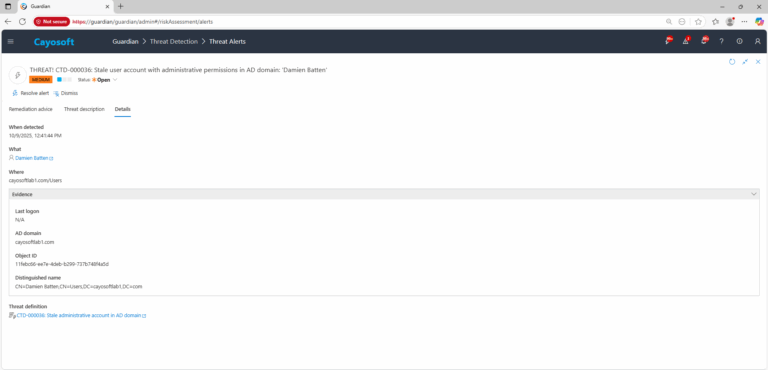
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- Last logon
- AD domain
- Object ID
- Distinguished name
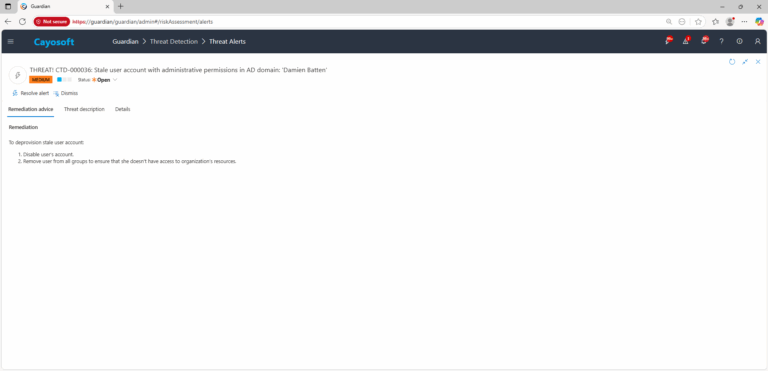
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Stale administrative account in AD domain. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
Additionally:
- Enforce JIT/PIM for admin roles; require MFA and time-bound elevation.
- Implement an admin offboarding runbook (disable → remove groups → review ACLs → delete).
- Set alerts on adminCount=1 users with no logon activity for N days; audit AdminSDHolder-affected ACLs.
- Prefer role-based access with dedicated admin accounts; prohibit shared or recycled admin identities.
FAQ
Stale accounts often retain broad privileges but lack active monitoring. Attackers can authenticate with old or leaked credentials and operate quietly because legitimate activity is not expected on unused accounts.
Not always. AdminSDHolder can leave behind protected ACLs that continue to grant elevated rights. Those ACLs must be manually reviewed and corrected.
If the domain’s ms-DS-Logon-Time-Sync-Interval is configured higher than the stale-account threshold, timestamps may not update frequently enough, causing false positives or missed stale accounts.
Yes. Cayosoft Guardian Protector can detect stale administrative accounts and other AD misconfigurations at no cost.
Yes. Cayosoft Guardian provides continuous monitoring, alerting, configuration auditing, and prescriptive remediation for stale-admin risks and more than 200 additional AD/M365 misconfigurations.
References
- Microsoft Open Specifications — adminCount attribute: https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-ada1/c1c2f7ca-5705-4619-9b62-527b87bf1801
- Microsoft Tech Community — AdminSDHolder and SDProp explained: https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/five-common-questions-about-adminsdholder-and-sdprop/ba-p/396293
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Stale administrative account in AD domain, you reduce attack surfaces and strengthen your organization’s overall security posture.