AD domain with built-in domain Guest account enabled
Cayosoft Threat Definition CTD-000002
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
An enabled built-in Guest account allows unauthenticated or low-trust access that adversaries can abuse to enumerate the environment and stage future attacks.
- Severity: Medium
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Discovery, Reconnaissance
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
An enabled built-in guest account poses a threat to your Active Directory environment. A threat actor can use a guest account to gather the information that can be used to plan future malicious operations.

Real-World Scenario
An attacker gains physical access to a kiosk joined to the domain. Because the domain’s built-in Guest account is enabled, the attacker signs in with minimal oversight, runs local/AD discovery tools, and collects hostnames, shares, and user lists. These findings feed password-spray attempts and targeted phishing. Cayosoft Guardian would surface CTD-000002 so defenders can disable the account before reconnaissance succeeds.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
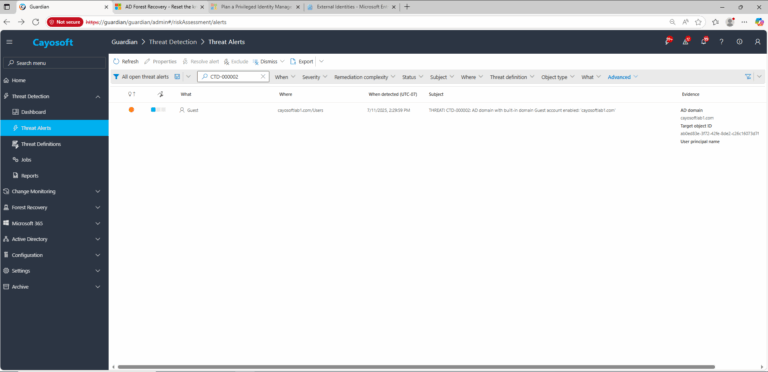
2.) View All Alerts and search for CTD-000002 or AD domain with built-in domain Guest account enabled.
3.) Open any alert and Click for details (from Raise Threat Alert action).
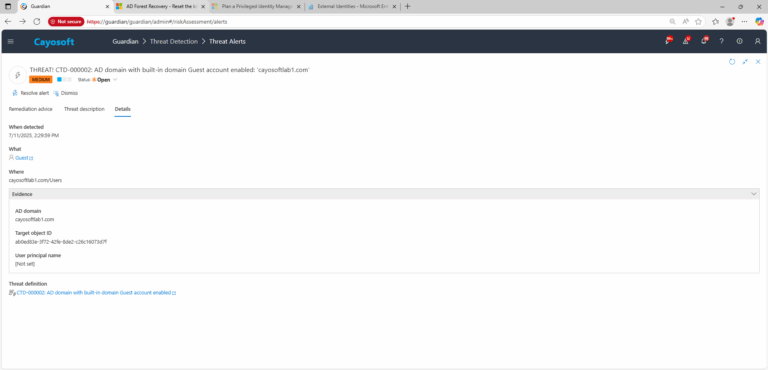
4.) Evidence:
- AD domain
- Target object ID (redacted in Guardian UI; verify in directory tools as needed)
- User principal name
Remediation Steps
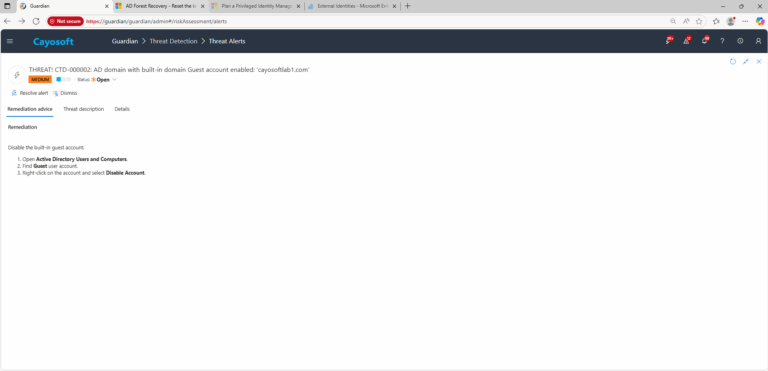
Disable the built-in guest account:
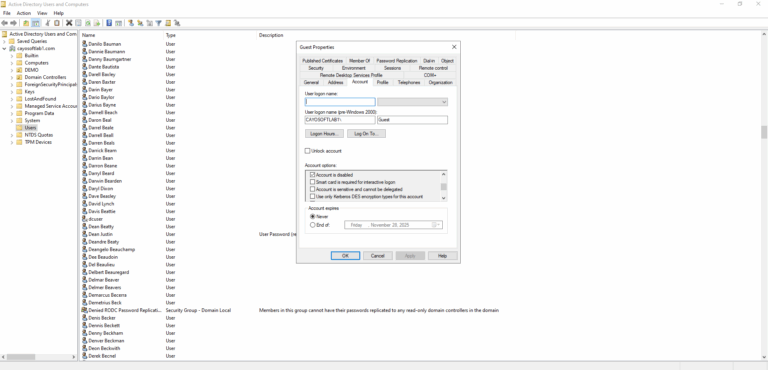
- ) Open Active Directory Users and Computers.
- ) Find Guest user account.
- ) Right-click on the account and select Disable Account.
How to Prevent It
- Keep the Guest account disabled across all domains and OUs.
- Deny local logon to Guests via GPO on servers and shared workstations.
- Use least-privilege, audited, time-bound access for legitimate visitor scenarios (e.g., separate non-domain networks).
- Cayosoft Guardian can proactively detect and alert on AD domain with built-in domain Guest account enabled. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
It allows low-trust or unauthenticated sign-ins that attackers can exploit to collect information about users, computers, and shares, helping them plan password-spray or phishing attacks.
Disabling it is critical, but you should also enforce Group Policy settings that deny local logon for Guests and consider renaming the account to make it harder to target.
In Active Directory Users and Computers, the Guest account icon will show a down arrow when disabled. You can also verify by running Get-ADUser -Identity "Guest" -Properties Enabled, which should return Enabled: False.
Yes. Cayosoft Guardian Protector can identify and alert when a built-in Guest account becomes enabled or active within your domain.
Yes. Cayosoft Guardian provides continuous monitoring, real-time detection, and automated remediation for Guest account activation across Active Directory and hybrid environments.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain with built-in domain Guest account enabled, you reduce attack surfaces and strengthen your organization’s overall security posture.