AD object with privileged SIDs in the sIDHistory
Cayosoft Threat Definition CTD-000037
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
An Active Directory object containing privileged SIDs in its sIDHistory attribute may indicate SID History injection, a technique used by attackers to bypass normal privilege assignments and gain unauthorized administrative control.
- Severity: Critical
- Platform: Active Directory
- Category: Account protection, SID History
- MITRE ATT&CK Tactics: Defense Evasion, Privilege Escalation
- MITRE D3FEND Tactics: Domain Account Monitoring, User Account Permissions
Description
An Active Directory object with privileged SIDs in its sIDHistory attribute might be an indication of threat actor activity.
A SID (Security Identifier) uniquely identifies security principals in security descriptors and access tokens. Normally, sIDHistory is populated only during migrations.
SID History injection allows a threat actor to add privileged SIDs to regular accounts, escalating privileges. For example, adding an Enterprise Admin SID to the sIDHistory of a normal account grants effective Domain Admin rights across all domains in the forest.
NOTE: Cayosoft Guardian defines privileged users as those with adminCount=1 — an attribute that Active Directory uses to protect administrative accounts (Microsoft documentation).
Security best practice recommends de-provisioning unused admin accounts instead of reusing them, as residual privileges may persist (AdminSdHolder and SDProp reference).

Real-World Scenario
During a red team engagement, an attacker gains control of a standard user account. Using directory service tools, they inject an Enterprise Admin SID into the account’s sIDHistory.
Without appearing in privileged group membership lists, the attacker gains full administrative rights across the AD forest. This stealthy access lets them create backdoor accounts, extract sensitive files, and disable security logs without raising immediate suspicion.
Cayosoft Guardian would have detected the presence of privileged SIDs in the sIDHistory attribute, allowing security teams to investigate and remove the injected privileges before major damage occurred.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
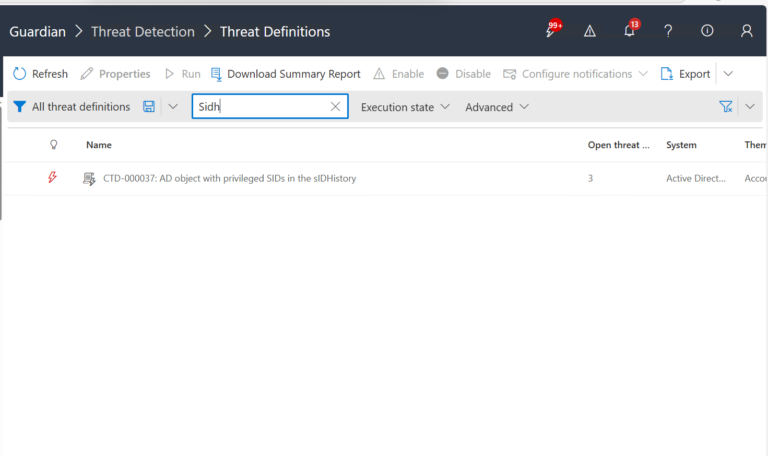
2.) View All Alerts and search for CTD-000037 or “AD object with privileged SIDs in the sIDHistory”.
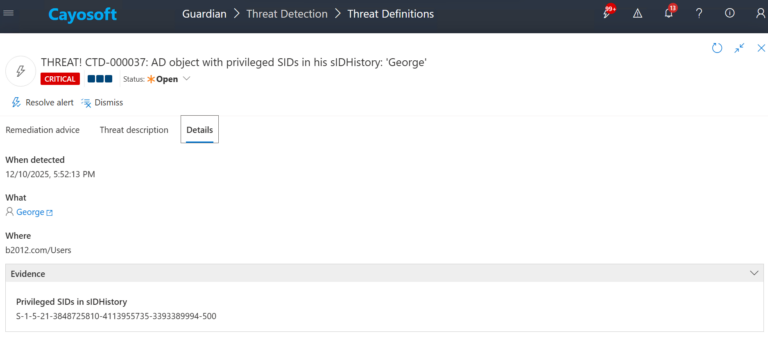
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Evidence:
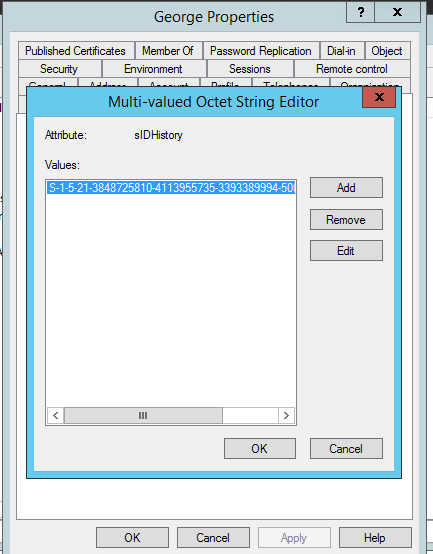
- Privileged SIDs in sIDHistory
Remediation Steps
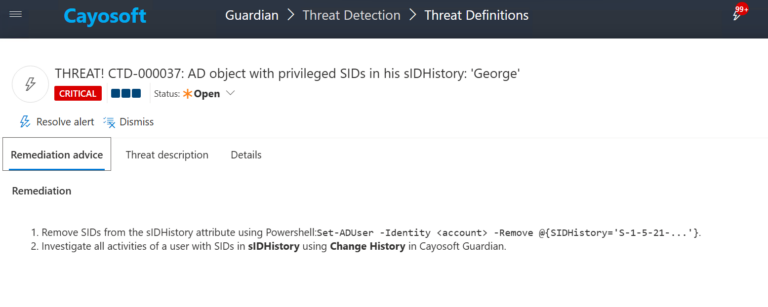
- ) Remove SIDs from the sIDHistory attribute using Powershell:
Set-ADUser -Identity <account> -Remove @{SIDHistory='S-1-5-21-...'}. - ) Investigate all activities of a user with SIDs in sIDHistory using Change History in Cayosoft Guardian.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD objects with privileged SIDs in the sIDHistory.
It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warnings before attackers can exploit them.
FAQ
It allows a regular account to inherit privileged access by adding admin-level SIDs into its sIDHistory attribute. This enables stealthy privilege escalation that bypasses standard group membership checks and monitoring tools.
Use tools like Cayosoft Guardian to continuously monitor sIDHistory attributes and flag accounts that contain privileged or unexpected SIDs. You can also script PowerShell queries to review sIDHistory values across critical accounts.
Yes. Cayosoft Guardian Protector can detect and alert on unauthorized or privileged SIDs appearing in the sIDHistory attribute.
Yes. Cayosoft Guardian provides comprehensive monitoring, alerting, and rollback capabilities to remove injected SIDs and restore secure AD configurations.
References
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like privileged SIDs in sIDHistory, you reduce attack surfaces and strengthen your organization’s overall security posture.