Dangerous Enrollment Permission on Authentication Certificate Templates
Cayosoft Threat Definition CTD-000150
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
Misconfigured permissions on Windows authentication certificate templates can enable attackers to request certificates for accounts they do not control — including Domain Admins.
If an unprivileged user can specify arbitrary subject names during enrollment, they can impersonate high-value targets and gain full network access.
- Severity: Critical
- Platform: Active Directory Certificate Services (ADCS)
- Category: Privileged Access Management
- MITRE ATT&CK Tactics: Privilege Escalation, Credential Access
- MITRE D3FEND Tactics: Network Traffic Analysis
Description
Active Directory Certificate Services (ADCS) allows organizations to issue digital certificates for authentication.
If a certificate template intended for authentication is misconfigured to grant Enroll or Autoenroll rights to overly broad groups such as Authenticated Users, Domain Users, or Domain Computers, attackers can abuse it to:
- Request a certificate for any account, including privileged ones.
- Authenticate to services as the impersonated account.
- Move laterally and escalate privileges without triggering password-based alerts.
Cayosoft Guardian detects and flags certificate templates with these risky permissions so administrators can secure them before they are exploited.

Real-World Scenario
A penetration tester discovers that a misconfigured authentication certificate template allows enrollment by any domain user.
They submit a certificate request with the subject name set to a Domain Admin account.
Once issued, the certificate is used to authenticate via Kerberos or NTLM without needing the account’s password.
Cayosoft Guardian would have detected the dangerous template and highlighted the exact permissions that made the attack possible.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) Search for CTD-000150 or Dangerous enrollment permission on authentication certificate templates.
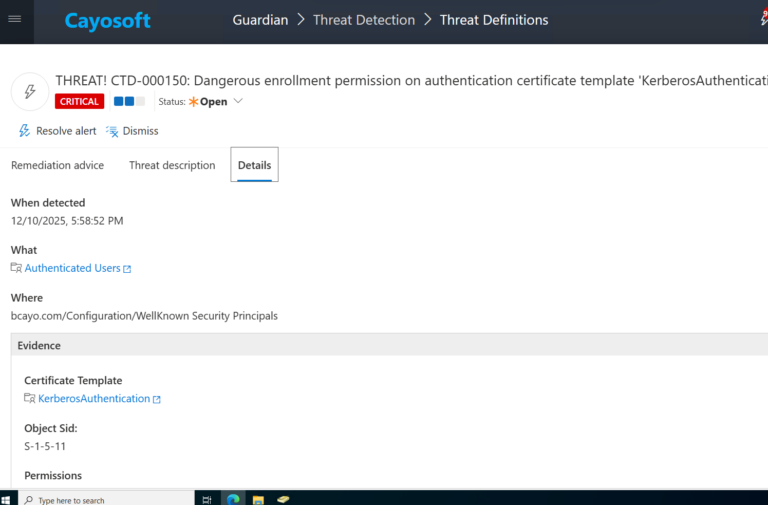
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review the evidence section to see the affected template and the associated dangerous permissions.
