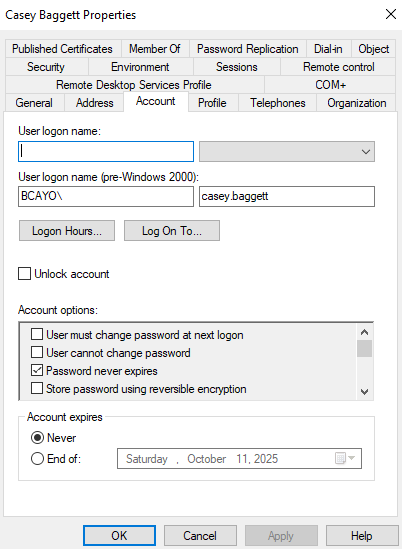
AD Domain Account’s Password Set to Never Expire
Cayosoft Threat Definition CTD-000001
Stop AD Threats As They Happen
Cayosoft Protector provides continuous monitoring and real-time alerts across your entire Microsoft Identity stack
Like This Article?
Subscribe to our LinkedIn Newsletter to receive more educational content
Risk Summary
A non-expiring password allows indefinite credential reuse, enabling attackers to maintain unauthorized access for long periods without detection. This increases the risk of credential-based attacks and persistence in your Active Directory environment.
- Severity: Medium
- Platform: Active Directory
- Category: Account Protection
- MITRE ATT&CK Tactics: Credential Access
- MITRE D3FEND Tactics: Credential Rotation
Description
A user account whose password never expires poses a threat to your Active Directory security posture. Password rotation reduces the risk and effectiveness of password-based attacks by shortening the time window in which stolen credentials can be used. A threat actor with a compromised password can maintain access until the password is changed.
Note: Cayosoft Guardian defines privileged users as those with adminCount=1, a built-in Active Directory attribute designed to protect members of administrative groups (Microsoft documentation).
Security best practices recommend de-provisioning, not reusing, admin accounts. If an account with administrative permissions is retained, it could retain access to other resources even after removal from admin groups. Learn more about AdminSDHolder and SDProp.

Real-World Scenario
Be Audit-Ready Any Day with Cayosoft Guardian
Immutable logs and exportable reports for AD + Entra ID.
Detect this and other threats with Cayosoft Guardian Protector (Free of Charge)
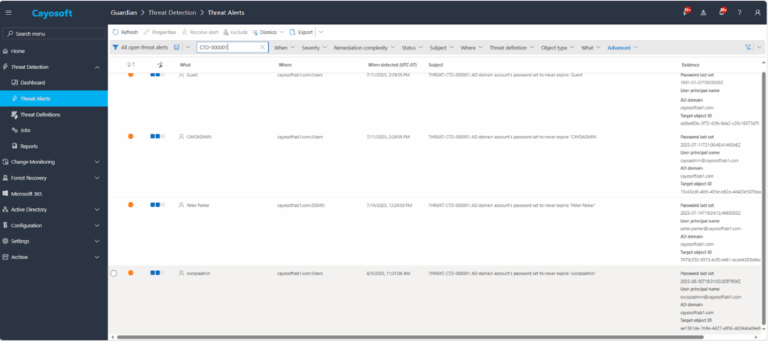
1.) Download Cayosoft Guardian Protector for free real-time threat detection and monitoring of your hybrid AD and Microsoft 365 environment. Once downloaded, sign in and navigate to the Threat Detection Dashboard.
2.) View All Alerts and search for CTD-000001 or AD domain account’s password set to never expire.
3.) Open any alert and Click for details (from Raise Threat Alert action).
