AD User with Identical Passwords
Cayosoft Threat Definition CTD-000181
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
When multiple Active Directory accounts share the same password, compromising one account often means compromising all of them.
This dramatically increases the likelihood of lateral movement — attackers can easily access additional accounts without cracking new credentials.
- Severity: Critical
- Platform: Active Directory
- Category: Account Protection
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: D3-PR (Password Rotation)
Description
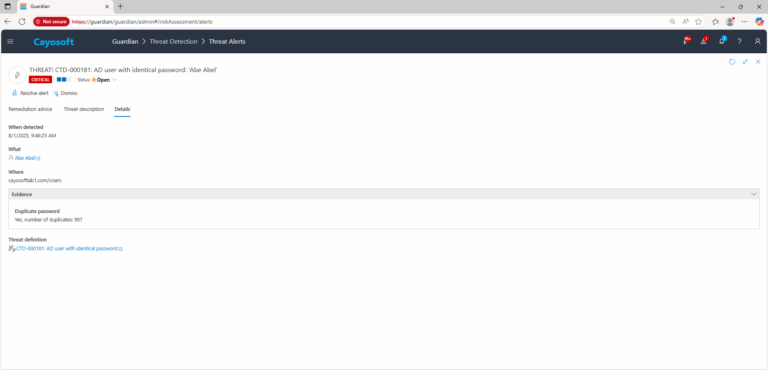
Duplicate passwords in AD create a single point of failure.
If an attacker obtains the credentials for one account, they can log in to all other accounts using the same password.
This often bypasses role-based access restrictions and can enable privilege escalation.
Cayosoft Guardian detects identical passwords by comparing password hashes locally on your domain controllers.
Specific user account names with duplicate passwords are not exposed in alerts to protect sensitive information.
All detection operations occur entirely within your environment — password hashes never leave your domain controllers, are not transmitted to the internet, and are not stored externally.

Real-World Scenario
Two separate AD accounts — one user and one service — share the same password for convenience.
A phishing attack compromises the user account, and the attacker immediately uses those credentials to log into the service account, gaining access to critical application data.
Cayosoft Guardian would have detected the shared password before the breach, allowing administrators to enforce unique credentials.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian Audit & Restore
Real-time alerts across AD & Entra ID with one-click rollback.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
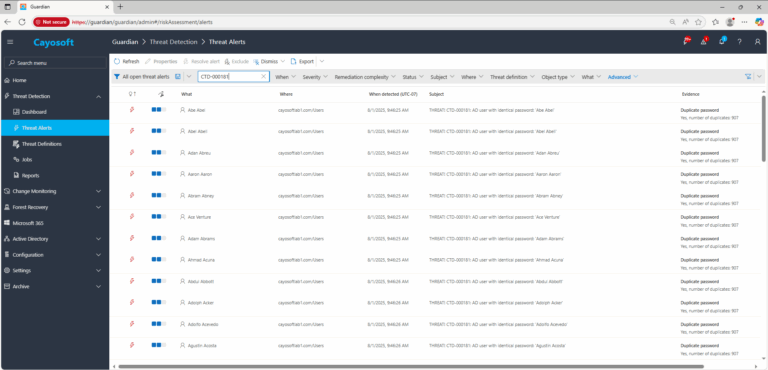
2.) View All Alerts and search for CTD-000181 or AD user with identical password.
3.) Open any alert and Click for details (from Raise Threat Alert action).
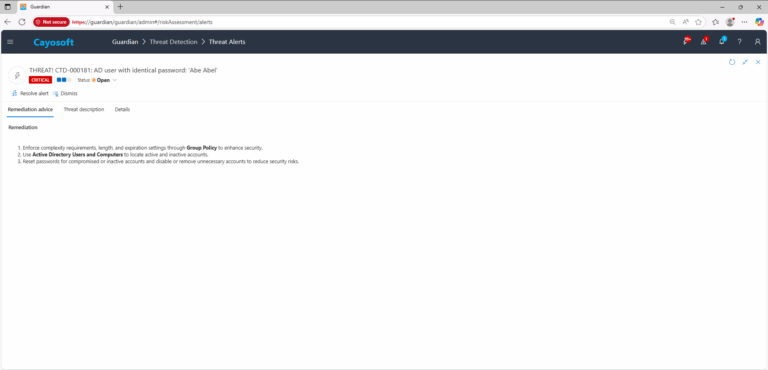
Remediation Steps
- ) Notify and contact user and inform them of the password vulnerability and have them either manually reset the password or use following steps
- ) Enforce complexity requirements, length, and expiration settings through Group Policy to enhance security.
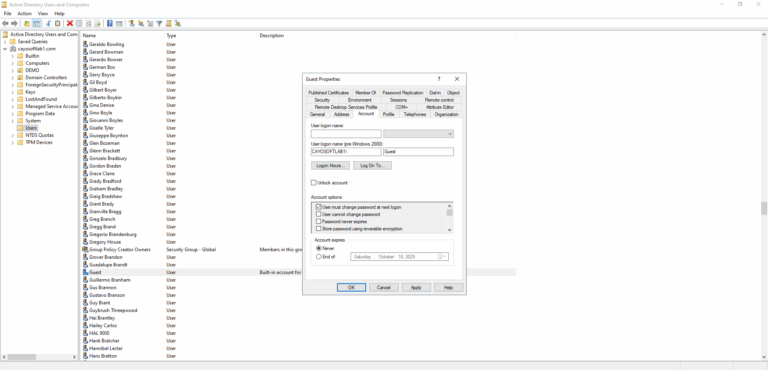
- ) Use Active Directory Users and Computers to locate active and inactive accounts.
- ) Reset passwords for compromised or inactive accounts and disable or remove unnecessary accounts to reduce security risks.
How to Prevent It
Technical Controls:
- Enable Fine-Grained Password Policies to enforce unique passwords per account.
- Implement Privileged Access Workstations (PAWs) for admin credentials.
Operational Controls:
- Include password uniqueness checks in regular AD security audits.
- Use Cayosoft Guardian’s ongoing duplicate password detection to prevent recurrence.
FAQ
Even low-privilege accounts can be used in credential-stuffing or privilege-escalation attacks, especially if they have access to shared resources.
No. All password hash comparisons occur locally on your domain controllers; no data leaves your secure environment.
References
- Microsoft – Password Policy Best Practices
Final Thought
In security, shared passwords are shared vulnerabilities. Enforcing unique, strong credentials for every account is one of the simplest ways to block lateral movement and contain breaches before they spread.