AD domain without group policy restricting anonymous enumeration of SAM accounts and shared resources
Cayosoft Threat Definition CTD-000163
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
In an Active Directory domain without a policy to restrict anonymous enumeration, an unauthenticated user can list account names and shared resources and then use that information for password guessing or social engineering.
- Severity: Medium
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Initial Access, Discovery, Credential Access
- MITRE D3FEND Tactics: D3-ACH (Application Configuration Hardening)
Description
When Group Policy does not restrict anonymous enumeration of SAM accounts and network shares, unauthenticated callers can query user and share lists. The exposure expands the attack surface for password spraying, phishing, and targeted social engineering. Applying the Network access: Do not allow anonymous enumeration of SAM accounts and shares policy ensures only authenticated users can retrieve these details. Note that enforcing this policy may affect operations in one-way trust scenarios and will block anonymous browsing of file/print shares until users authenticate.

Real-World Scenario
An external attacker connects over VPN to a misconfigured domain and, without credentials, enumerates user and share lists from a file server. Using harvested usernames, the attacker launches a low-and-slow password spray that compromises a helpdesk account. With the foothold, the attacker queries additional shares to map sensitive paths and pivots to an application server. Cayosoft Guardian raises CTD-000163 early, prompting administrators to enforce the GPO and stop anonymous enumeration before credentials are abused.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
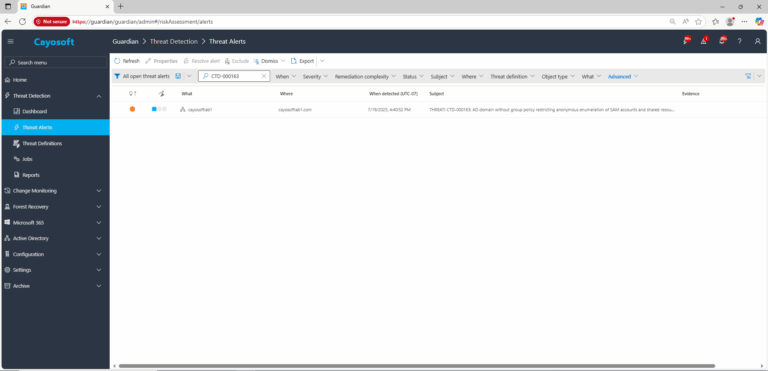
2.) Open All Alerts and search for CTD-000163 or AD domain without group policy restricting anonymous enumeration of SAM accounts and shared resources.
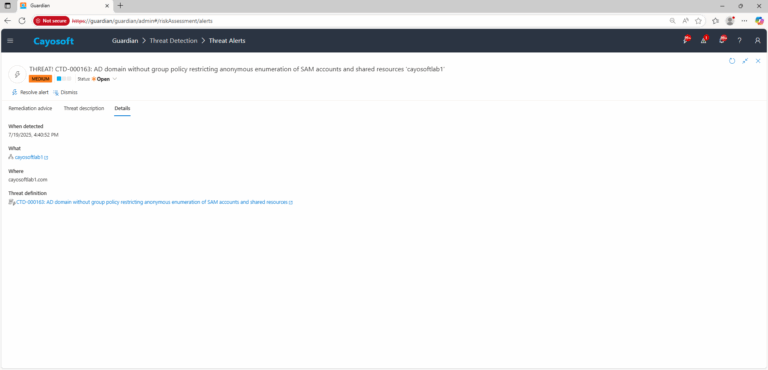
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review alert context (What/Type/Where/When/Who/Severity/Threat definition) to confirm the domain is missing the restriction.
Remediation Steps
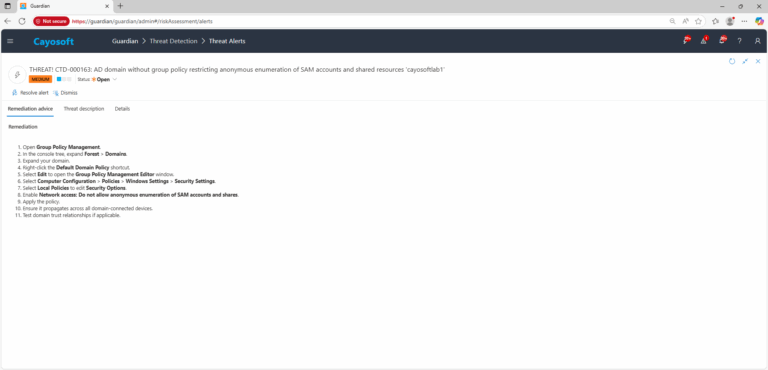
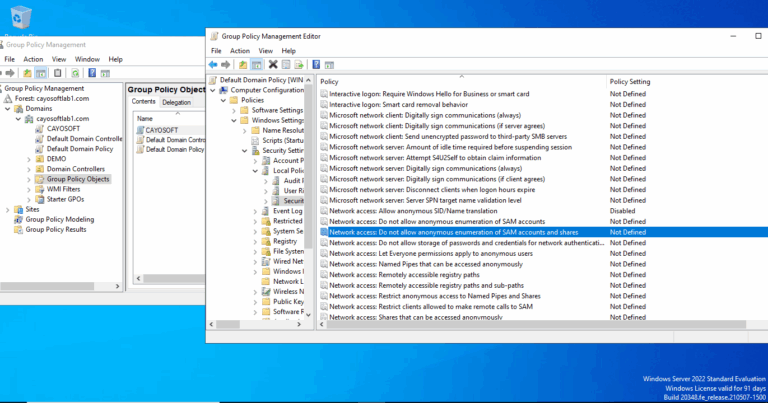
- ) Open Group Policy Management.
- ) In the console tree, expand Forest > Domains.
- ) Expand your domain.
- ) Right-click the Default Domain Policy shortcut.
- ) Select Edit to open the Group Policy Management Editor window.
- ) Select Computer Configuration > Policies > Windows Settings > Security Settings.
- ) Select Local Policies to edit Security Options.
- ) Enable Network access: Do not allow anonymous enumeration of SAM accounts and shares.
- ) Apply the policy.
- ) Ensure it propagates across all domain-connected devices.
- ) Test domain trust relationships if applicable.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD domain without group policy restricting anonymous enumeration of SAM accounts and shared resources. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Anonymous enumeration allows unauthenticated users to list domain accounts and shared network resources without needing valid credentials. Attackers can use this information to perform password spraying, phishing, or targeted social engineering. By leaving this unrestricted, you expose valuable reconnaissance data that helps adversaries move from initial access to credential compromise.
This Group Policy enforces authentication before any user can retrieve SAM account names or browse shared resources. Once enabled, it blocks null sessions and anonymous RPC calls that could otherwise list users and shares. As a result, only authenticated sessions can perform enumeration, effectively closing off a common reconnaissance path used in early-stage attacks.
While enabling this policy strengthens security, it can affect certain legacy or cross-domain operations—particularly one-way trusts or older applications relying on anonymous access to shares. Administrators should test the policy in a controlled environment first, validate all trust relationships, and ensure service accounts or applications authenticate properly before enforcing the change domain-wide.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like AD domain without group policy restricting anonymous enumeration of SAM