AD domain controller using unsecure encryption type
Cayosoft Threat Definition CTD-000088
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Allowing legacy Kerberos ciphers (e.g., RC4/DES) enables downgrade and cryptographic attacks that can expose tickets and credentials, letting attackers impersonate users and elevate privileges.
- Severity: High
- Platform: Active Directory
- Category: Kerberos, Infrastructure
- MITRE ATT&CK Tactics: Privilege Escalation, Credential Access
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
While RC4 (Rivest Cipher 4) is simple and fast, multiple vulnerabilities render it insecure—especially when the keystream prefix is not discarded or when related/non-random keys are used. A man-in-the-middle adversary can exploit weak Kerberos encryption to decrypt or manipulate authentication flows.

Real-World Scenario
An attacker with a foothold on a workstation forces Kerberos to use RC4 by requesting a service ticket to a domain controller that still allows weak ciphers. Using known RC4 weaknesses and captured traffic, the attacker recovers a service key, forges tickets, and pivots to Domain Admin. Because the domain controller’s account and policy permit legacy encryption, no password crack is needed—just a protocol downgrade. Cayosoft Guardian would flag CTD-000088 when a domain controller allows unsecure encryption types, giving the SOC time to harden policy before exploitation.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
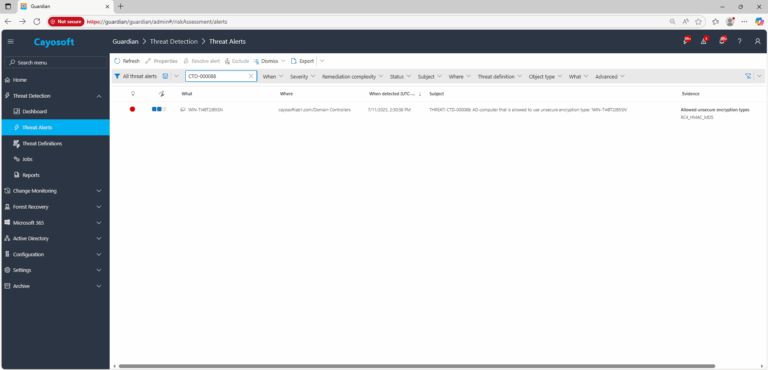
2.) Open All Alerts and search for CTD-000088 or AD domain controller using unsecure encryption type.
3.) Open any alert and Click for details (from Raise Threat Alert action).
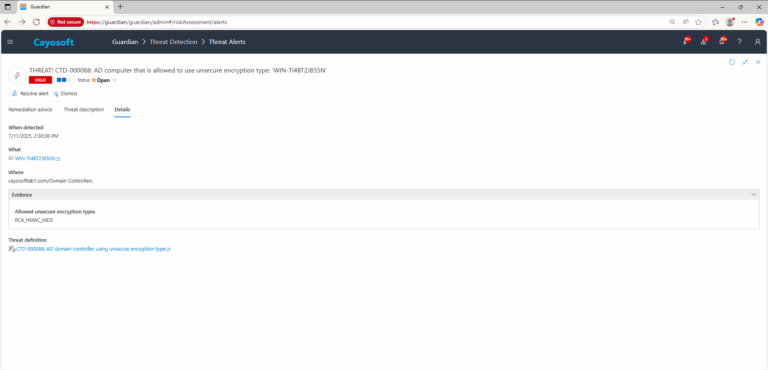
4.) Review Evidence and environment scope:
- Allowed unsecure encryption types – verify which legacy types (e.g., RC4, DES) are reported.
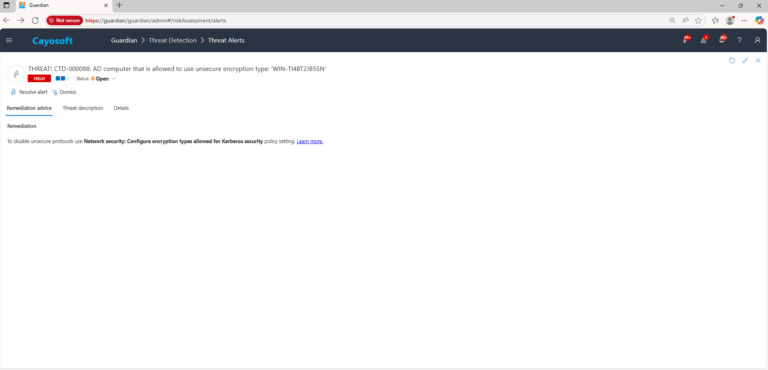
Remediation Steps
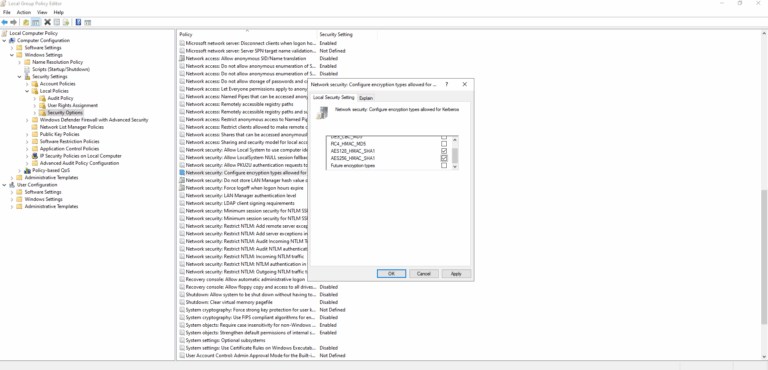
To disable unsecure protocols use Network security: Configure encryption types allowed for Kerberos security policy setting. Learn more.
How to Prevent It
- Standardize on AES for Kerberos across domain controllers, servers, and service accounts.
- Prohibit RC4/DES via GPO (Network security: Configure encryption types allowed for Kerberos).
- Rotate keys/passwords for computer and service accounts after disabling legacy ciphers to ensure AES keys are created.
- Continuously monitor for objects advertising legacy msDS-SupportedEncryptionTypes values.
- Cayosoft Guardian can proactively detect and alert on AD domain controller using unsecure encryption type. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Legacy ciphers like RC4 and DES are cryptographically weak and can be exploited through downgrade or brute-force attacks. When domain controllers accept these ciphers, attackers can capture Kerberos traffic, recover service keys, and forge authentication tickets, enabling credential theft and privilege escalation without cracking passwords.
Administrators should use Group Policy to configure Network security: Configure encryption types allowed for Kerberos, disabling legacy options like RC4_HMAC_MD5 and DES_CBC_CRC/MD5 while allowing only AES128_HMAC_SHA1 and AES256_HMAC_SHA1. After applying the policy, restart the KDC service or reboot DCs and verify AES-only encryption in Kerberos logs or with monitoring tools like Cayosoft Guardian.
Enforce AES as the standard across all domain controllers and service accounts, rotate passwords to regenerate AES keys, and continuously monitor for objects still advertising legacy encryption types. Cayosoft Guardian can automatically detect and alert when a domain controller reverts to or allows insecure encryption types, preventing unnoticed regression.
References
- Network security: Configure encryption types allowed for Kerberos — Microsoft: https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/network-security-configure-encryption-types-allowed-for-kerberos
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain controller using unsecure encryption type, you reduce attack surfaces and strengthen your organization’s overall security posture.