Exchange Online mailbox with Full Access permission assigned
Cayosoft Threat Definition CTD-000030
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Exchange Online mailbox with Full Access permissions assigned might indicate threat activity; a threat actor could grant access to a compromised mailbox to evade detection.
- Severity: Informational
- Platform: Exchange Online
- Category: Account protection
- MITRE ATT&CK Tactics: Defense Evasion
- MITRE D3FEND Tactics: User Account Permissions
Description
Exchange Online mailboxes with Full Access assigned allow a user or service principal to open, read, and copy mailbox contents. Threat actors commonly add or abuse Full Access on targeted mailboxes to quietly collect sensitive data, set up rules, or stage exfiltration while avoiding obvious sign-in anomalies.

Real-World Scenario
After compromising a helpdesk account, an attacker grants Full Access to the CFO’s mailbox for a low-profile user account. The attacker signs in to Outlook on the web using the low-profile account and silently reads executive email, capturing wire instructions and MFA notifications. The attacker then creates hidden inbox rules to forward finance-related messages to an external account and periodically exports mailbox folders. Cayosoft Guardian detects that Full Access was assigned and raises an alert with the trustees list, enabling rapid removal before data theft escalates.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
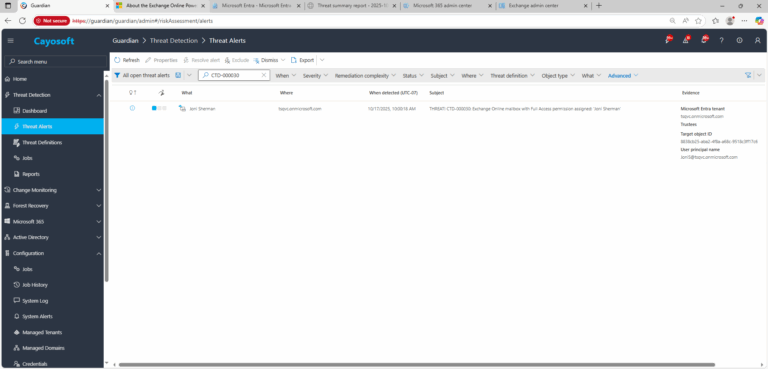
2.) Open All Alerts and search for CTD-000030 or Exchange Online mailbox with Full Access permission assigned.
3.) Open any alert and Click for details (from Raise Threat Alert action).
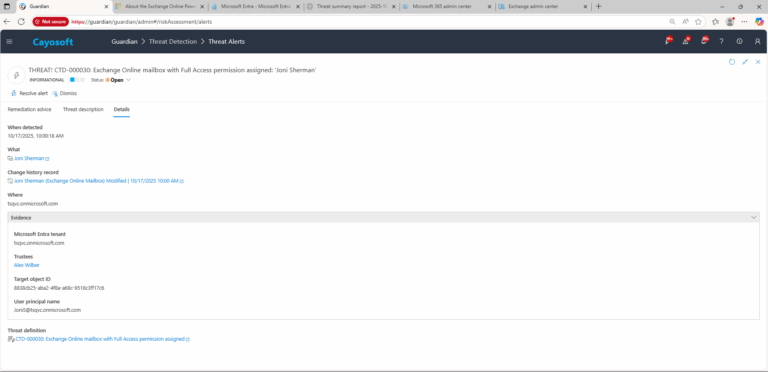
4.) Evidence:
- Microsoft Entra tenant
- Trustees
- Target object ID
- User principal name
Remediation Steps
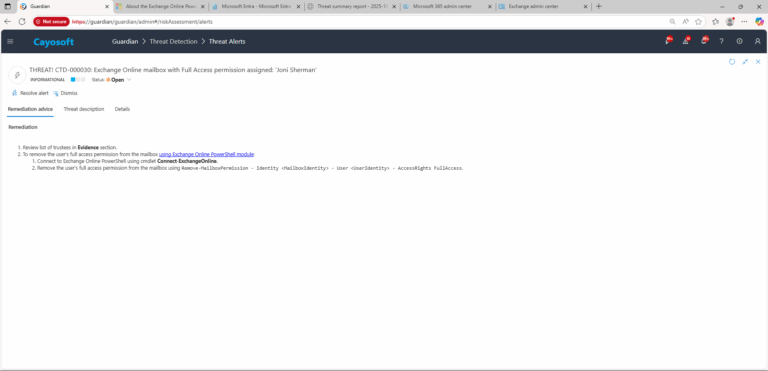
- ) Review list of trustees in Evidence section.
- ) To remove the user’s full access permission from the mailbox using Exchange Online PowerShell module:
- ) Connect to Exchange Online PowerShell using cmdlet Connect-ExchangeOnline.
- ) Remove the user’s full access permission from the mailbox using
Remove-MailboxPermission - Identity <MailboxIdentity> - User <UserIdentity> - AccessRights FullAccess.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Exchange Online mailbox with Full Access permission assigned. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
Additionally:
- Enforce least privilege and time-bound delegate access (PIM/JIT where possible).
- Require change approvals for mailbox delegate assignments; audit changes daily.
- Alert on new inbox rules, forwarding, and external recipients for sensitive mailboxes.
FAQ
Full Access allows a user or service principal to open, read, and copy mailbox contents. Threat actors can exploit these permissions to quietly access sensitive information, create hidden inbox rules, or stage data exfiltration, all while avoiding obvious sign-in alerts.
In the Cayosoft Guardian Threat Detection Dashboard, search for CTD-000030 or the issue name. The alert provides the mailbox’s trustees, target object ID, and user principal names, enabling administrators to quickly identify unapproved Full Access assignments for remediation.
Review the trustees’ business justification, then remove unneeded Full Access assignments using Remove-MailboxPermission in Exchange Online PowerShell. Re-verify mailbox permissions, audit recent sign-ins and inbox rules, and reset credentials if compromise is suspected. Enforce least privilege and time-bound delegate access where possible.
References
- Microsoft Docs — Exchange Online PowerShell (V2): https://learn.microsoft.com/powershell/exchange/exchange-online-powershell-v2
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Exchange Online mailbox with Full Access permission assigned, you reduce attack surfaces and strengthen your organization’s overall security posture.