Security principals with dangerous replication permissions
Cayosoft Threat Definition CTD-000050
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Security principal with replication permissions poses a threat to your Active Directory domain. Attackers who obtain Replicate Directory Changes / Replicate Directory Changes All on the domain naming context can perform DCSync to pull password hashes for any user, including domain admins.
- Severity: Critical
- Platform: Active Directory
- Category: Account protection, DC Sync
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Domain Account Monitoring, Application Configuration Hardening
Description
Security principal with replication permissions poses a threat to your Active Directory domain. A malicious actor might use security principals with Replicate Changes All and Replicate Directory Changes permissions on the domain naming context object to execute a DCSync attack and retrieve password hashes for any user in an Active Directory domain. DCSync emulates a domain controller’s replication mechanism using the native Directory Replication Service (DRS) Remote Protocol, so requests appear valid to other domain controllers.

Real-World Scenario
A compromised helpdesk account was incorrectly delegated Replicate Directory Changes All at the domain root. The attacker uses Mimikatz DCSync from a workstation to request secrets, then cracks or replays hashes to impersonate a Domain Admin. To reduce noise, the attacker performs minimal reads, stages access tokens, and clears local traces before pivoting to servers. Cayosoft Guardian (CTD-000050) would surface the misdelegation (with the container DN and effective replication permissions) so the ACE could be removed before abuse.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
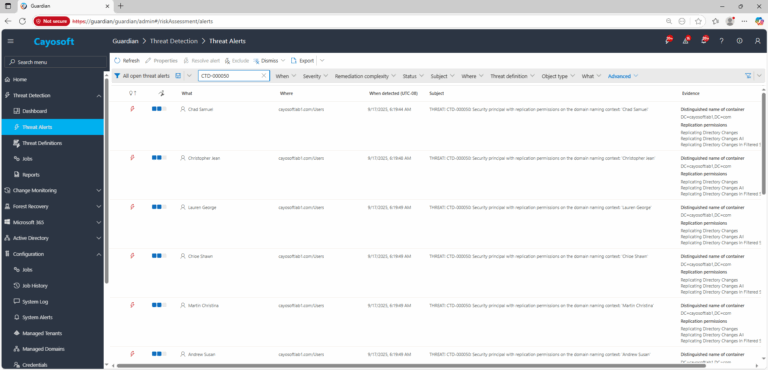
2.) Open All Alerts and search for CTD-000050 or Security principals with dangerous replication permissions.
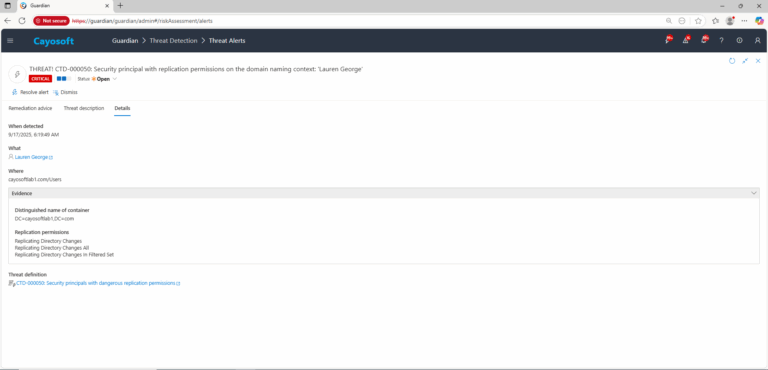
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- Distinguished name of container (containerDistinguishedName)
- Replication permissions (permissions)
Remediation Steps
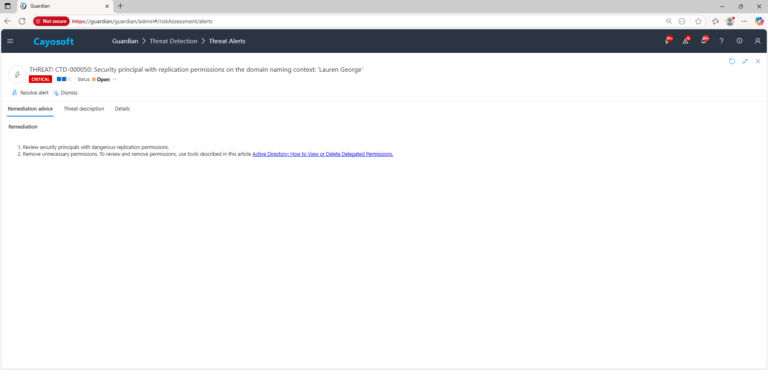
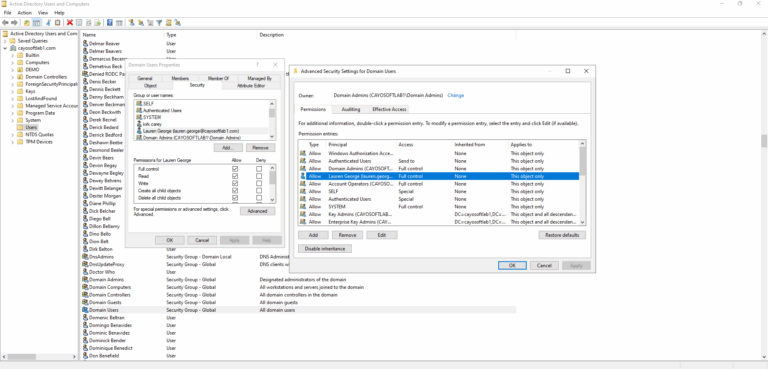
- ) Review security principals with dangerous replication permissions.
- ) Remove unnecessary permissions. To review and remove permissions, use tools described in this article Active Directory: How to View or Delete Delegated Permissions.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Security principals with dangerous replication permissions. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
The permissions Replicate Directory Changes, Replicate Directory Changes All, and Replicate Directory Changes In Filtered Set allow an attacker to request password hashes from domain controllers using the DCSync technique.
These rights let a security principal impersonate a domain controller using the Directory Replication Service (DRS) Remote Protocol. DCSync requests appear legitimate, enabling attackers to extract password hashes for any account—including Domain Admins—without needing DC access.
Only Domain Controllers and approved directory synchronization or monitoring services that explicitly require replication APIs. Regular users, helpdesk accounts, admin groups, or service accounts should never have these permissions.
Yes. Cayosoft Guardian Protector provides free detection and alerting for misconfigurations such as unauthorized replication permissions.
Yes. Cayosoft Guardian offers full detection, alerting, auditing, and step-by-step remediation guidance for dangerous replication permissions, along with continuous monitoring of Active Directory, Entra ID, Microsoft 365, and Intune.
References
- Active Directory: How to View or Delete Delegated Permissions (Microsoft TechNet Wiki): https://social.technet.microsoft.com/wiki/contents/articles/6477.active-directory-how-to-view-or-delete-delegated-permissions.aspx#Active_Directory_Users_and_Computers_console
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Security principals with dangerous replication permissions, you reduce attack surfaces and strengthen your organization’s overall security posture.