AD forest with anonymous access enabled over Name Service Provider Interface
Cayosoft Threat Definition CTD-000003
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Anonymous NSPI (Name Service Provider Interface) access to Active Directory allows unauthenticated RPC-based binds. A threat actor can query address-book data and enumerate users/groups for targeted password spraying, phishing, or privilege escalation. Disabling anonymous NSPI removes this unauthenticated reconnaissance path.
- Severity: Medium
- Platform: Active Directory
- Category: Infrastructure, Forest-wide
- MITRE ATT&CK Tactics: Initial Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
Anonymous name service provider interface (NSPI) access to AD is enabled at the forest level. NSPI serves address-book data to MAPI/Outlook clients; when anonymous access is allowed, attackers can enumerate directory information without credentials, aiding initial access and subsequent operations.

Real-World Scenario
An external attacker connects over RPC to the NSPI endpoint of a DC and performs anonymous queries to list user display names, SMTP addresses, and group memberships. Using this intel, the attacker crafts a focused password-spray and phishing campaign against high-value targets, then pivots to VPN and OWA. Cayosoft Guardian spots the dSHeuristics setting that enables anonymous NSPI and raises CTD-000003, allowing admins to remediate before the enumeration is weaponized.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
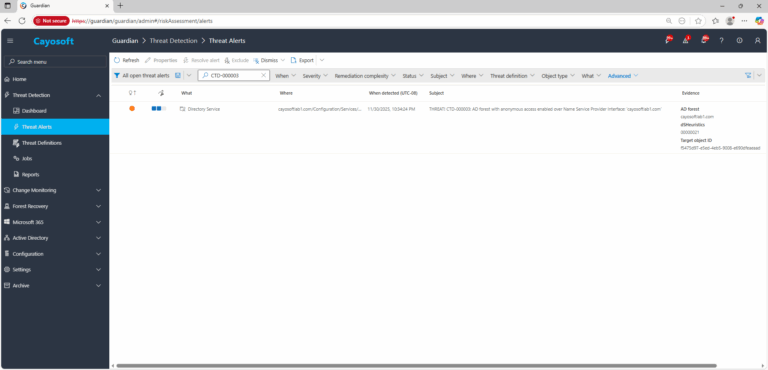
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Open All Alerts and search for CTD-000003 or “AD forest with anonymous access enabled over NSPI.”
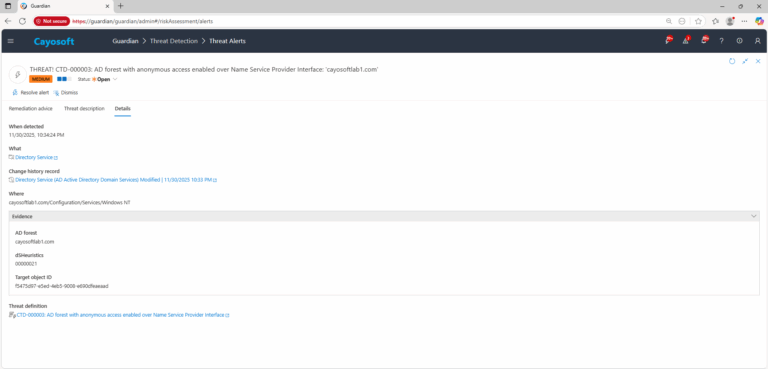
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- AD forest
- dSHeuristics
- Target object ID
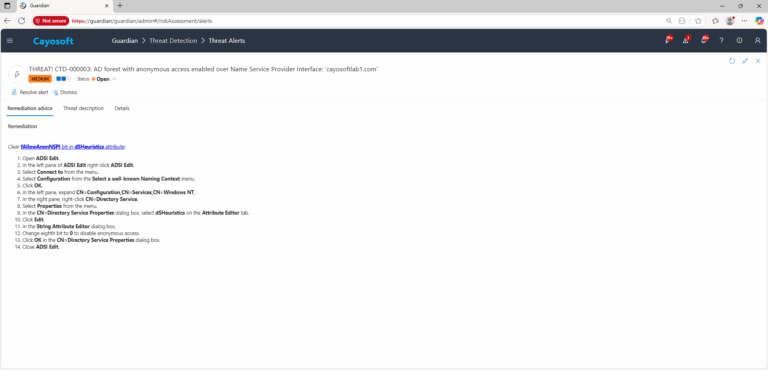
Remediation Steps
Clear fAllowAnonNSPI bit in dSHeuristics attribute:
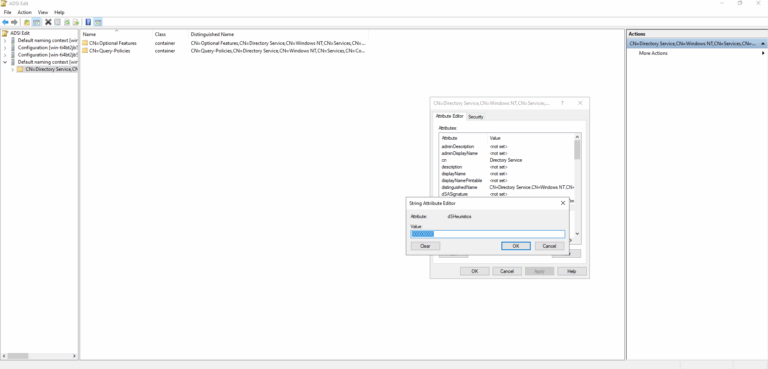
- ) Open ADSI Edit.
- ) In the left pane of ADSI Edit right-click ADSI Edit.
- ) Select Connect to from the menu.
- ) Select Configuration from the Select a well-known Naming Context menu.
- ) Click OK.
- ) In the left pane, expand CN=Configuration,CN=Services,CN=Windows NT.
- ) In the right pane, right-click CN=Directory Service.
- ) Select Properties from the menu.
- ) In the CN=Directory Service Properties dialog box, select dSHeuristics on the Attribute Editor tab.
- ) Click Edit.
- ) In the String Attribute Editor dialog box.
- ) Change eighth bit to 0 to disable anonymous access.
- ) Click OK in the CN=Directory Service Properties dialog box.
- ) Close ADSI Edit.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD forest with anonymous access enabled over NSPI. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for 200+ misconfigurations to provide early warnings and reduce attack surface.
FAQ
It allows unauthenticated enumeration of address-book data such as users, SMTP addresses, and groups, giving attackers reconnaissance data for password spraying, phishing, and privilege escalation.
The eighth character of the dSHeuristics attribute (fAllowAnonNSPI). Setting it to 0 disables anonymous NSPI.
No. Modern Outlook, MAPI, and EWS clients use authenticated access. Anonymous NSPI is not required in supported environments.
Yes. Cayosoft Guardian Protector can detect misconfigurations such as anonymous NSPI exposure at no cost.
Yes. Cayosoft Guardian provides continuous monitoring, alerting, configuration auditing, and prescriptive remediation for NSPI-related risks and 200+ other AD/M365 misconfigurations.
References
- Microsoft AD Technical Specification — dSHeuristics / fAllowAnonNSPI (attribute bit description) — https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-adts/e5899be4-862e-496f-9a38-33950617d2c5
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD forest with anonymous access enabled over NSPI, you reduce attack surfaces and strengthen your organization’s overall security posture.