Insufficient Active Directory domain controller auditing policy configuration
Cayosoft Threat Definition CTD-000148
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Weak or missing domain controller (DC) audit policy leaves gaps in visibility for credential theft, DC manipulation, and lateral movement. Without reliable DC logs, defenders cannot promptly detect or investigate attacks that can escalate to full domain compromise.
- Severity: Medium
- Platform: Active Directory
- Category: Infrastructure
- MITRE ATT&CK Tactics: Defense Evasion
- MITRE D3FEND Tactics: Application Configuration Hardening
Description
This threat checks whether your organization has sufficient auditing settings for AD domain controllers, which helps organizations alert on suspicious activity that could lead to lateral movement and privilege escalation, including a complete domain compromise.

Real-World Scenario
An attacker compromises a helpdesk account and abuses unconstrained delegation to harvest a DC computer ticket. Because DC auditing for Account Logon and Directory Service Access isn’t enabled for both success and failure, critical Kerberos and directory operations are not recorded. The attacker modifies group memberships and GPOs to expand access and clears limited logs to hide traces. Incident response cannot reconstruct the timeline due to incomplete auditing. Cayosoft Guardian highlights the insufficient DC audit configuration and raises CTD-000148 so teams can harden auditing before and during the intrusion.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
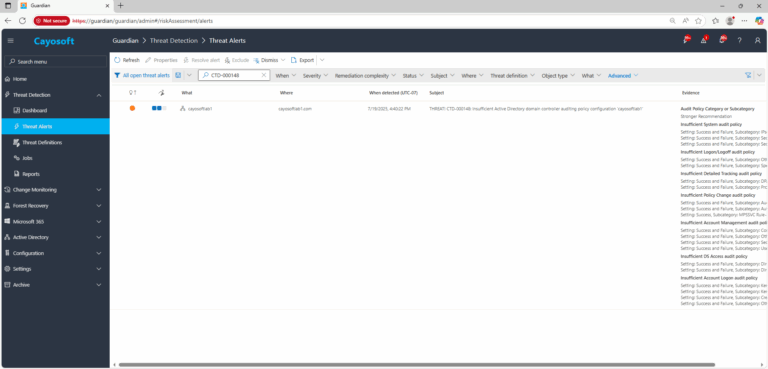
2.) View All Alerts and search for CTD-000148 or Insufficient Active Directory domain controller auditing policy configuration.
3.) Open any alert and Click for details (from Raise Threat Alert action).
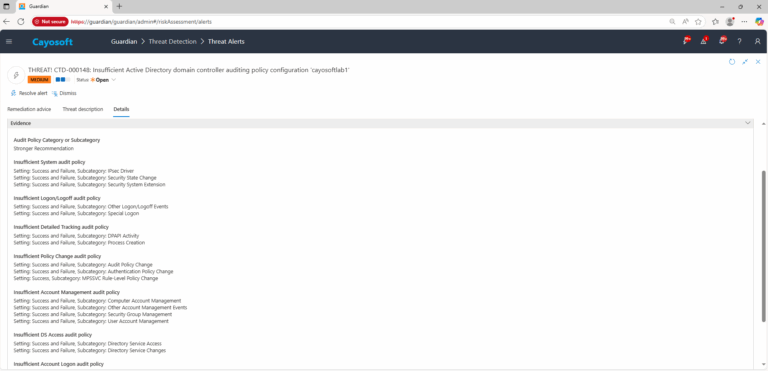
4.) Review Evidence and compare current DC audit subcategory settings against recommended baselines (enable success and failure where indicated). If Stronger recommendation for audit settings is enabled in the rule, apply the stronger profile.
Evidence (fields)
- Audit Policy Category or Subcategory (auditpol)
- Insufficient System audit policy (auditpolSystem)
- Insufficient Logon/Logoff audit policy (auditpolLogonLogoff)
- Insufficient Detailed Tracking audit policy (auditpolDetailedTracking)
- Insufficient Policy Change audit policy (auditpolPolicyChange)
- Insufficient Account Management audit policy (auditpolAccountManagement)
- Insufficient DS Access audit policy (auditpolDSAccess)
- Insufficient Account Logon audit policy (auditpolAccountLogon)
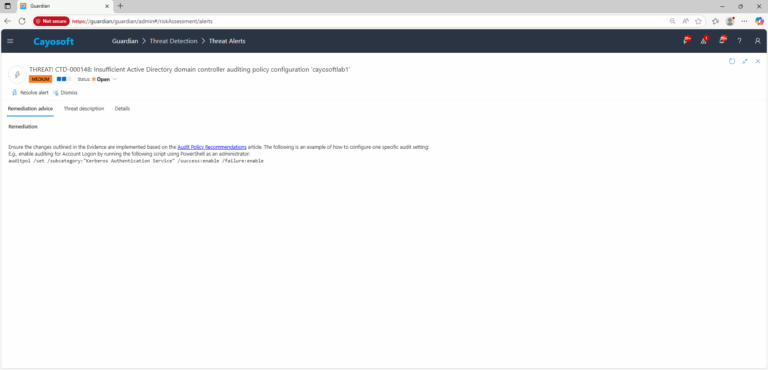
Remediation Steps
Ensure the changes outlined in the Evidence are implemented based on the Audit Policy Recommendations article. The following is an example of how to configure one specific audit setting:
E.g., enable auditing for Account Logon by running the following script using PowerShell as an administrator:auditpol /set /subcategory:"Kerberos Authentication Service" /success:enable /failure:enable
How to Prevent It
Cayosoft Guardian can proactively detect and alert on dangerous ACLs on DFSR settings objects. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
It warns that dangerous ACLs on DFSR-GlobalSettings objects can let attackers modify SYSVOL replication settings, leading to unauthorized Group Policy propagation and potential domain-wide compromise.
Active Directory administrators and security teams should regularly review and secure permissions on DFSR-GlobalSettings to prevent attackers from manipulating replication or Group Policy Objects.
They can use continuous monitoring tools like Cayosoft Guardian to detect dangerous ACL changes early and apply strict permission controls to safeguard SYSVOL replication integrity.
References
- Microsoft – DFSR Overview
Final Thought
Securing SYSVOL replication settings is critical to maintaining the integrity of Group Policy. By locking down DFSR-GlobalSettings permissions, you prevent attackers from injecting malicious policies that can silently take control of your environment.