AD domain allows unprivileged users to add computer accounts
Cayosoft Threat Definition CTD-000056
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Allowing non-admin users to create computer accounts (ms-DS-MachineAccountQuota, default 10) enables attackers with a compromised user to register fake “computer” objects and authenticate to Active Directory, establishing an initial foothold and persistence.
- Severity: High
- Platform: Active Directory
- Category: Domain-wide, Infrastructure
- MITRE ATT&CK Tactics: Initial Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
By default, the ms-DS-MachineAccountQuota attribute is set to 10, which permits any user to create up to ten computer accounts associated with their identity. If a compromised user does not already own that many devices, an attacker can create computer accounts for non-existent devices. These fake computer accounts can still perform AD authentication as if they were real. Organizations should consider setting ms-DS-MachineAccountQuota to 0 to prevent non-admin users from adding devices to the domain, blocking the simplest path for this attack’s first step and forcing adversaries toward more complex, riskier methods.

Real-World Scenario
An attacker phishes a standard employee and steals credentials. Using those rights, the attacker adds several bogus computer objects until the user’s MachineAccountQuota is exhausted. The attacker then uses the fake machine accounts to request Kerberos tickets and blend into normal workstation authentication, avoiding obvious spikes on the user account. Lateral movement follows as the attacker targets file shares and service accounts from the fake identities. Cayosoft Guardian, monitoring CTD-000056, raises an alert the moment non-admin-initiated computer creation is detected or when the domain’s MachineAccountQuota is found permissive.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
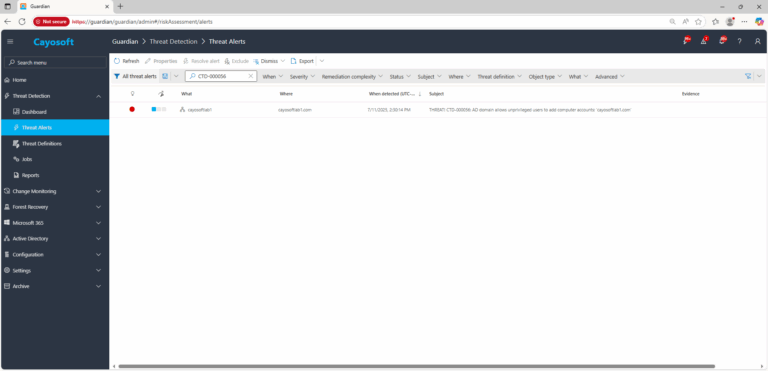
2.) View All Alerts and search for CTD-000056 or AD domain allows unprivileged users to add computer accounts.
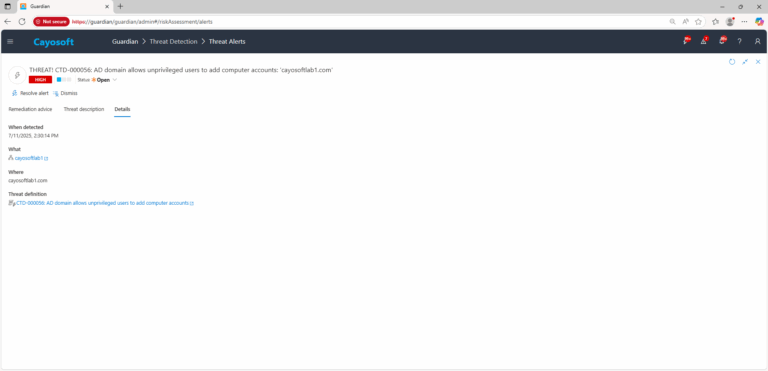
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review domain configuration and audit findings related to ms-DS-MachineAccountQuota.
