AD Computer with Traces of DCShadow Attack
Cayosoft Threat Definition CTD-000048
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A detected computer account contains servicePrincipalName (SPN) values that match patterns left by DCShadow attacks using the Mimikatz tool. These changes allow an attacker to push malicious Active Directory updates while avoiding detection in native security logs.
- Severity: Critical
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Defense Evasion
- MITRE D3FEND Tactics: Domain Account Monitoring
Description
The computer object with specific values in the servicePrincipalName attribute is an indicator of attacker tool usage in your environment. The Mimikatz tool can create a shadow domain controller to inject malicious Active Directory changes, bypassing built-in security auditing. This activity leaves identifiable traces on the compromised computer account, and such changes often appear without a recorded initiator in the Who column of the Change History. Cayosoft Guardian can detect these changes even when native logging does not.

Real-World Scenario
An attacker gains a foothold on a workstation in your network and deploys Mimikatz’s DCShadow feature. They register the compromised machine as a rogue domain controller, push unauthorized changes to privileged accounts, and hide their tracks by avoiding traditional event logs. The only clues are suspicious SPN values left on the computer account. Without timely detection, the attacker could maintain persistence and escalate privileges. Cayosoft Guardian identifies these traces in near real time, raising an alert even when the initiator is unknown.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
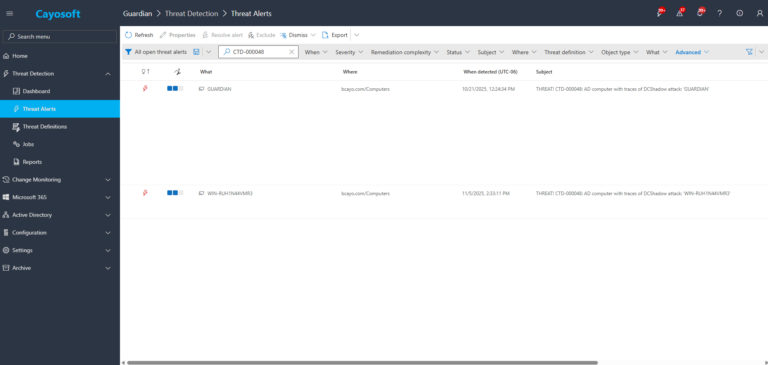
2.) View All Alerts and search for CTD-000048 or AD computer with traces of DCShadow attack.
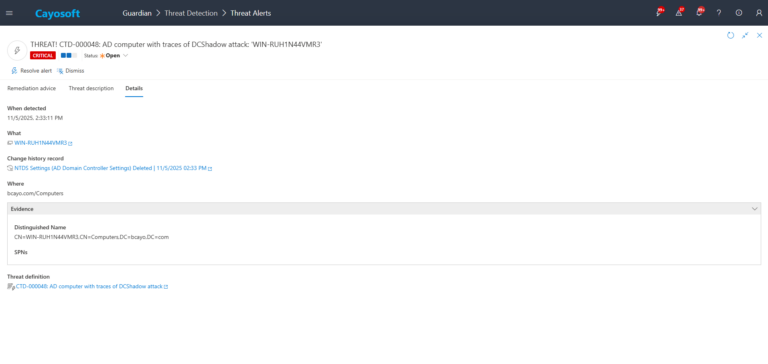
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
- Distinguished Name
- SPNs
Remediation Steps
- ) Isolate and investigate computers with possible evidence of the Mimikatz tool usage.
- ) Review suspicious changes in the Active Directory made around the time when SPN was added and where the initiator was not detected.
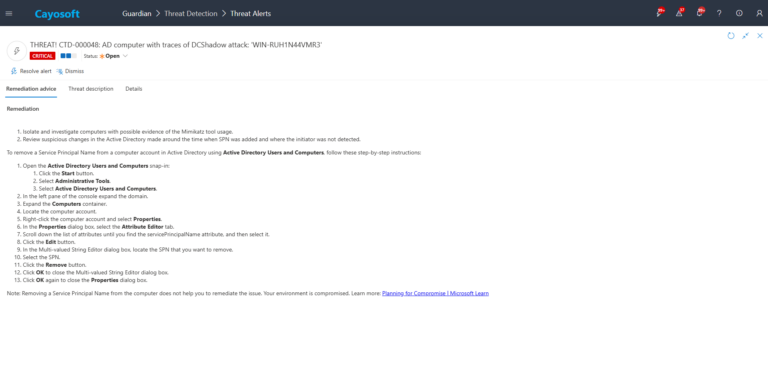
To remove a Service Principal Name from a computer account in Active Directory using Active Directory Users and Computers, follow these step-by-step instructions:
- ) Open the Active Directory Users and Computers snap-in:
- ) Click the Start button.
- ) Select Administrative Tools.
- ) Select Active Directory Users and Computers.
- ) In the left pane of the console expand the domain.
- ) Expand the Computers container.
- ) Locate the computer account.
- ) Right-click the computer account and select Properties.
- ) In the Properties dialog box, select the Attribute Editor tab.
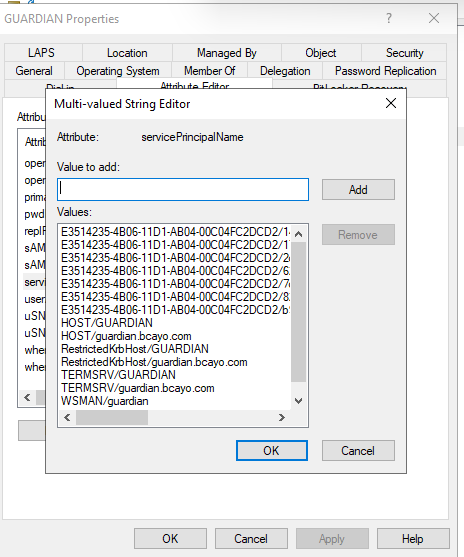
- ) Scroll down the list of attributes until you find the servicePrincipalName attribute, and then select it.
- ) Click the Edit button.
- ) In the Multi-valued String Editor dialog box, locate the SPN that you want to remove.
- ) Select the SPN.
- ) Click the Remove button.
- ) Click OK to close the Multi-valued String Editor dialog box.
- ) Click OK again to close the Properties dialog box.
Note: Removing a Service Principal Name from the computer does not help you to remediate the issue. Your environment is compromised. Learn more: Planning for Compromise | Microsoft Learn
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD computers with DCShadow attack traces. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for malicious changes and indicators of compromise, giving you early warning before attackers can escalate privileges undetected.
FAQ
A DCShadow attack is when an attacker registers a rogue domain controller and pushes unauthorized Active Directory updates that bypass native security auditing and event logs.
Because Mimikatz and similar tools register fake domain controller SPNs to perform unauthorized replication. These unusual SPN entries remain even after the attack completes and can be used to identify compromised systems.
DCShadow operations are performed through replication protocols that bypass standard event logging, so the initiator is often missing. Guardian uses change correlation and attribute pattern detection to identify such unauthorized updates.
Yes. Cayosoft Guardian Protector can detect and alert on unauthorized SPN modifications and potential DCShadow attack traces within Active Directory.
Yes. Cayosoft Guardian provides comprehensive monitoring, alerting, and rollback capabilities for suspicious SPN changes and DCShadow-related activities across Active Directory.
References
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like DCShadow attack traces, you reduce attack surfaces and strengthen your organization’s security posture.