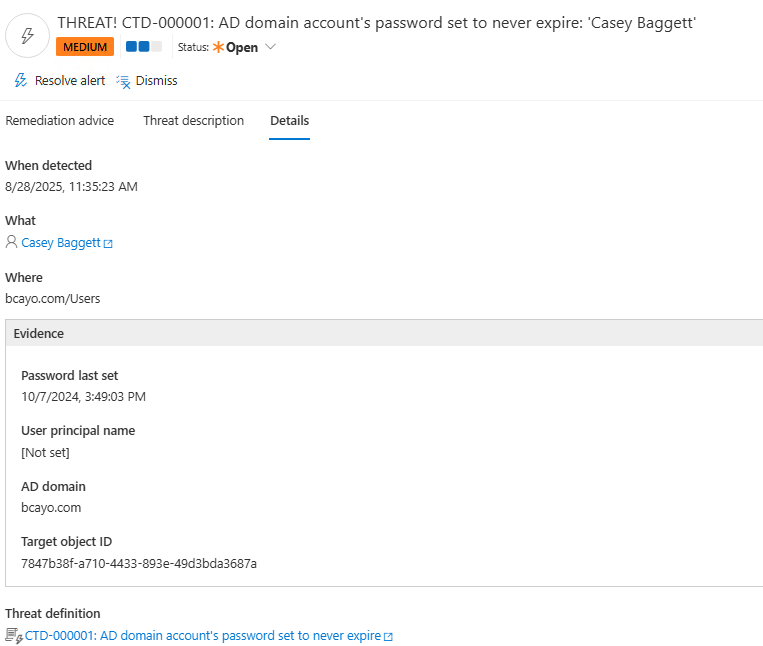
4.) Review Evidence:
- Password last set
- User principal name
- AD domain
- Target object ID
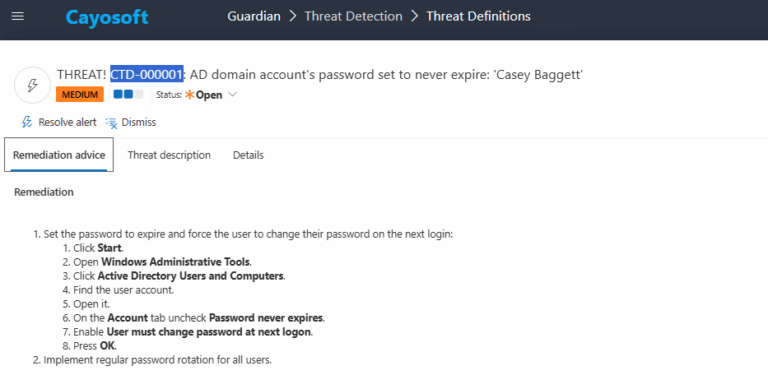
Remediation Steps
1.) Click Start.
2.) Open Windows Administrative Tools.
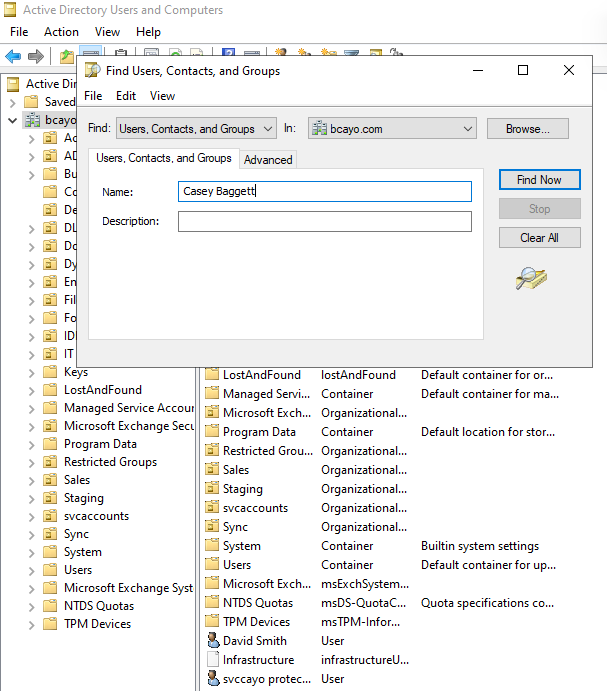
3.) Click Active Directory Users and Computers (ADUC).
4.) Locate the affected user account.
5.) Open account properties.
6.) On the Account tab, uncheck Password never expires.
Note: Performing this step on a service account will break the application until it is updated in windows service or wherever it was used.
7.) Enable User must change password at next logon.
8.) Click OK.
PowerShell (Optional)
PowerShell Disclaimer:
The following examples are for reference only. Test in a non-production environment and follow your organization’s change control policy. These commands are recommended only for experienced users with a solid understanding of Active Directory and PowerShell.
powershell
CopyEdit
# Disable 'Password Never Expires' for a specific user
Set-ADUser -Identity "<UserName>" -PasswordNeverExpires $false
# Audit users with 'Password Never Expires' enabled
Get-ADUser -Filter * -Properties PasswordNeverExpires |
Where-Object { $_.PasswordNeverExpires -eq $true } |
Select-Object SamAccountName
How to Prevent It
Cayosoft Guardian can proactively detect and alert on AD accounts with passwords set to never expire. It continuously monitors Active Directory, Entra ID, Microsoft 365, and Intune for over 200 misconfigurations, providing early warnings before attackers can exploit them.
FAQ
Stolen credentials can be used indefinitely, allowing attackers to maintain persistent access.
It marks accounts as protected administrative accounts, applying special permission handling (Microsoft reference).
Accounts under AdminSDHolder protection retain special permissions, which can allow persistent access even after removal from admin groups (Microsoft Community Hub).