Privileged AD user not protected against delegation
Cayosoft Threat Definition CTD-000135
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A threat actor controlling a delegated account can perform actions on other services or systems, potentially escalating their privileges.
- Severity: High
- Platform: Active Directory
- Category: Account protection
- MITRE ATT&CK Tactics: Initial Access, Privilege Escalation Access
- MITRE D3FEND Tactics: Application Configuration Hardening, Domain Account Monitoring
Description
Privileged accounts (members of administrator groups) must not be trusted for delegation. If a privileged AD user is not marked Account is sensitive and cannot be delegated, an attacker who compromises that user can leverage Kerberos delegation paths for lateral movement and elevation.
Note: In Active Directory, privileged users are commonly identified by adminCount=1 protection.

Real-World Scenario
A helpdesk admin is added to Domain Admins during an outage and later removed, but the account remains usable and is not protected against delegation. An attacker phishes the helpdesk admin’s credentials, authenticates to a tier-0 service that performs Kerberos delegation, and impersonates higher-privilege services to access sensitive systems. The move blends with normal SSO traffic and avoids obvious alerts. Cayosoft Guardian would surface CTD-000135 before the delegation path is abused.
Stop Privilege Escalation—Then Undo It with Cayosoft Guardian
Real-time alerts across AD & Entra ID with one-click rollback.
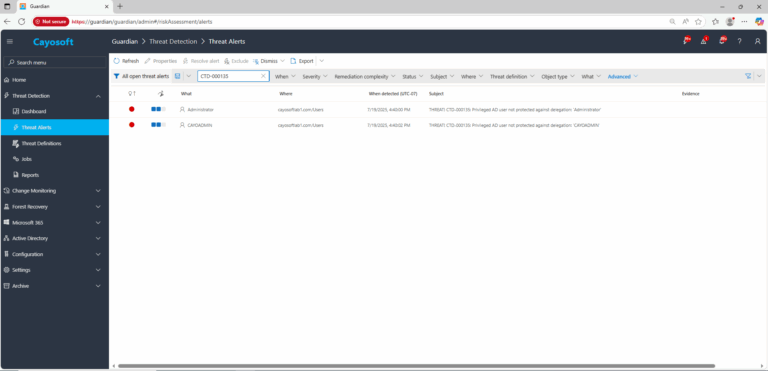
2.) Open All Alerts and search for CTD-000135 or “Privileged AD user not protected against delegation.”
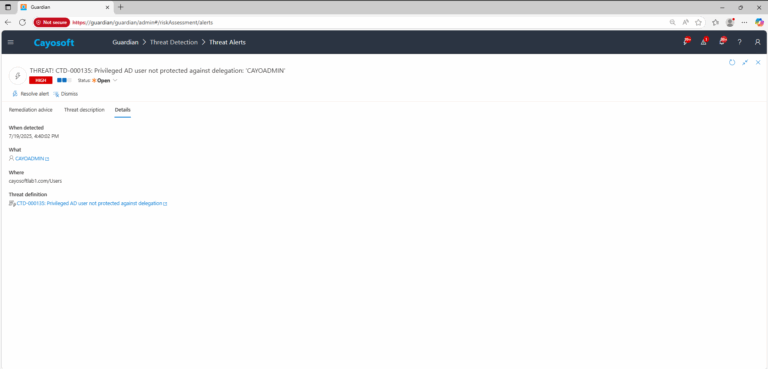
3.) Open any alert and Click for details (from Raise Threat Alert action).
4.) Review affected users; confirm whether the Account is sensitive and cannot be delegated option is disabled on those privileged accounts.
Remediation Steps
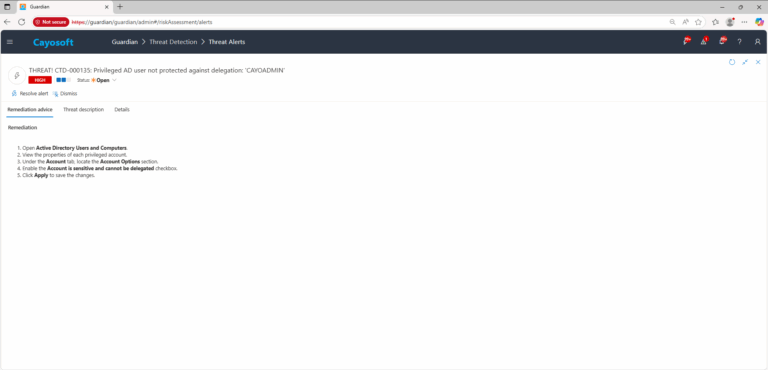
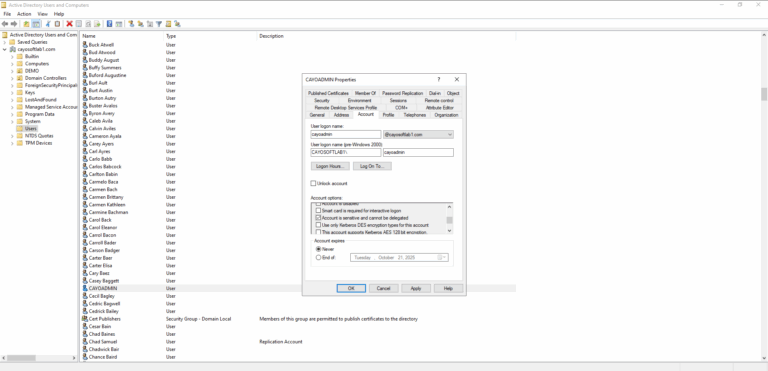
- ) Open Active Directory Users and Computers.
- ) View the properties of each privileged account.
- ) Under the Account tab, locate the Account Options section.
- ) Enable the Account is sensitive and cannot be delegated checkbox.
- ) Click Apply to save the changes.
How to Prevent It
Cayosoft Guardian can proactively detect and alert on Privileged AD user not protected aganst delegation. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warning before attackers can exploit them.
FAQ
Without this restriction, an attacker who compromises the account can exploit Kerberos delegation to impersonate higher-privilege services and users, effectively bypassing standard access controls.
Under normal use, delegation simplifies access to services in a trusted model. In compromise scenarios, however, an attacker can “chain” through infrastructure, escalate privileges, and impersonate critical services, leading directly to domain compromise.
Privileged accounts should never be trusted for delegation. For such scenarios, create dedicated service accounts with minimal rights and configure constrained delegation instead.
Final Thought
Proactive monitoring and timely remediation of configuration risks is essential to maintaining a secure Active Directory and Microsoft 365 environment. By addressing issues like Privileged AD user not protected against delegation, you reduce attack surfaces and strengthen your organization’s overall security posture.