Privileged Microsoft Entra account not registered for MFA
Cayosoft Threat Definition CTD-000044
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Administrative accounts without MFA are easy to compromise and ideal for persistence. A single phished or reused password can grant wide access, and without a second factor there’s little to stop credential replay or password-spray attacks.
- Severity: Critical
- Platform: Entra ID
- Category: Account protection, Privileged Access Management
- MITRE ATT&CK Tactics: Credential Access, Persistence
- MITRE D3FEND Tactics: Multi-factor Authentication
Description
An Entra ID privileged account that isn’t registered for multi-factor authentication lacks sufficient protection against modern threats. A threat actor who guesses, steals, or reuses the password can operate under elevated privileges, conceal persistence, and access sensitive resources and data without triggering additional verification challenges.

Real-World Scenario
An attacker harvests a Global Administrator’s password from a third-party breach and signs in directly to the Entra admin portal because the account has no MFA. The attacker creates a new break-glass-style user, grants it privileged roles, and sets SMTP forwarding rules in Exchange to exfiltrate alerts. Activity occurs during business hours to blend in. Cayosoft Guardian detects privileged accounts missing MFA and highlights the affected roles so responders can enforce registration and cut off access quickly.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
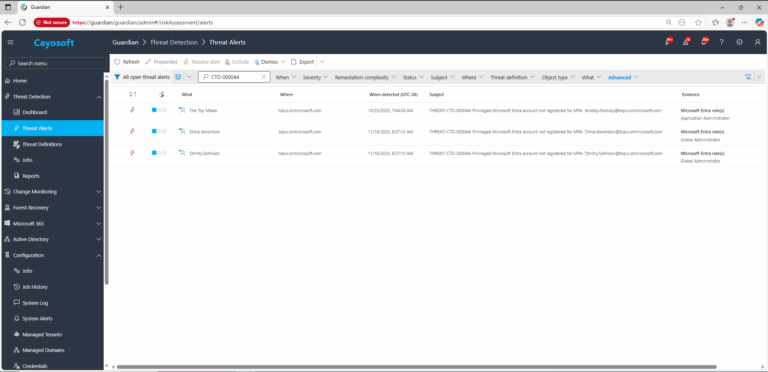
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) View All Alerts and search for CTD-000044 or Privileged Microsoft Entra account not registered for MFA.
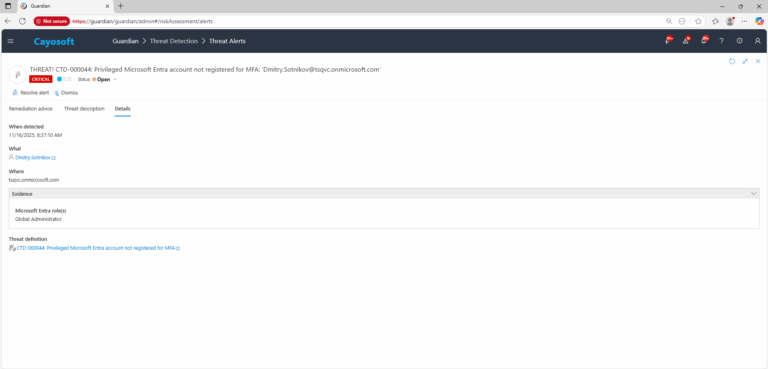
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- Microsoft Entra role(s)
Remediation Steps
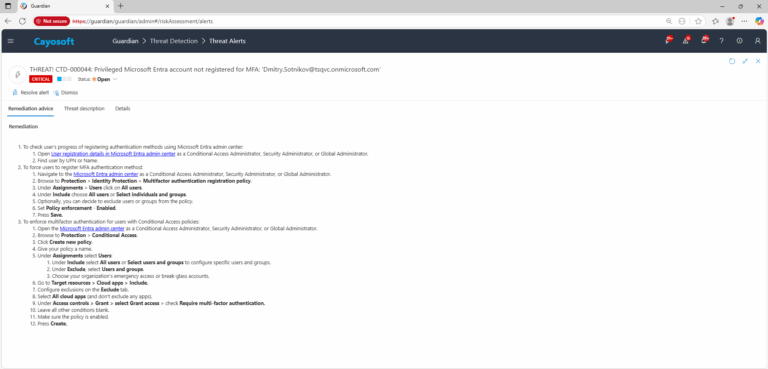
- ) To check user’s progress of registering authentication methods using Microsoft Entra admin center:
- ) Open User registration details in Microsoft Entra admin center as a Conditional Access Administrator, Security Administrator, or Global Administrator.