Remediation Steps
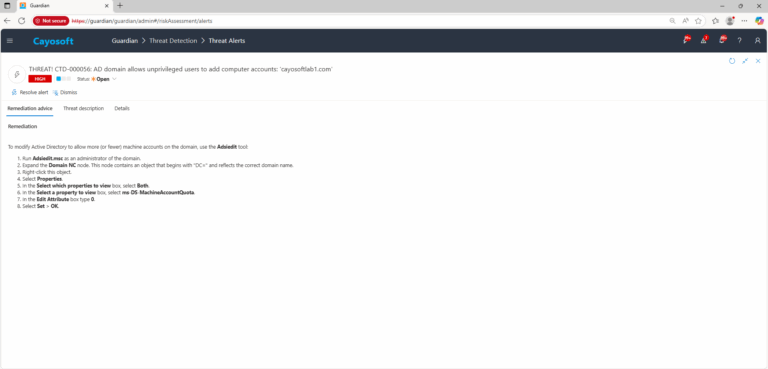
To modify Active Directory to allow more (or fewer) machine accounts on the domain, use the Adsiedit tool:
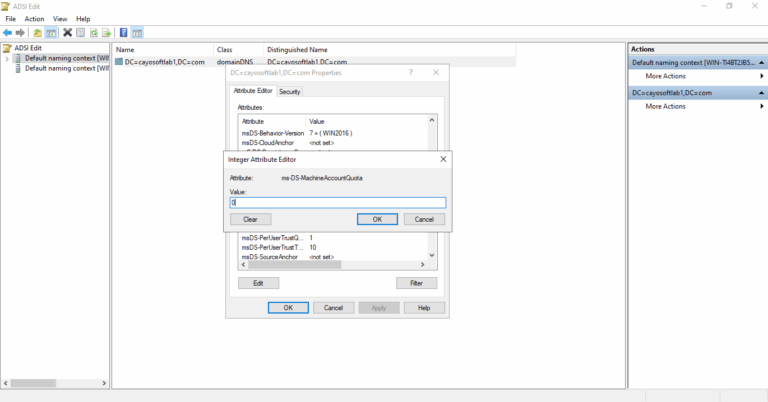
- ) Run Adsiedit.msc as an administrator of the domain.
- ) Expand the Domain NC node. This node contains an object that begins with “DC=” and reflects the correct domain name.
- ) Right-click this object.
- ) Select Properties.
- ) In the Select which properties to view box, select Both.
- ) In the Select a property to view box, select ms-DS-MachineAccountQuota.
- ) In the Edit Attribute box type 0.
- ) Select Set > OK.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD domain allows unprivileged users to add computer accounts. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for 200+ misconfigurations, providing early warning before attackers can exploit them.
- Set ms-DS-MachineAccountQuota to 0 in all production domains.
- Restrict who can join computers to the domain via delegated rights (e.g., allow only a workstation join group).
- Monitor for creation of computer objects by non-admin accounts.
- Regularly review AD audit logs for Event IDs 4741/4742 (computer account changes).
- Baseline and alert on changes to domain-level attributes.
FAQ
When ms-DS-MachineAccountQuota is greater than zero, any authenticated user can create computer objects that automatically gain domain trust and Kerberos authentication privileges. Attackers can exploit this to perform Resource-Based Constrained Delegation (RBCD) attacks, effectively impersonating privileged accounts or services without needing administrative credentials. This makes it possible to pivot laterally and access sensitive domain resources while remaining undetected under seemingly legitimate computer identities.
Setting the quota to zero centralizes computer join operations under administrative or delegated accounts, which may impact existing automation or imaging workflows that rely on user-level joins. Administrators should ensure proper delegation to a “Workstation Join” group and adjust provisioning pipelines accordingly. On the monitoring side, reducing the quota simplifies threat detection — any non-admin computer creation event (Event IDs 4741/4742) becomes a clear anomaly and should trigger immediate investigation.
Fake machine accounts can be used to obtain valid Kerberos tickets and generate consistent, domain-trusted authentication traffic that blends with legitimate workstation activity. Attackers can persist by maintaining access to these accounts, even if the original user’s credentials are reset. Moreover, machine accounts typically have long-lived passwords (30 days by default) and are often excluded from standard identity hygiene policies, making them an ideal vector for stealthy persistence and privilege escalation operations.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain allows unprivileged users to add computer accounts, you reduce attack surfaces and strengthen your organization’s overall security posture.