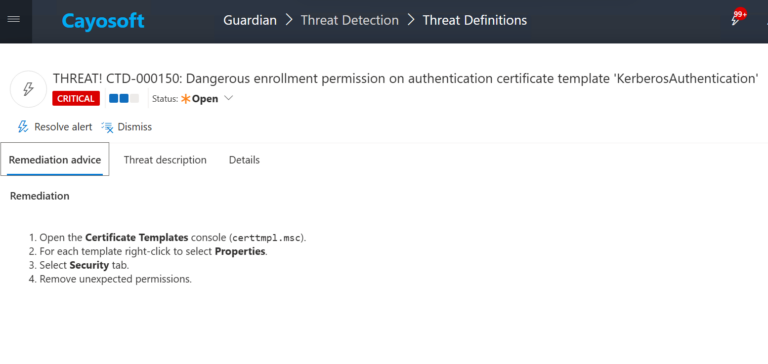
Remediation Steps
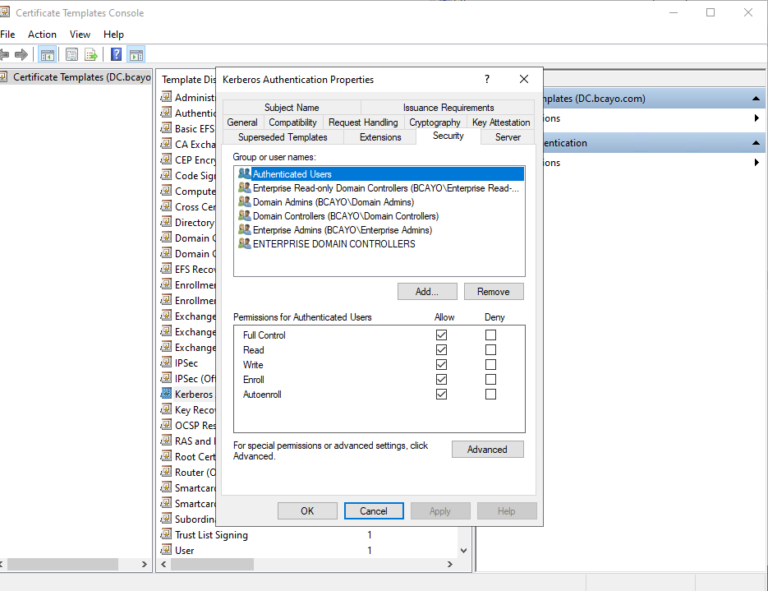
- ) Open the Certificate Templates console (
certtmpl.msc). - ) For each template right-click to select Properties.
- ) Select Security tab.
- ) Remove unexpected permissions.
How to Prevent It
- Access Control: Limit certificate template permissions to only the required administrative or service accounts.
- Regular Auditing: Periodically review ADCS permissions to ensure no unintended groups have enrollment rights.
- Security Enhancements: Require multi-step approval for sensitive certificate issuance.
FAQ
When an authentication certificate template grants Enroll or Autoenroll rights to broad security groups such as Authenticated Users or Domain Users, any unprivileged user can request certificates on behalf of other accounts. If the template also allows specifying arbitrary subject names, an attacker can request a certificate for a Domain Admin or service account. The resulting certificate can then be used to authenticate through Kerberos, NTLM, or LDAP over SSL — effectively granting the attacker high-privilege access without needing passwords or triggering MFA.
A template is considered dangerous when:
The Security tab lists permissive groups (e.g., Domain Users, Authenticated Users, Domain Computers) with Enroll or Autoenroll permissions.
The Subject Name field is configured to be supplied by the requester, allowing arbitrary identity impersonation.
The template is intended for Client Authentication, Smart Card Logon, or similar authentication purposes.
Cayosoft Guardian automatically identifies and highlights such templates, helping administrators pinpoint and fix the misconfiguration before it is weaponized.
Administrators should regularly audit all templates in the Certificate Templates console (certtmpl.msc) and verify that only authorized accounts — typically certificate administrators or specific service accounts — have enrollment rights. Remove overly broad groups, restrict subject name supply options, and enforce Manager Approval or Authorized Signatures where appropriate. In high-security environments, implement monitoring tools such as Cayosoft Guardian or Microsoft Defender for Identity to detect and alert on suspicious certificate requests or abnormal enrollment patterns.
Yes. Cayosoft Guardian Protector provides free detection and alerting for misconfigured certificate templates that pose high-risk privilege escalation paths.
Yes. Cayosoft Guardian delivers continuous monitoring, alerting, full auditing, and prescriptive remediation for ADCS risks along with more than 200 Active Directory, Entra ID, and Microsoft 365 configuration vulnerabilities.
References
- Microsoft – Active Directory Certificate Services Best Practices
- SpecterOps – Certified Pre-Owned: Abusing Active Directory Certificate Services
Final Thought
A single misconfigured certificate template can hand over the keys to your kingdom.
Tight permission controls and continuous monitoring are essential to keeping ADCS from becoming your environment’s biggest backdoor.