- ) Find user by UPN or Name.
- ) To force users to register MFA authentication method:
- ) Navigate to the Microsoft Entra admin center as a Conditional Access Administrator, Security Administrator, or Global Administrator.
- ) Browse to Protection > Identity Protection > Multifactor authentication registration policy.
- ) Under Assignments > Users click on All users.
- ) Under Include choose All users or Select individuals and groups.
- ) Optionally, you can decide to exclude users or groups from the policy.
- ) Set Policy enforcement – Enabled.
- ) Press Save.
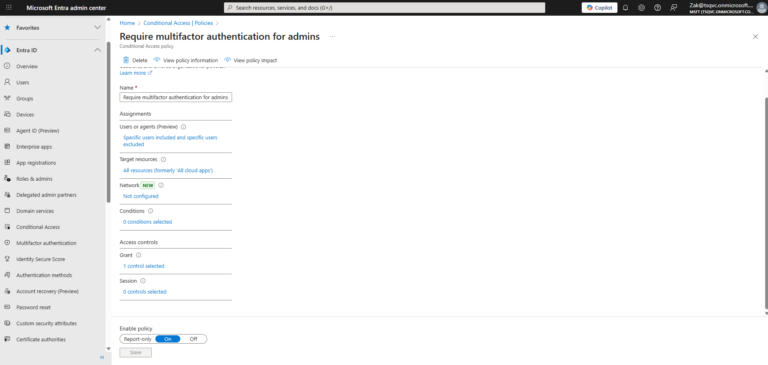
- ) To enforce multifactor authentication for users with Conditional Access policies:
- ) Open the Microsoft Entra admin center as a Conditional Access Administrator, Security Administrator, or Global Administrator.
- ) Browse to Protection > Conditional Access.
- ) Click Create new policy.
- ) Give your policy a name.
- ) Under Assignments select Users:
- ) Under Include select All users or Select users and groups to configure specific users and groups.
- ) Under Exclude, select Users and groups.
- ) Choose your organization’s emergency access or break-glass accounts.
- ) Go to Target resources > Cloud apps > Include.
- ) Configure exclusions on the Exclude tab.
- ) Select All cloud apps (and don’t exclude any apps).
- ) Under Access controls > Grant > select Grant access > check Require multi-factor authentication.
- ) Leave all other conditions blank.
- ) Make sure the policy is enabled.
- ) Press Create.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Privileged Microsoft Entra account not registered for MFA. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
Additionally:
- Default-deny for admins: Require MFA for all privileged roles; block legacy auth.
- Register before privilege: Enforce MFA registration prior to role activation (via PIM/JIT).
- Limit exemptions: Keep only two monitored break-glass accounts; exclude them in CA policies but secure and review them regularly.
- Measure & alert: Track MFA registration coverage for privileged roles and alert on regressions.
FAQ
Without MFA, a single stolen, guessed, or reused password is enough for an attacker to access admin portals, elevate privileges, create persistence, and modify cloud resources without any secondary challenge.
All high-impact roles, including Global Administrator, Privileged Role Administrator, Exchange Administrator, SharePoint Administrator, Security Administrator, and Compliance Administrator, whether active or eligible.
In the Entra admin center → Authentication methods → User registration details, where you can view registered methods per user.
Yes. Cayosoft Guardian Protector provides free detection and alerting for misconfigurations like privileged accounts without MFA.
Yes. Cayosoft Guardian delivers full detection, alerting, auditing, and guided remediation for MFA misconfigurations across Entra ID, Microsoft 365, Active Directory, and Intune.
References
- Microsoft Entra admin center (User registration details blade)
- Conditional Access policies for MFA enforcement
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Privileged Microsoft Entra account not registered for MFA, you reduce attack surfaces and strengthen your organization’s overall security posture.