User account with old passwords
Cayosoft Threat Definition CTD-000072
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
An Active Directory user account whose password is not changed periodically can be easily compromised. Long-lived passwords enable password spraying, reuse across systems, and undetected persistence. Regular rotation shortens the window in which a stolen credential remains valid.
- Severity: Low
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Credential Access, Persistence
- MITRE D3FEND Tactics: Credential Rotation
Description
An account that has not changed its password within policy increases the chance of compromise and subsequent privilege escalation. Regular password rotation reduces the risk and effectiveness of password-based attacks by limiting credential lifetime.
Note: Cayosoft Guardian defines privileged users in Active Directory as users with adminCount=1 (used by AD to protect members of administrative groups).

Real-World Scenario
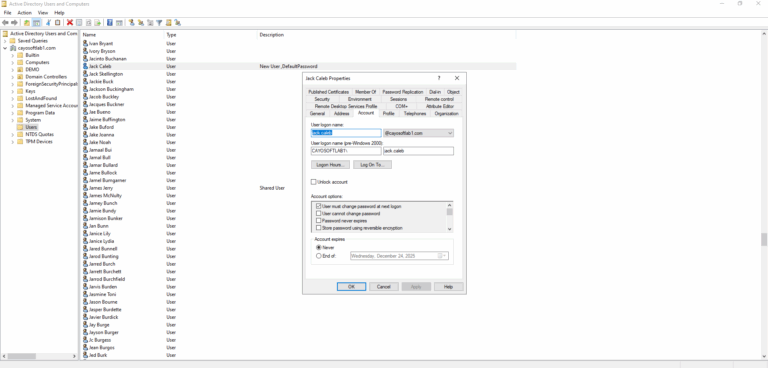
An attacker performs password spraying against VPN and OWA using a small set of common passwords. A helpdesk account whose password hasn’t changed in many months matches the attacker’s spray. With the foothold, the attacker harvests shares, dumps cached creds from a workstation, and schedules tasks to maintain access. Cayosoft Guardian flags User account with old passwords (CTD-000072), surfacing the domain and last password change so responders can rotate the credential and investigate lateral movement.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
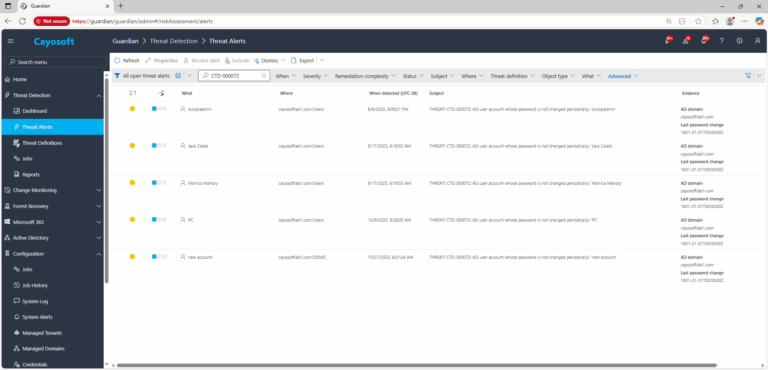
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Open All Alerts and search for CTD-000072 or “User account with old passwords.”
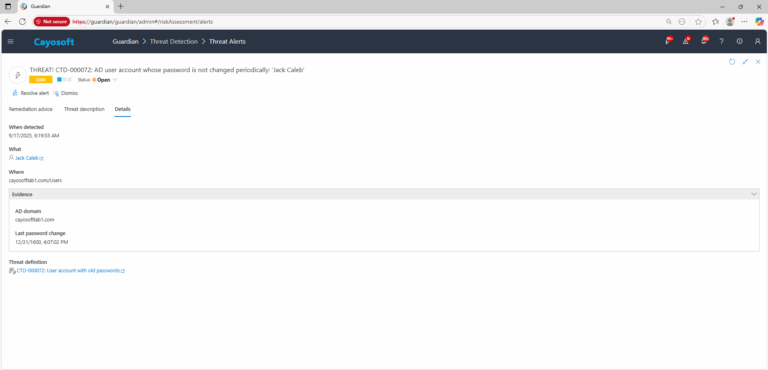
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- AD domain
- Last password change
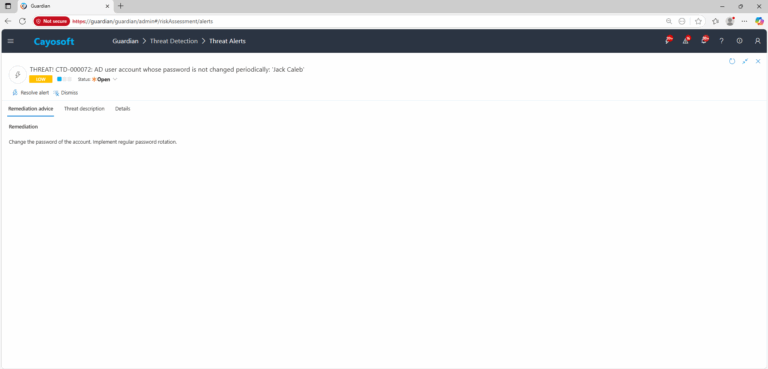
How to Prevent It
Cayosoft Guardian can proactively detect and alert on User account with old passwords. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for 200+ misconfigurations, providing early warning before attackers can exploit them.
FAQ
They greatly increase the chance of compromise via password spraying, brute-force attempts, credential reuse, or stolen-password persistence. The longer a password remains unchanged, the more opportunities an attacker has.
Abnormal sign-in patterns, unexpected Kerberos tickets, lateral movement, recent privilege elevation, or new sessions created outside normal hours.
Guardian flags users with adminCount=1 as privileged. This aligns with Active Directory’s model for protecting administrative accounts (AdminSDHolder/SDProp).
Yes—native AD tools such as PowerShell (Get-ADUser with pwdLastSet), dsquery, and open-source reporting scripts can identify old passwords. Free tools can detect but typically cannot continuously monitor, alert, correlate, or track changes historically.
Guardian continuously monitors for accounts exceeding password-age thresholds, highlights privileged users first, provides historic evidence, and alerts in real time so teams can rotate credentials before attackers exploit them.
References
- Microsoft — adminCount attribute (MS-ADA1): https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-ada1/c1c2f7ca-5705-4619-9b62-527b87bf1801
- Microsoft Community Hub — Five common questions about AdminSDHolder and SDProp: https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/five-common-questions-about-adminsdholder-and-sdprop/ba-p/396293
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like User account with old passwords, you reduce attack surfaces and strengthen your organization’s overall security posture.